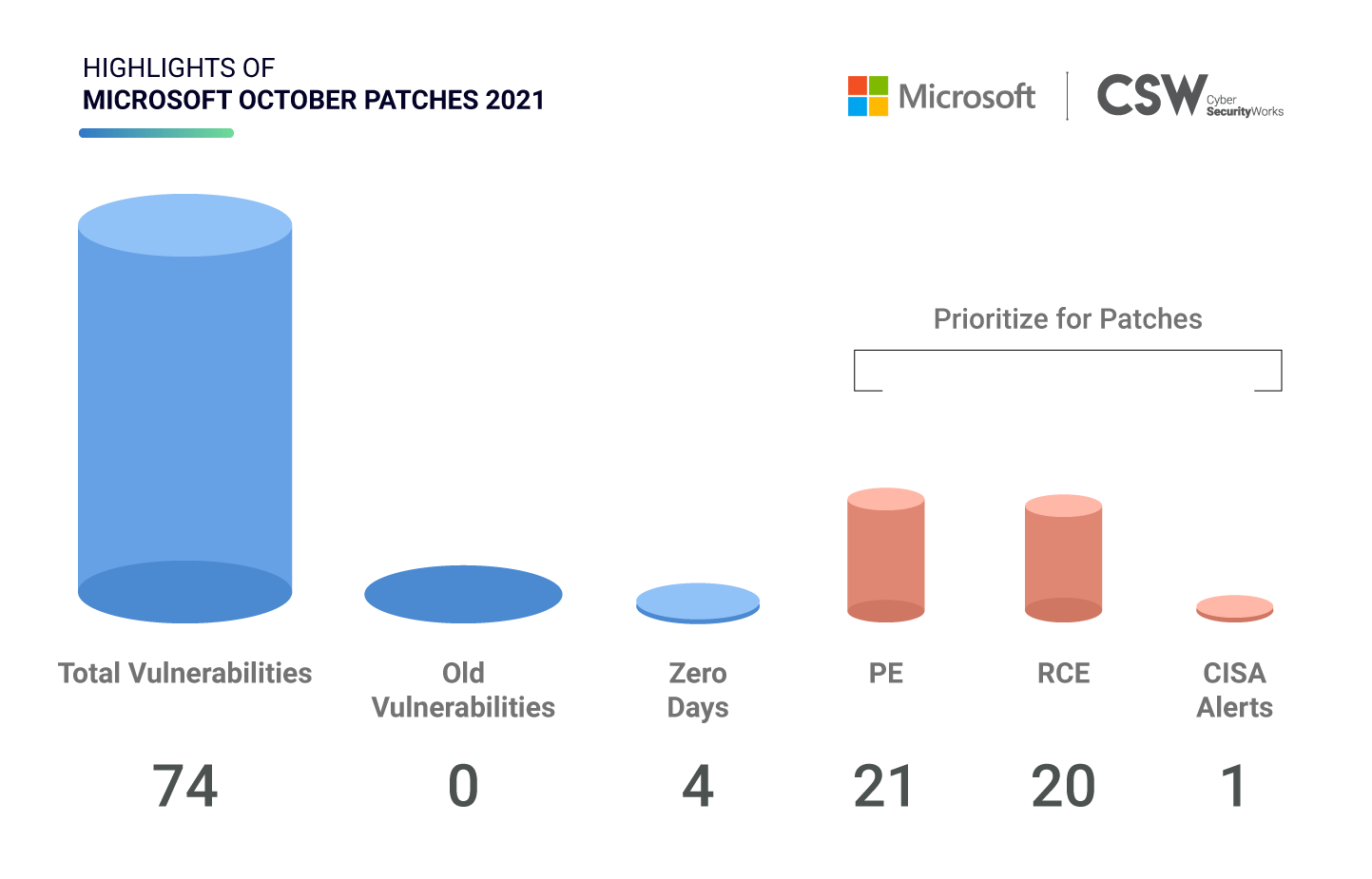
Microsoft patched 74 unique security vulnerabilities in October 2021, which includes four zero-day exploits. We analyzed these weaknesses and spotlighted the most important vulnerabilities that ought to be fixed on priority.
