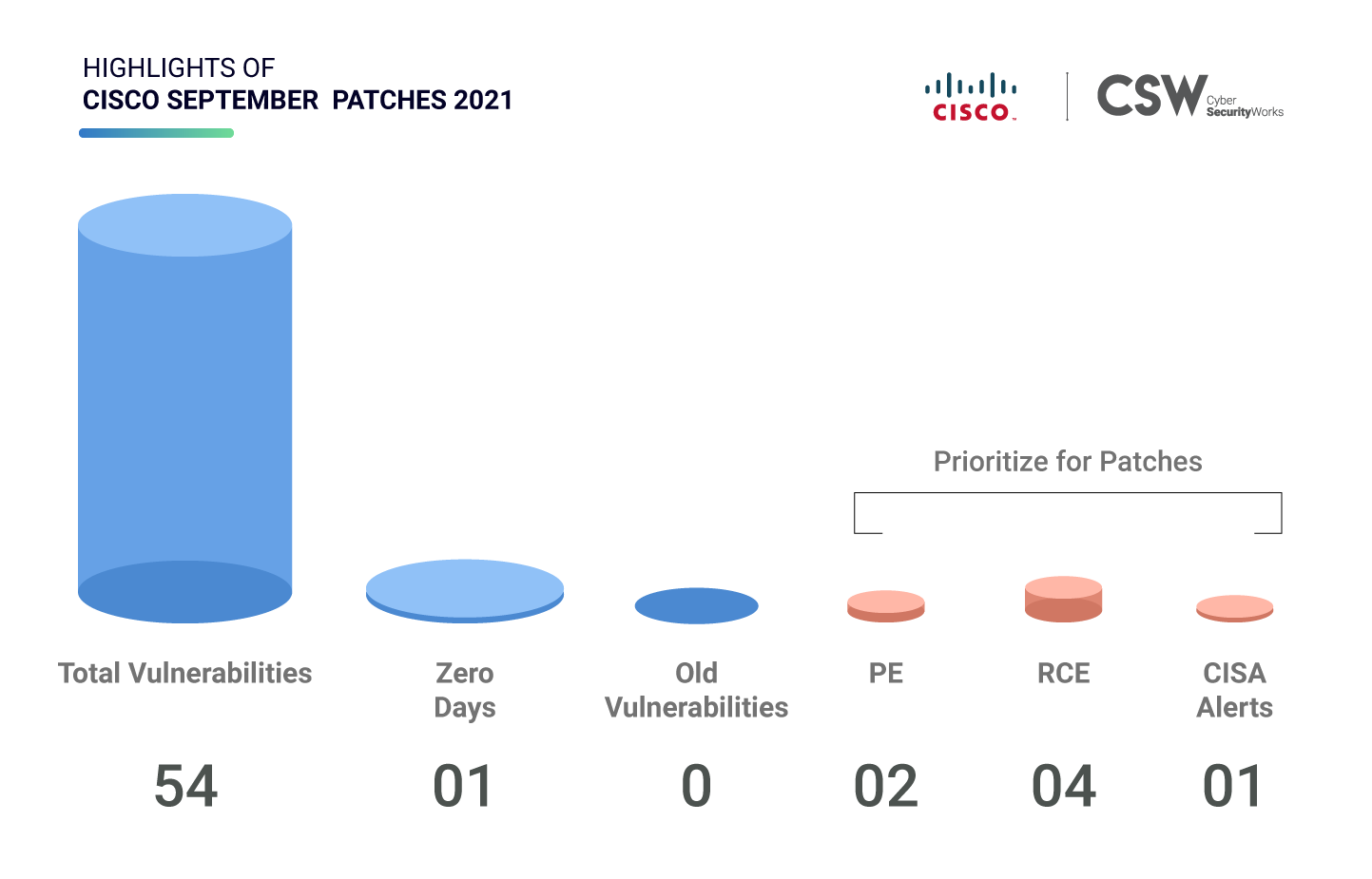
Cisco Systems had released security patches to address 54 unique vulnerabilities in September, ranging in importance from critical, high, and medium severity. We analyzed these weaknesses and spotlighted the most important vulnerabilities that ought to be fixed on priority.
