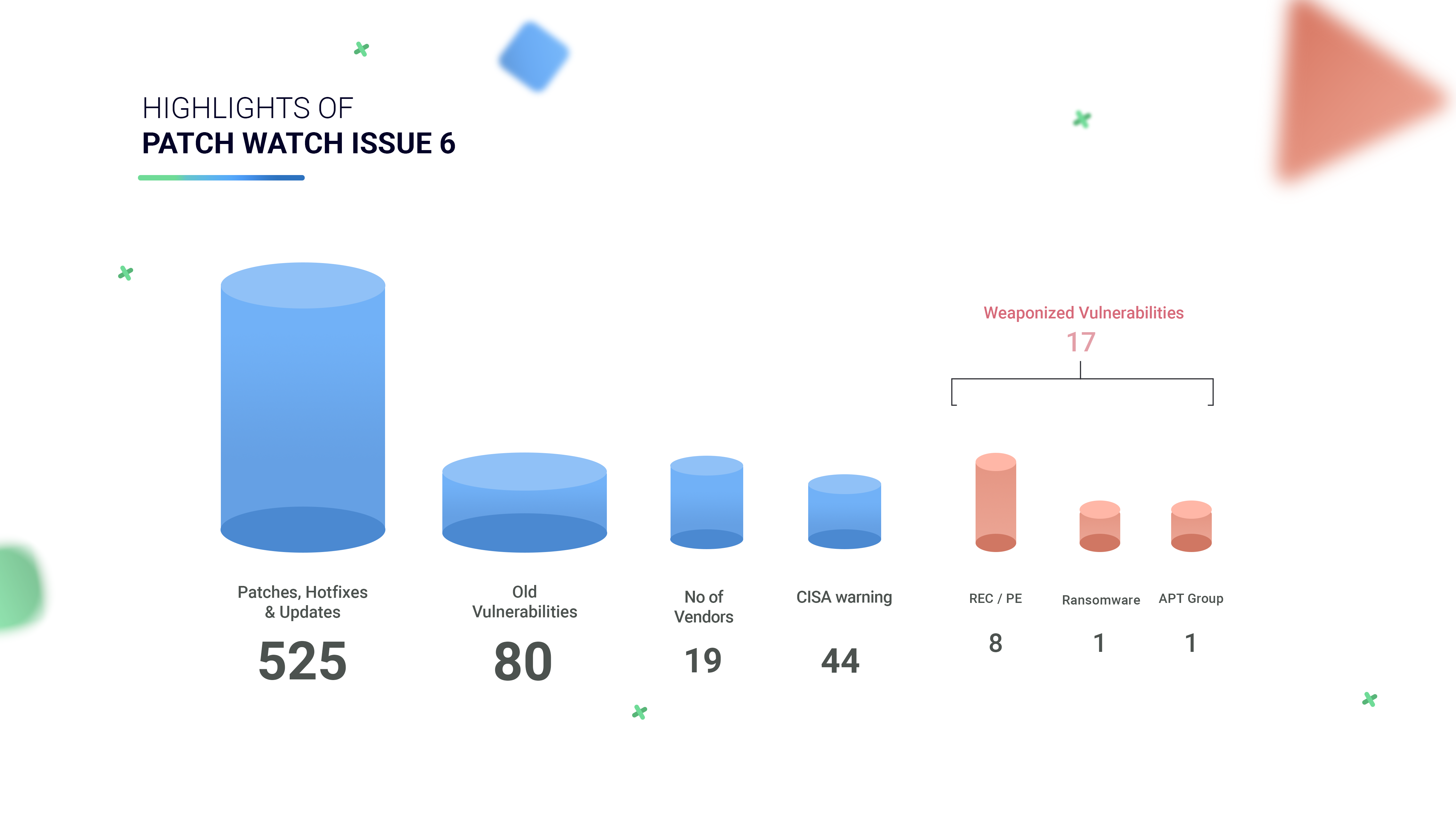
Highlights of Patch Watch Issue 6
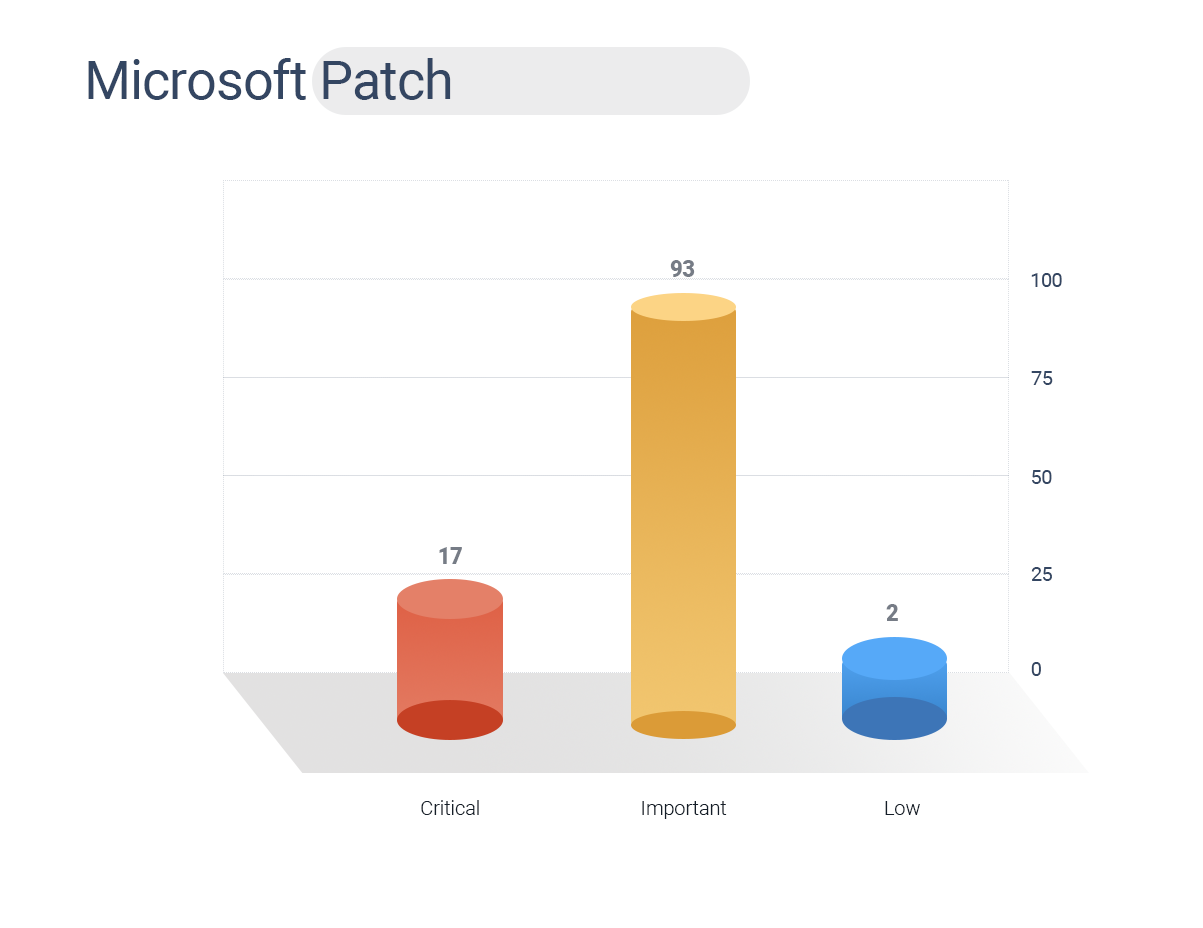
- Microsoft November patch Tuesday fixed 112 security bugs.
- 19 Vendors, including Adobe, Apple, Cisco, Citrix, Chrome, Microsoft, Mozilla, Palo Alto, Checkpoint, Dell, and other popular vendors, have released 525 security patches. (Out of these, 17 CVEs have known exploits)
- CISA has issued a security alert for 44 Vulnerabilities.
- 80 Old vulnerabilities have been fixed this week.
- 24 CVEs are associated with Remote Code Execution hence patching these would be optimum.
- Microsoft has also changed its security advisories by limiting the disclosing information for each bug.
- Of these, 17 are critical, 93 are as important, and two are low in severity.
- Among the bugs patched, zero-day bug – CVE-2020-17087, an actively exploitable vulnerability with PE capabilities.
- CVE-2020-17087 exists in Windows Kernel Cryptography Driver which constitutes a locally accessible attack surface.