Microsoft Patches: Overview
This October, Microsoft patched 74 vulnerabilities discovered in 2021.
-
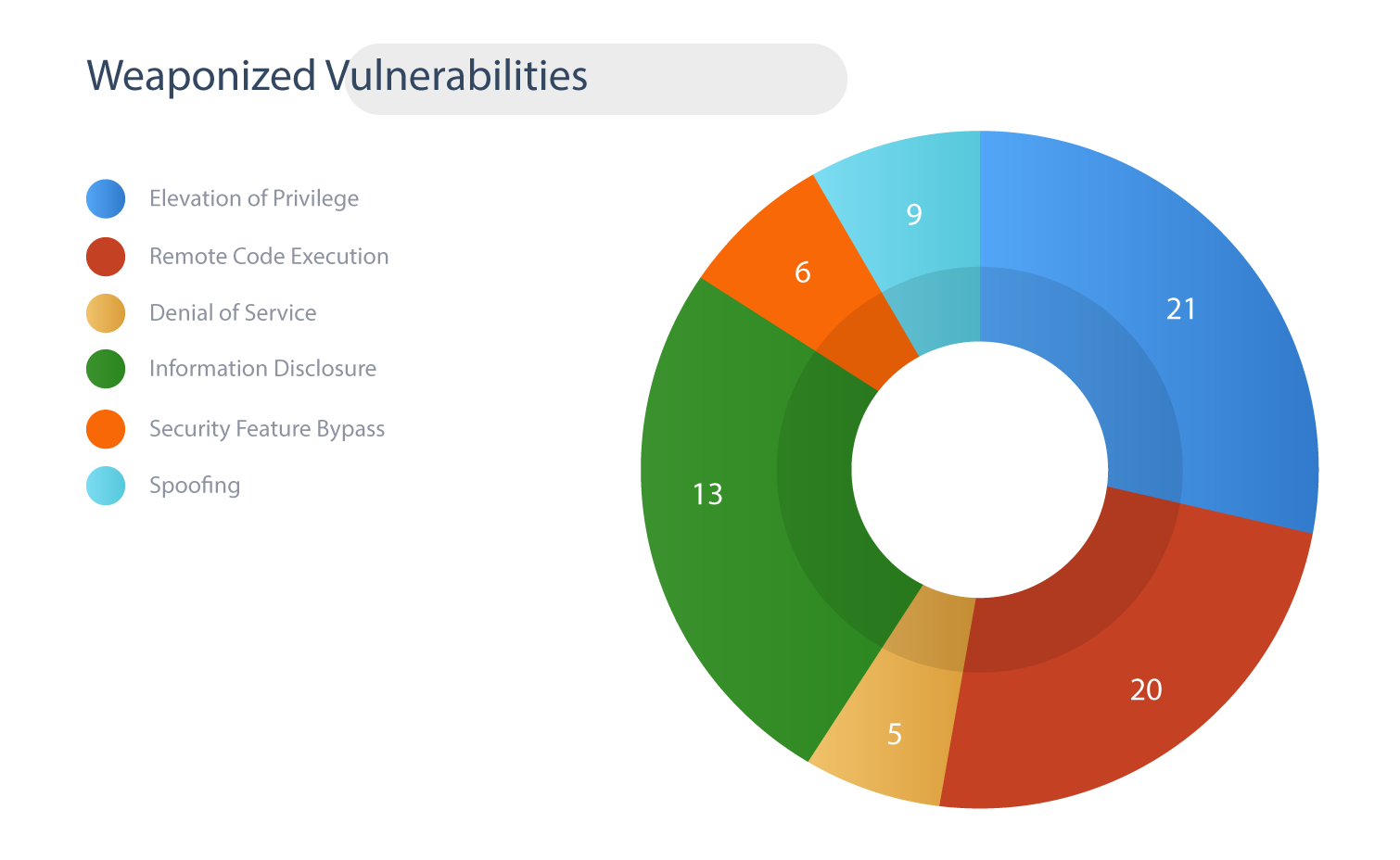
20 CVEs are classified as Remote Code Execution bugs
-
21 CVEs with Privilege Escalation capabilities
-
13 CVEs are linked to Information Disclosure
-
5 CVEs have Denial of Service capabilities
-
9 CVEs has Spoofing possibilities
-
6 CVEs are Security Bypass bugs
Three of the CVEs CVE-2021-40469, CVE-2021-41335, and CVE-2021-41338 have been disclosed publicly, though haven’t been observed in active exploitation.
