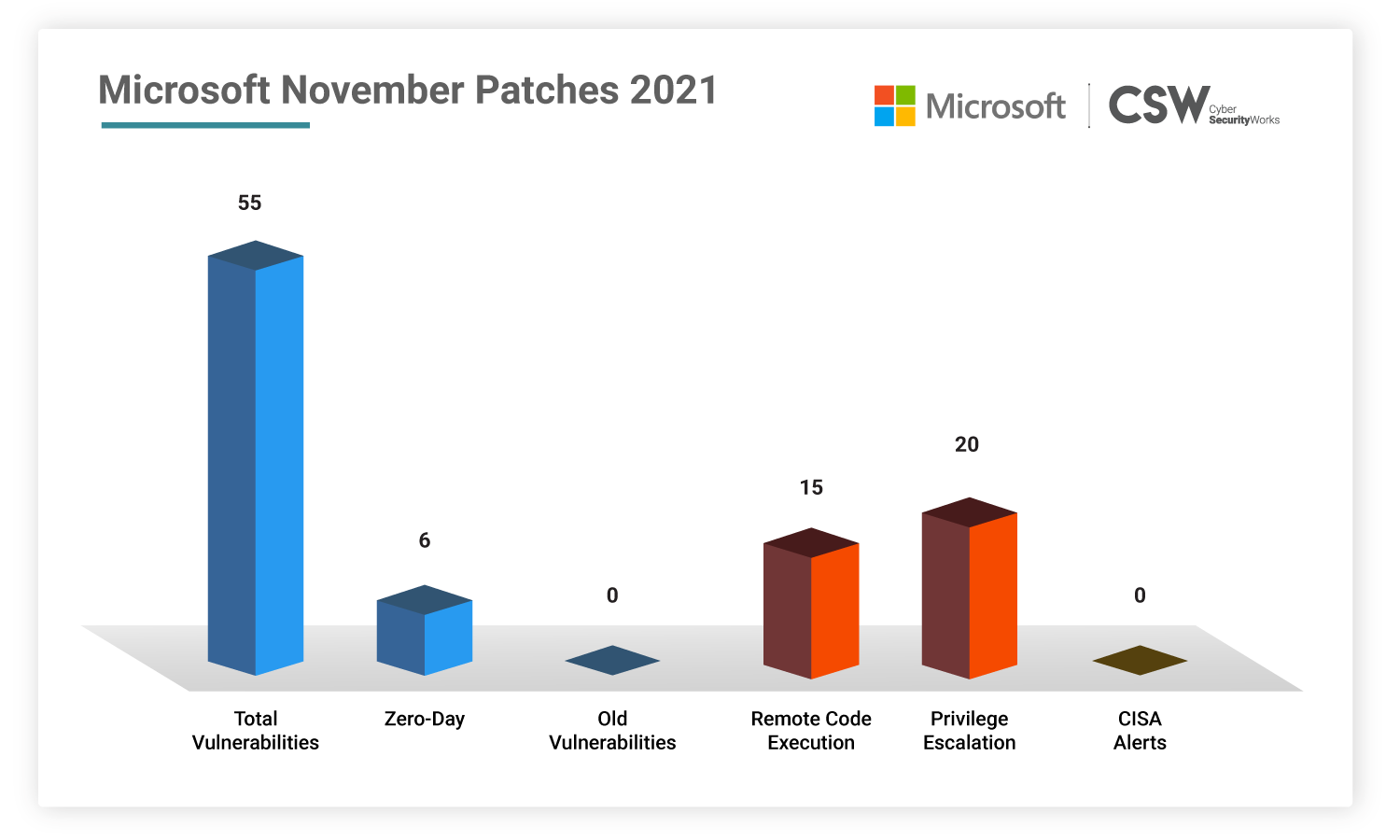
Microsoft patched 55 unique security vulnerabilities in November 2021, which includes six zero-day exploits. We analyzed these weaknesses and spotlighted the most important vulnerabilities that ought to be fixed on priority.
Microsoft Patches: Overview
This November, Microsoft patched 55 vulnerabilities discovered in 2021.