- When CVE-2020-15999 (type of memory-corruption vulnerability) and CVE-2020-17087 are linked together would allow an attacker to break out of Google Chrome’s sandbox.
- 17 CVEs have known exploits
- 1 CVE is associated with Sea turtle APT group
- 1 CVE has ties with Satan Ransomware
- 508 are yet to be weaponized
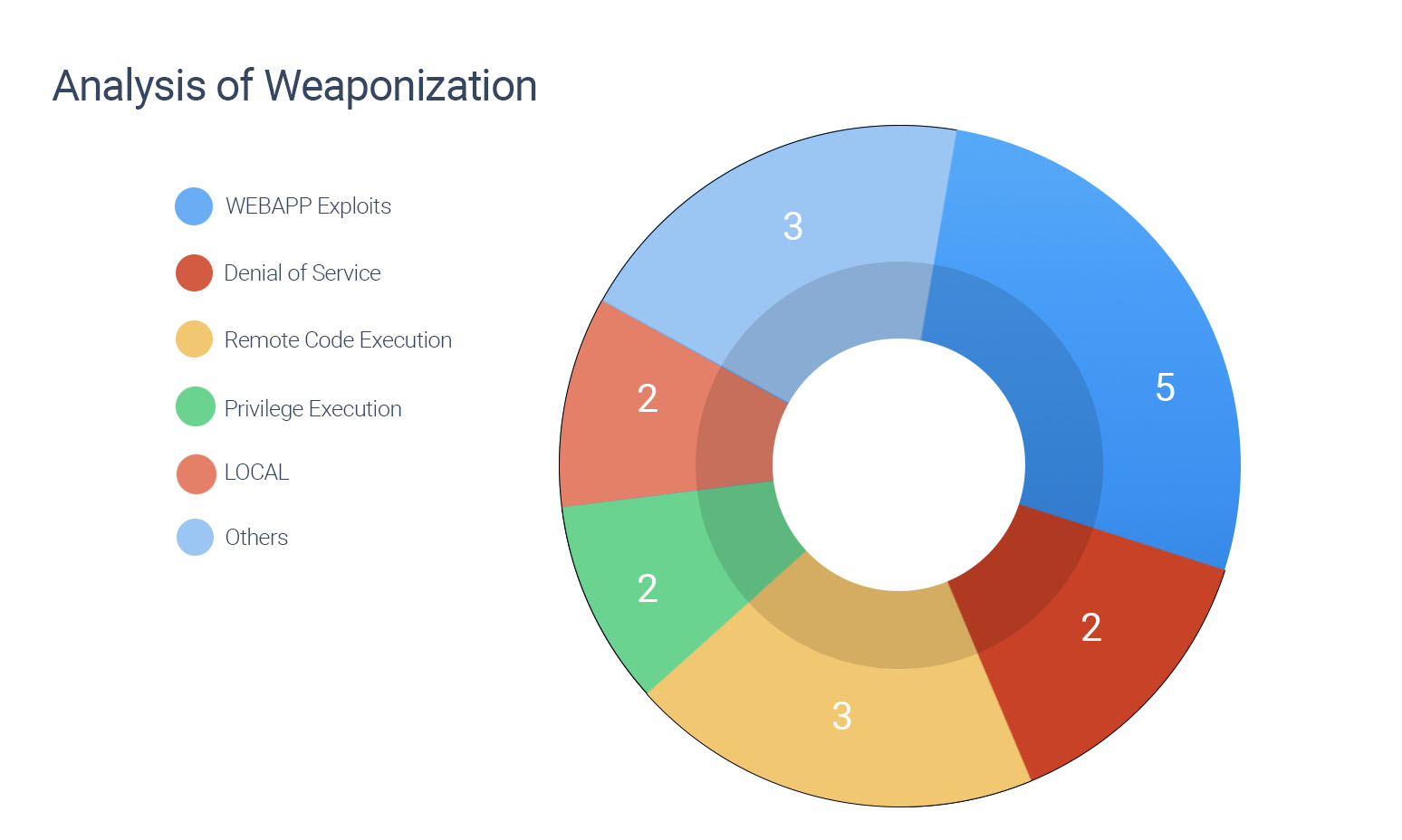
- Exploitable vulnerabilities are correlated with RCE, DoS, WEB APP, Local, PE, and others.