Zero-days
Microsoft had released patches for four zero-day vulnerabilities this month:
-
CVE-2021-40449 – Win32K kernel driver
-
CVE-2021-40469 – Windows DNS Server
-
CVE-2021-41335 – Windows Kernel
-
CVE-2021-41338 – Windows AppContainer Firewall Rules
CVE-2021-40449 is an elevation of privilege vulnerability in the Win32k Kernel driver known to have been actively exploited in attacks. According to researchers, Chinese hacking groups are leveraging this vulnerability to launch espionage campaigns. As part of the intrusions, the threat actors deploy a remote access trojan (RAT) that is elevated with authorized rights to exploit this Windows vulnerability. This cluster of malicious activity is dubbed as MysterSnail by Kaspersky and is linked to the Chinese-speaking APT group, IronHusky.
RCE/PE
Microsoft has patched a remote code execution (RCE) vulnerability in Exchange Server (CVE-2021-26427) that was disclosed by the National Security Agency (NSA). An attacker would need direct network access to an Exchange Server to exploit this weakness, therefore it isn’t easily accessible via the Internet. However, because email servers are constantly attacked, it’s a good idea to fix your Exchange Servers as soon as possible. This CVE received a CVSS score of 9.0, the highest rated vulnerability of this month’s patch release.
Additional Fix for PrintNightmare
Another important spoofing vulnerability (CVE-2021-36970), reported as “more likely to be exploited” in the Windows Print Spooler, got a CVSSv3 score of 8.8 (high). This flaw necessitates an attacker to have access to the same network as the target, as well as user interaction.
The PrintNightmare and Exchange Server bugs are worth keeping an eye on as they are more interested by the threat actors for exploiting.
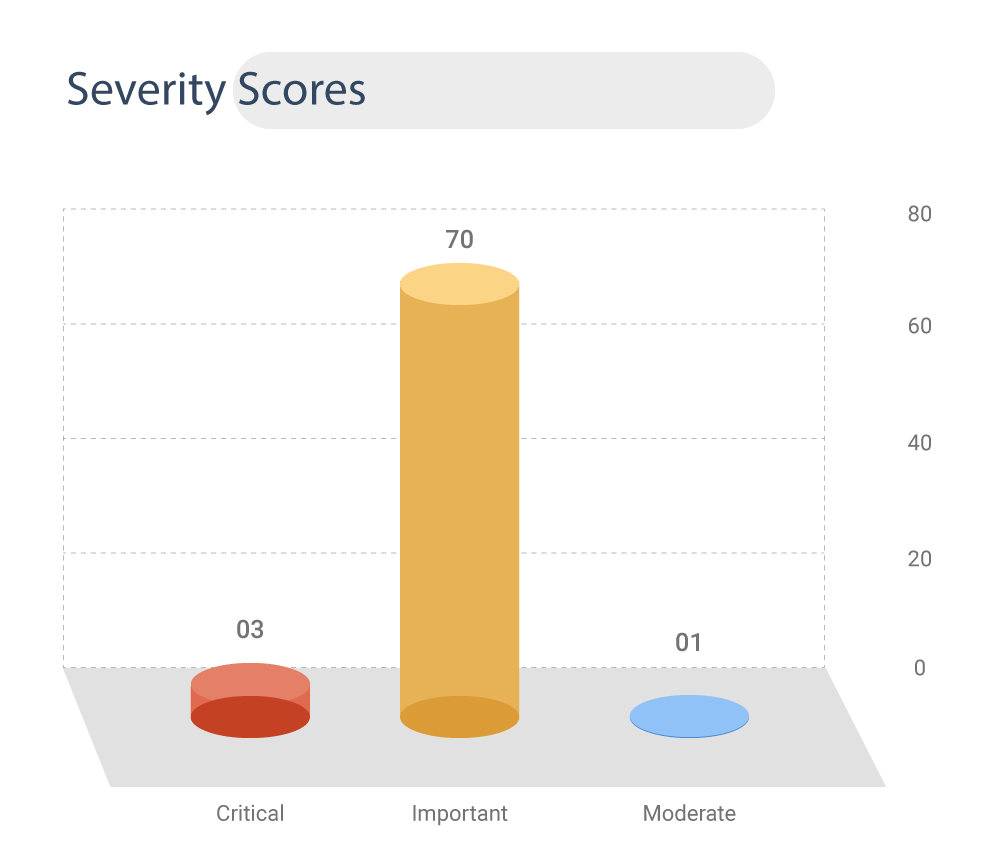
Severity Scores
Of these 74 vulnerabilities, three CVEs have been marked critical. All the critical CVEs are classified as Remote Code Execution bugs.