-
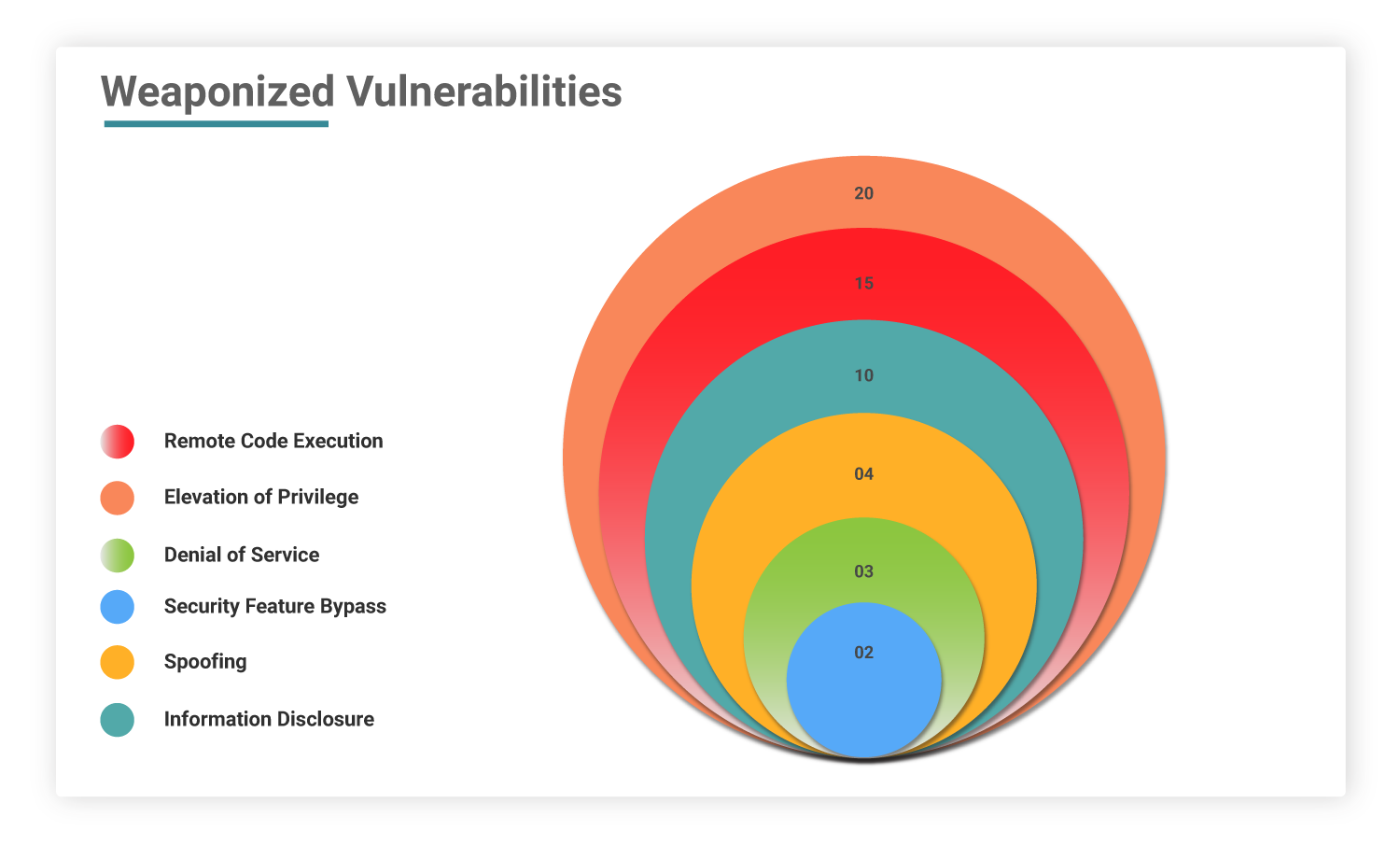
15 CVEs are classified as Remote Code Execution bugs
-
20 CVEs with Privilege Escalation capabilities
-
10 CVEs are linked to Information Disclosure
-
3 CVEs have Denial of Service capabilities
-
4 CVEs has Spoofing possibilities
-
2 CVEs are Security Bypass bugs
Two of the CVEs (CVE-2021-42292 and CVE-2021-42321) have been classified as actively exploited and were disclosed publicly. Most concerning is that these two CVEs have been called out by CISA in its recent directive encouraging users to apply immediate patching to a list of 291 Known Exploited Vulnerabilities (KEV).
Microsoft had disclosed that security updates for Microsoft Office for Mac have not been released as of yet.