- Security patches for 80 old vulnerabilities have been released. These vulnerabilities range from years – 2015 to 2019.
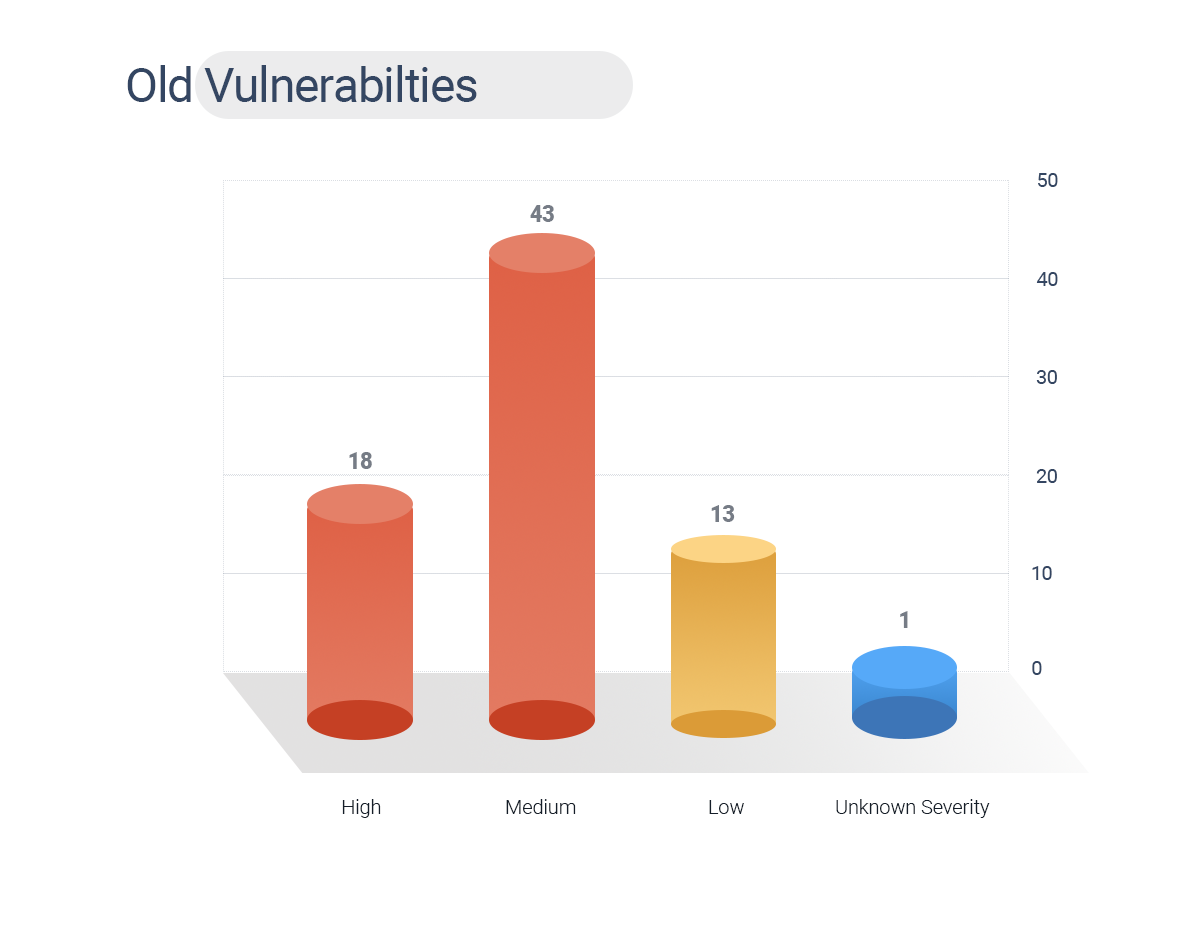
- Out of 80 CVEs, CVE-2018-7600 is associated with both Sea turtle APT group and Satan Ransomware and has a CVSS V3 Score of 7.5.
Table 1: Old Vulnerabilities
- CISA has issued 47 security alerts for this week, including 7 CVEs rating high severity, 20 CVEs of medium, 9 of low severity, and 8 CVEs with unknown severity.