Product Analysis
The products impacted in the October patch bundle include Windows, Microsoft Office, Exchange Server, MSHTML, Visual Studio, and the Edge browser. Windows products received a fix for 45 vulnerabilities in which 9 CVEs accounted for Remote Code Execution, 20 for Privilege Escalation possibilities. There are 15 vulnerabilities fixed in Microsoft Office that include 11 Remote Code Execution bugs.
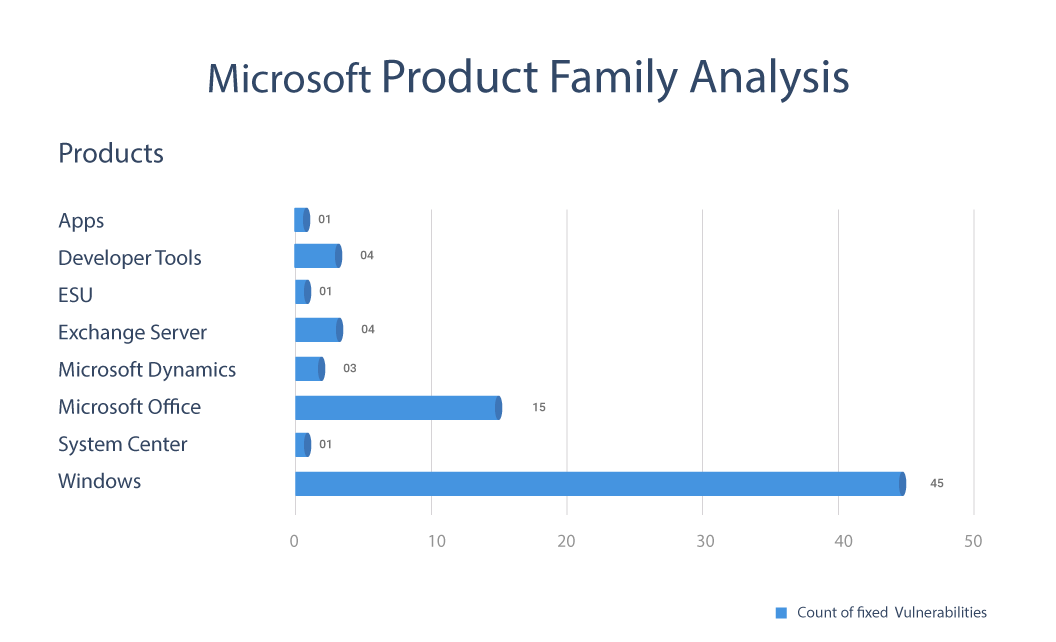
Table: Microsoft October Patches 2021
CISA has issued an advisory urging users to update these October released patches. We recommend users to patch systems as quickly as possible and monitor their environment on a regular basis to detect systems that have not been completely patched.