Zero-days
Microsoft had released fixes for six zero-day vulnerabilities this month:
-
CVE-2021-38631 – Windows Remote Desktop Protocol (RDP)
-
CVE-2021-41371 – Windows Remote Desktop Protocol (RDP)
-
CVE-2021-43208 – 3D Viewer
-
CVE-2021-43209 – 3D Viewer
-
CVE-2021-42292 – Microsoft Excel
-
CVE-2021-42321 – Microsoft Exchange Server
CVE-2021-42321 is a remote code execution vulnerability in Microsoft Exchange Server. The bug with a CVSS v3 score of 8.8 (high) arises as a result of incorrect validation of command-let (cmdlet) parameters. An attacker would have to be authenticated to a susceptible Exchange Server in order to exploit this issue. According to Microsoft, this vulnerability has been used in “limited targeted attacks” in the wild.
Throughout 2021, many notable vulnerabilities in Microsoft Exchange Server have been exposed, starting with ProxyLogon and linked zero-days in March, and later followed by ProxyShell. Organizations running Exchange Server on-premises should deploy security upgrades as soon as possible to avoid future exploitation once the proof-of-concept code is made public.
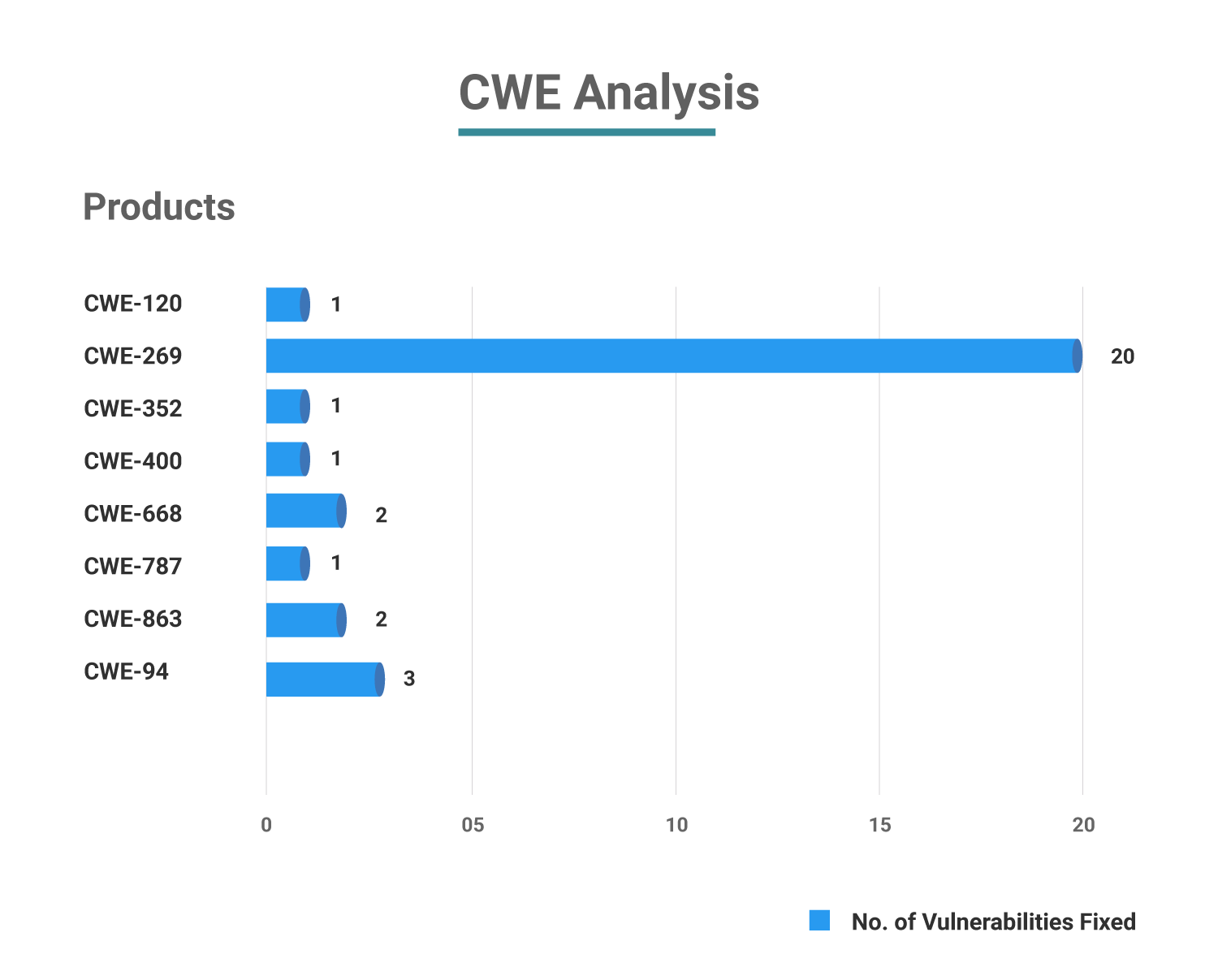
CWE Analysis
When analyzing these vulnerabilities based on the Common Weakness Enumeration (CWE) categorization, 20 CVEs carry a CWE of CWE-269 (Improper Privilege Management) that falls under 2021 CWE Top 30 Most Dangerous Software Weaknesses. On the whole, 24 CVEs have not been assigned a CWE Identifier yet.