An Analysis of Cisco September Patched Vulnerabilities
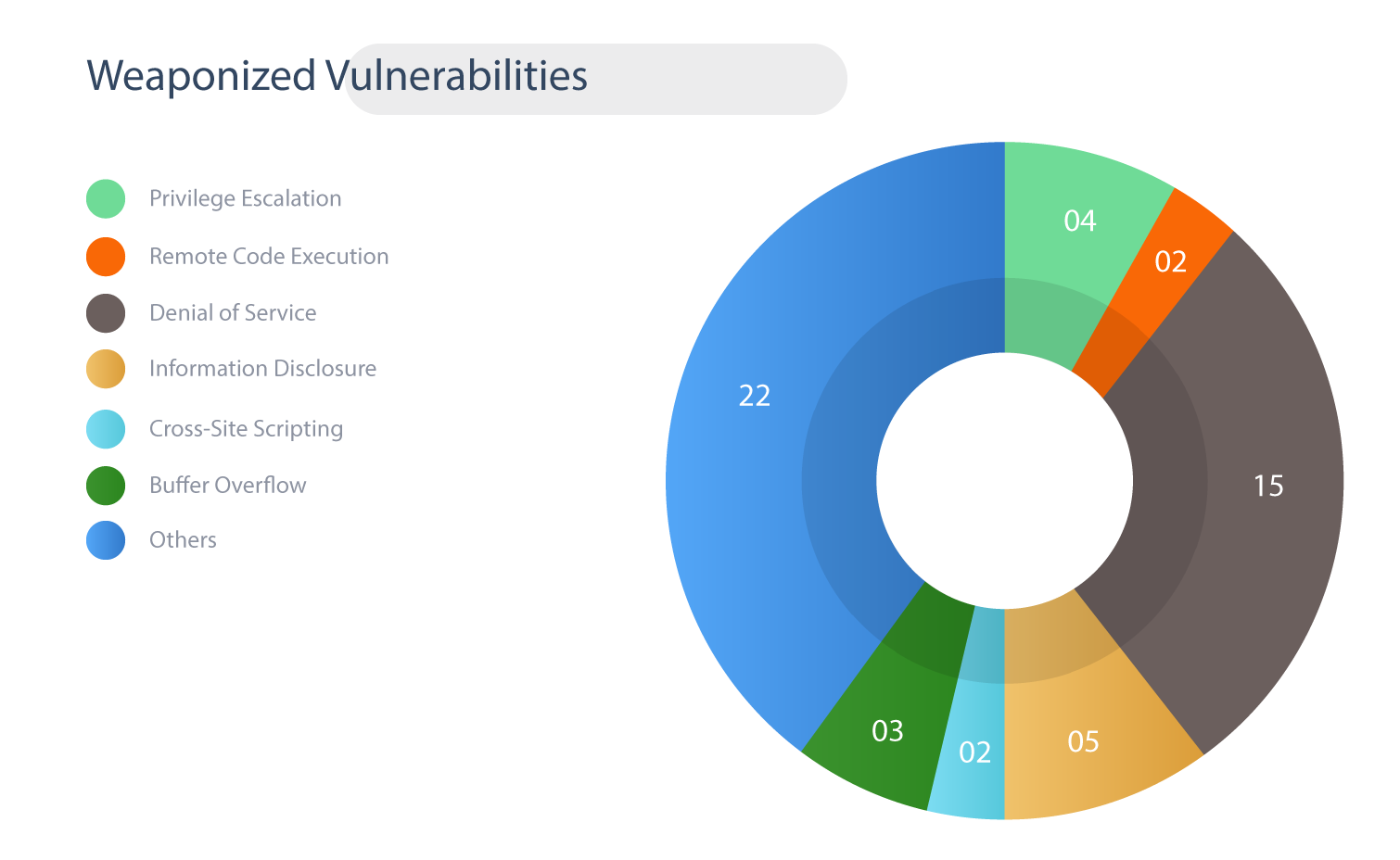
The 54 vulnerabilities that were patched in September include –
-
2 CVEs classified as Remote Code Execution bugs
-
4 CVEs have Privilege Escalation capabilities
-
15 CVEs with Denial of Service
-
5 CVEs are Information Disclosure
-
2 CVEs are linked to Cross-Site Scripting.
Among these patched vulnerabilities, CVE-2021-34746 is found to be publicly disclosed.