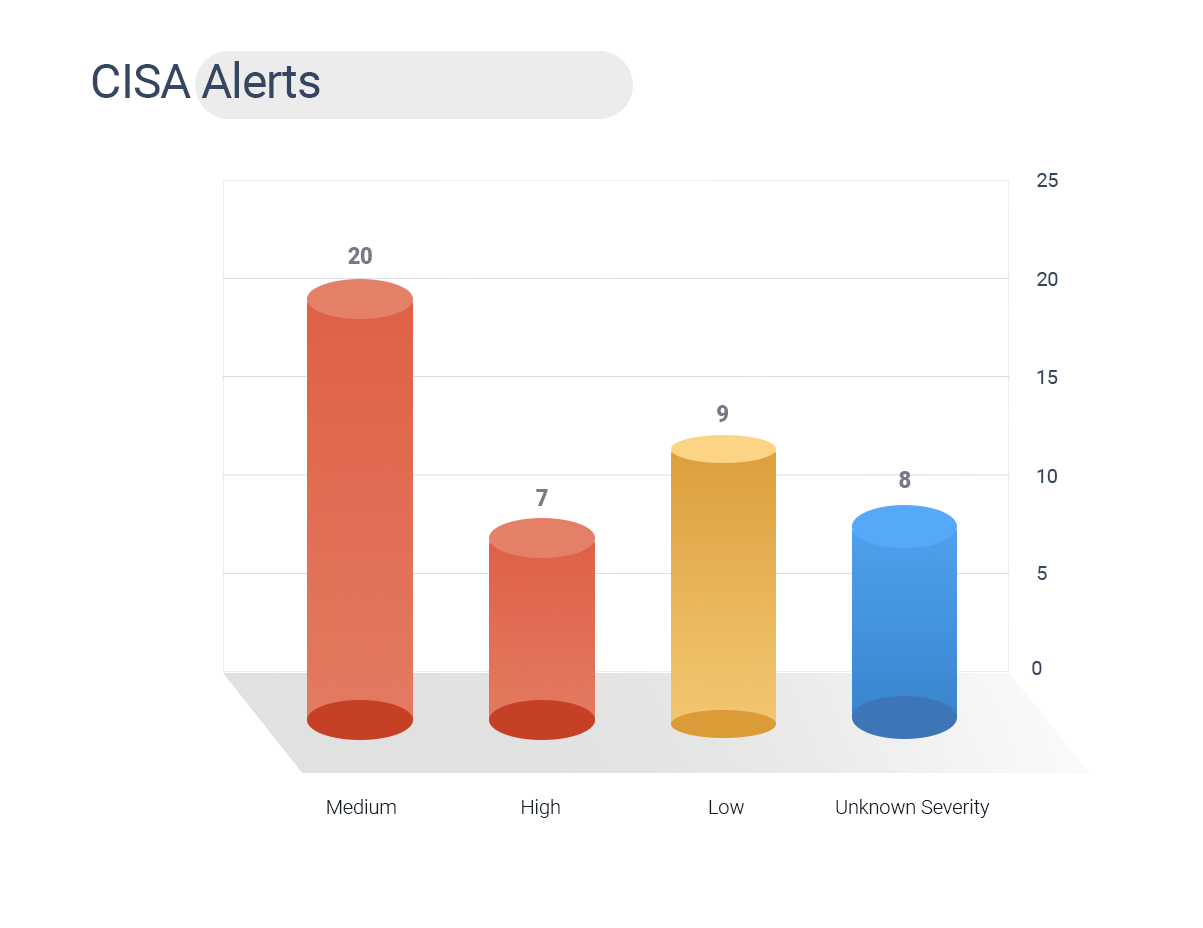
Table 2: CISA Alerts
According to a study by the University of Maryland, a cyber attack occurs once every 39 seconds (2,244 times per day). Cyber Hygiene is the only arsenal that can be employed by security teams to combat threat actors who mount bold and daring attacks on organizations every day.
Table 3: Weaponized Vulnerabilities
Table 4: Vulnerabilities Yet to be Weaponized
Organizations today working with massive data sets are undoubtedly challenged with securely managing those data. So, urge patching and prevent your organization from falling victim to an attack.
Happy Patching
Team CSW