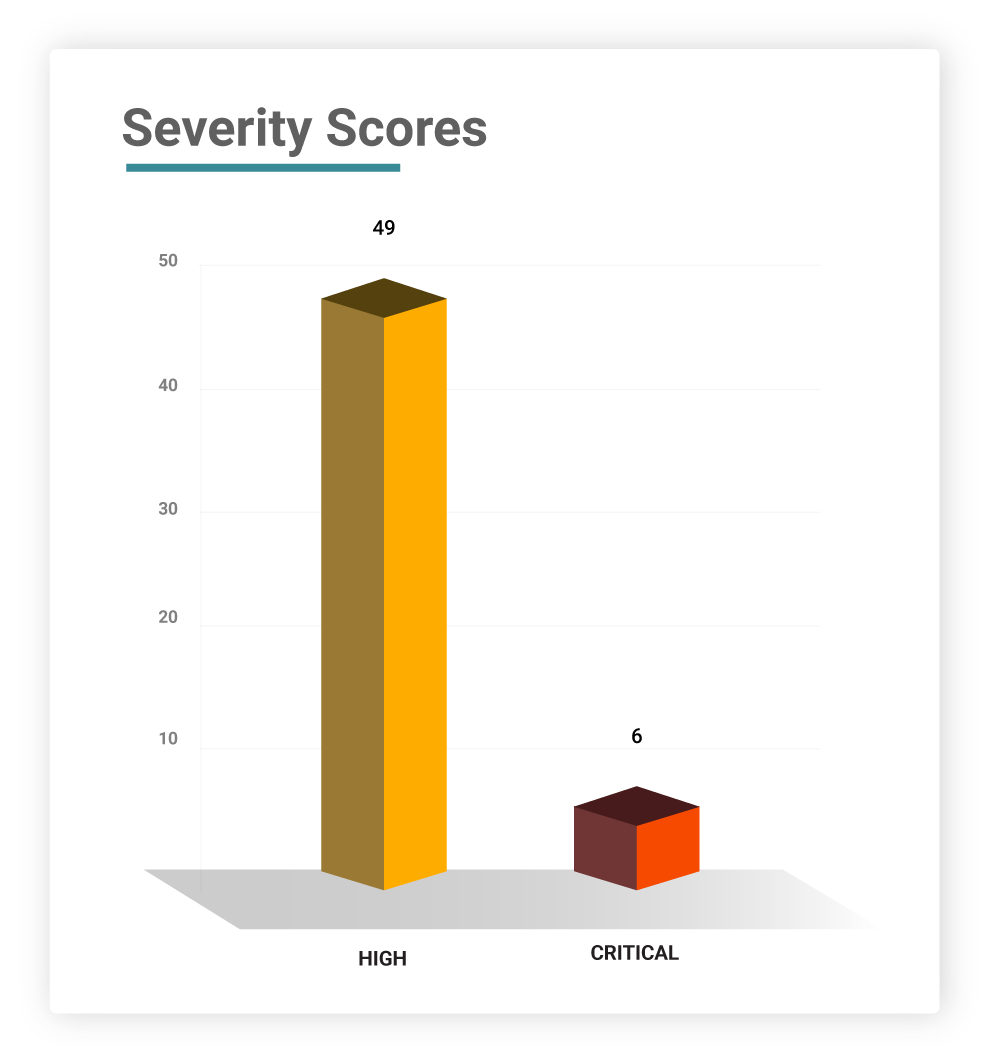
Severity Scores
Product Analysis
The November patch package has an influence on the following products: Microsoft Azure, the Chromium-based Edge browser, Microsoft Office — as well as associated products such as Excel, Word, and SharePoint — Visual Studio, Exchange Server, Windows Kernel, and Windows Defender. Windows products received a fix for 27 vulnerabilities in which 6 CVEs accounted for Remote Code Execution and 14 CVEs for Privilege Escalation.