Zero Days
Cisco disclosed a zero-day bug that received a security update this September.
The security issue tracked as CVE-2021-34746 affects Terminal Access Controller Access-Control System Plus (TACACS+) authentication, authorization, and accounting (AAA) of Cisco’s Enterprise NFV Infrastructure Software, a solution designed to aid Virtualization Network Services so that VFNs are managed easily.
CVE-2021-34746 is caused by insufficient validation of user-supplied input given to an authentication script during the sign-in process. It allows unauthenticated, remote attackers to log in as an administrator on an unpatched device.
This CVE has a CVSS score of 9.8 (critical) and is categorized under CWE-289 (Authentication Bypass by Alternate Name).
A patch is now available for this authentication bypass vulnerability that was fixed in Cisco Enterprise NFVIS releases 4.6.1 and later.
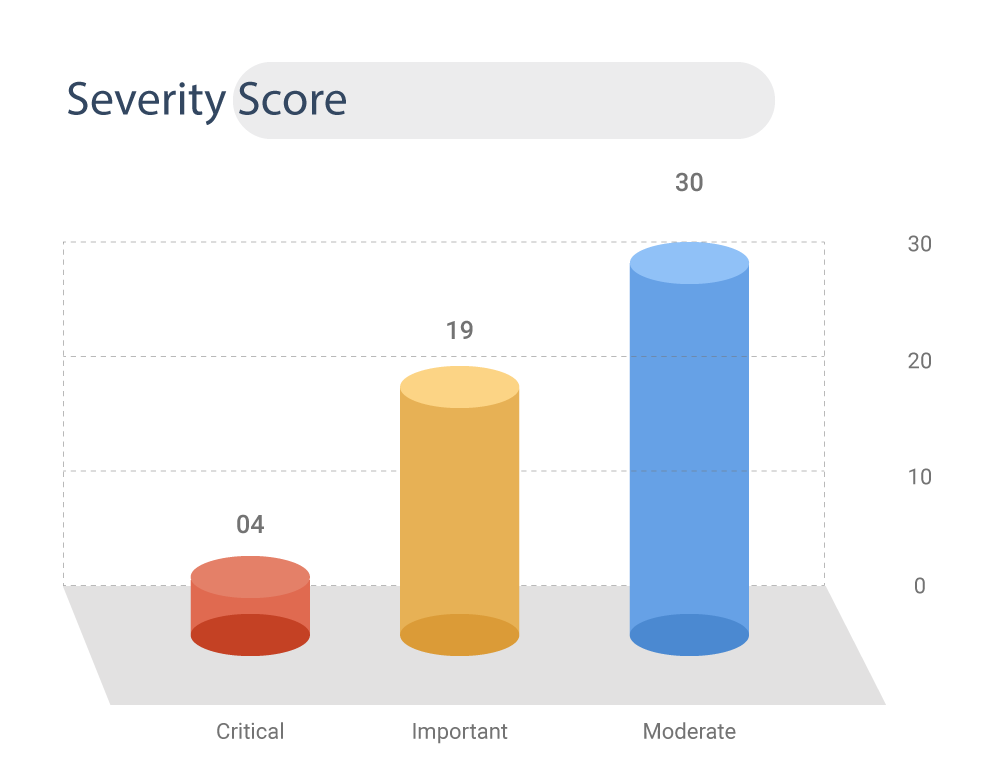
Severity Scores
CWE Analysis
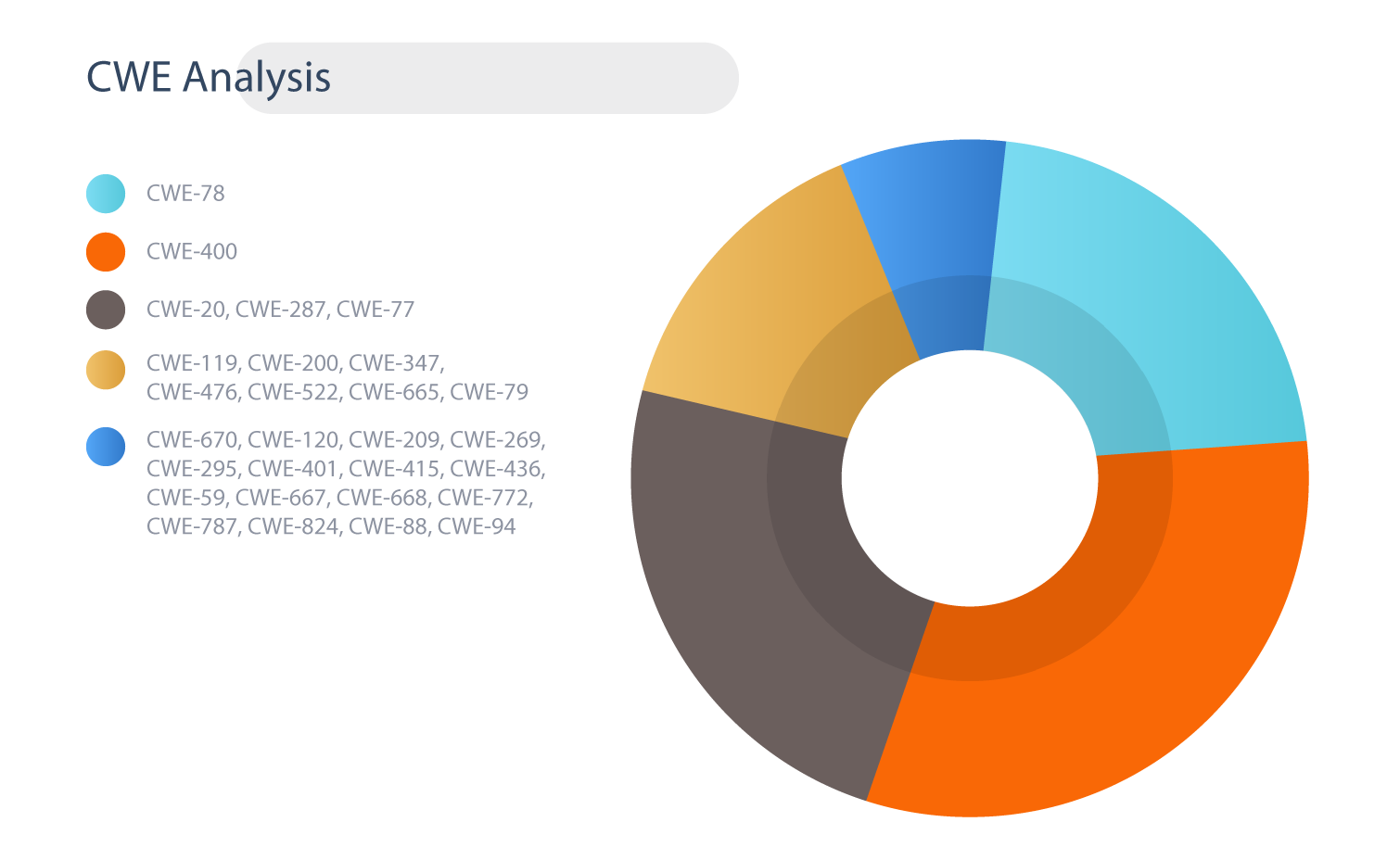
Table: Cisco September Patches 2021
CISA Alerts
CISA had issued a notice, urging IT teams to update a Cisco system that has a critical vulnerability. Therefore, patching this CVE-2021-34746 vulnerability should be top priority.
To reduce the chance of information security breaches, patching is essential for safeguarding systems and data. We request all Cisco users to beware of newly disclosed vulnerabilities and urge them to implement updates as quickly as possible.
Does your organization have a patch management program? Talk to CSW’s Experts to prioritize the threats that need immediate attention!









