
What is a Zero Day?
In the world of cyberattacks, a zero day is the day when a vulnerability is discovered before the vendor has become aware of it. On the zero day, no patch exists, so threat actors can easily exploit the vulnerability knowing that no protections are in place. This makes zero-day vulnerabilities a severe security threat. After a few days, the vendor releases a patch for the vulnerability, an assessment report is published, and a CVE number is assigned.
We are a CVE Numbering Authority (CNA)
Securin is a US Department of Homeland Security sponsored CVE Numbering Authority (CNA). We play a critical role in the global effort to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.
Our innovation in vulnerability and exploit research has led us to discover 56 zero days in popular products such as Oracle, D-Link, WSO2, Thembay, and Zoho.

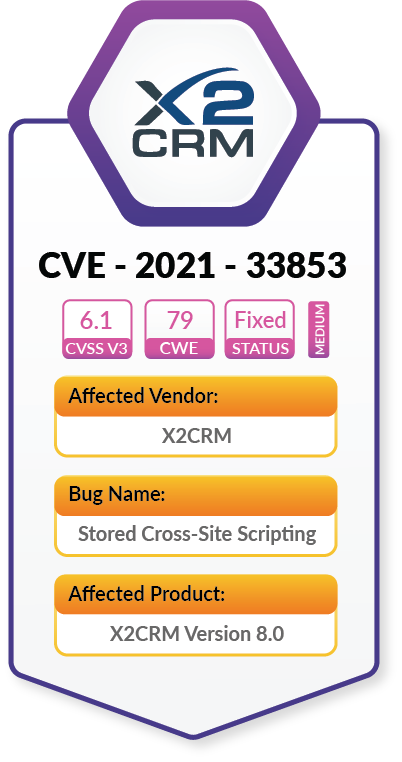
Latest Zero Days
Common Vulnerability & Exposure (CVE)
A Common Vulnerability and Exposure (CVE) is an alphanumeric ID assigned by the CVE Numbering Authority (CNA) to refer to a specific software or hardware vulnerability. Once the vulnerability is identified and analyzed, it is listed publicly in MITRE. Then, the information is updated to the National Vulnerability Database (NVD).
Common Weakness Enumeration (CWE)
Common Weakness Enumeration (CWE) is a global categorization system of weakness found in software and hardware vulnerabilities. Over 600 types of vulnerabilities are available in the source, which is maintained by MITRE corporation and sponsored by National Cybersecurity FFRDC. This process provides the users an understanding of the issues in their software and helps in the development of automated tools to identify, fix, and prevent these issues.
Each of the CWE is classified with an ID and description that gives an overview of the vulnerability type. Some of the categorized vulnerabilities are buffer overflows, path/directory tree traversal errors, cross-site scripting, privilege escalation, and SQL injection.
Common Vulnerability Scoring System (CVSS)
Common Vulnerability Scoring System (CVSS) is a standard scoring scale of 0–10, which determines the severity and impact of prioritizing vulnerabilities. Vendors release patches and updates for vulnerabilities based on the given CVSS score. The most recent version is CVSS 3.1. The following table presents its breakdown.
| Rating | CVSS V3 Score |
|---|---|
| Critical | 9.0 – 10 |
| High | 7.0 – 8.9 |
| Medium | 4.0 – 6.9 |
| Low | 0.1 – 3.9 |
Common Vulnerability & Exposure (CVE)
A Common Vulnerability and Exposure (CVE) is an alphanumeric ID assigned by the CVE Numbering Authority (CNA) to refer to a specific software or hardware vulnerability. Once the vulnerability is identified and analyzed, it is listed publicly in MITRE. Then, the information is updated to the National Vulnerability Database (NVD).

Common Weakness Enumeration (CWE)
Common Weakness Enumeration (CWE) is a global categorization system of weakness found in software and hardware vulnerabilities. Over 600 types of vulnerabilities are available in the source, which is maintained by MITRE corporation and sponsored by National Cybersecurity FFRDC. This process provides the users an understanding of the issues in their software and helps in the development of automated tools to identify, fix, and prevent these issues.
Each of the CWE is classified with an ID and description that gives an overview of the vulnerability type. Some of the categorized vulnerabilities are buffer overflows, path/directory tree traversal errors, cross-site scripting, privilege escalation, and SQL injection.
Common Vulnerability Scoring System (CVSS)
Common Vulnerability Scoring System (CVSS) is a standard scoring scale of 0–10, which determines the severity and impact of prioritizing vulnerabilities. Vendors release patches and updates for vulnerabilities based on the given CVSS score. The most recent version is CVSS 3.1. The following table presents its breakdown.
| Rating | CVSS V3 Score |
|---|---|
| Critical | 9.0 – 10 |
| High | 7.0 – 8.9 |
| Medium | 4.0 – 6.9 |
| Low | 0.1 – 3.9 |