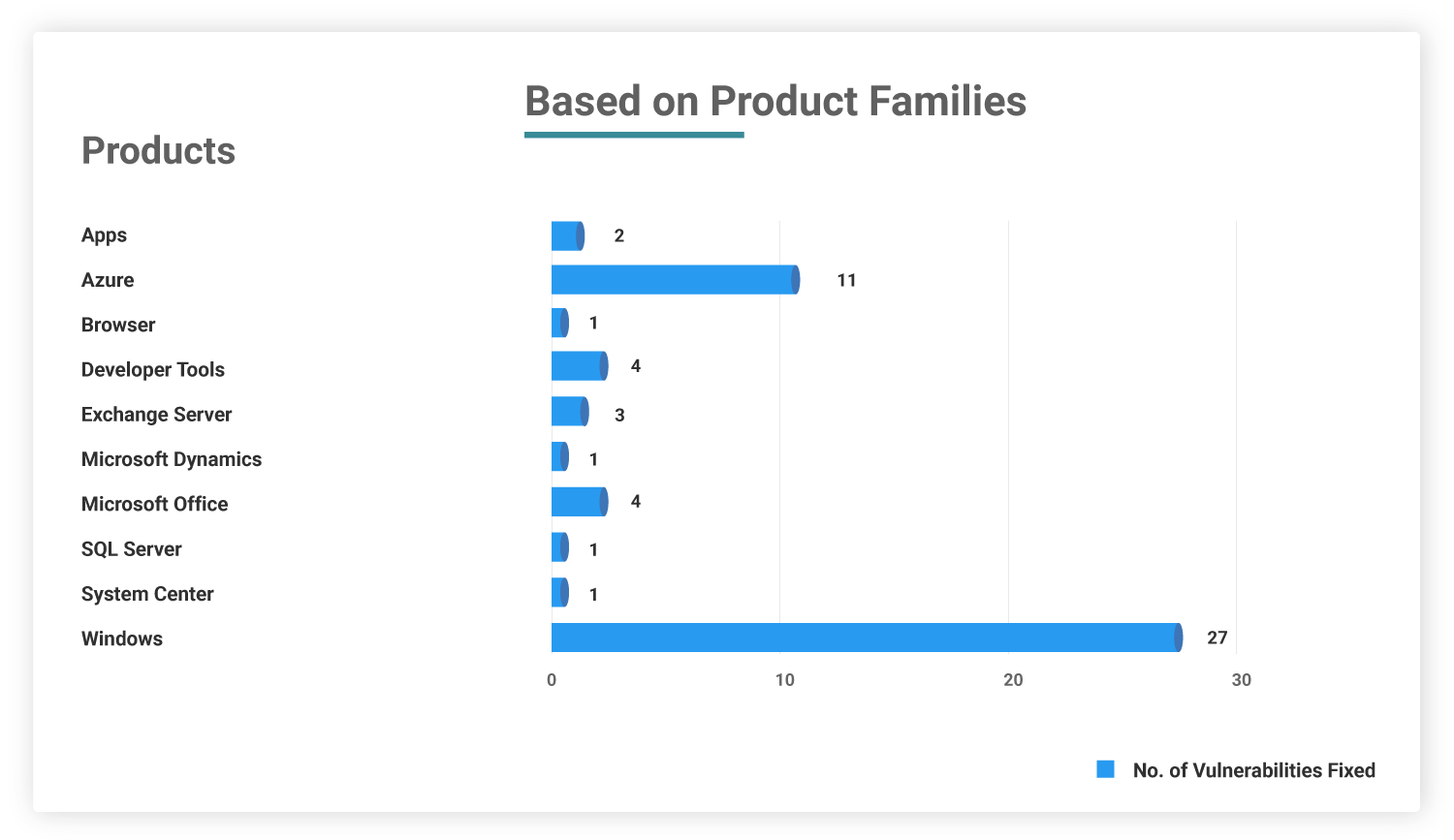
Table: Microsoft November Patches 2021
It is important to understand that new vulnerabilities are found every day. Legacy scanning tools generate hundreds or thousands of vulnerable files each time they run. Due to these overwhelming numbers, security teams are stretched to the limit, forcing them to prioritize vulnerabilities based solely on traditional CVSS severity levels. Therefore, we recommend implementing risk-based vulnerability management into your business that will help reap significant benefits.