Chinese state-sponsored threat group named “HAFNIUM” targets attacks on-premises versions of Microsoft Exchange Servers.
On March 3, following Microsoft’s release of out-of-band security patches to address multiple zero-day bugs (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065) in on-premises versions of Microsoft Exchange Server, CISA issued an emergency directive alert mitigate product vulnerabilities.
Nine Reasons to Patch Hafnium Vulnerabilities
-
All four CVEs are tied to Dearcry ransomware
-
Nine APT groups are exploiting these vulnerabilities – Hafnium, Winnti , Tick, LuckyMouse, Websiic, Calypso, Tonto Team, Mikroceen and Vicious Panda Group
-
PlugX and ShadowPad Malware are associated with these four CVEs.
-
Needless to say all vulnerabilities are weaponized and NVD has rated them with high severity.
-
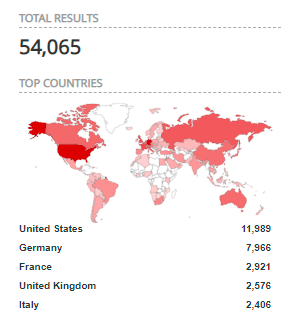
Initially, the US was the most targeted country but ended up impacting customers worldwide exposing 54,065 assets.
-
This is a fixable problem because patches are available for all four vulnerabilities and all these vulnerabilities are detected by Qualys, Tenable, and Nexpose scanners.
-
The Microsoft Exchange Server team released a script to check the HAFNIUM indicators of compromise (IOCs)
-
Once the systems are compromised by these vulnerabilities, the exchange server is totally under the threat actors control that matures into more devastating outbreaks, such as ransomware attacks and data exfiltration.
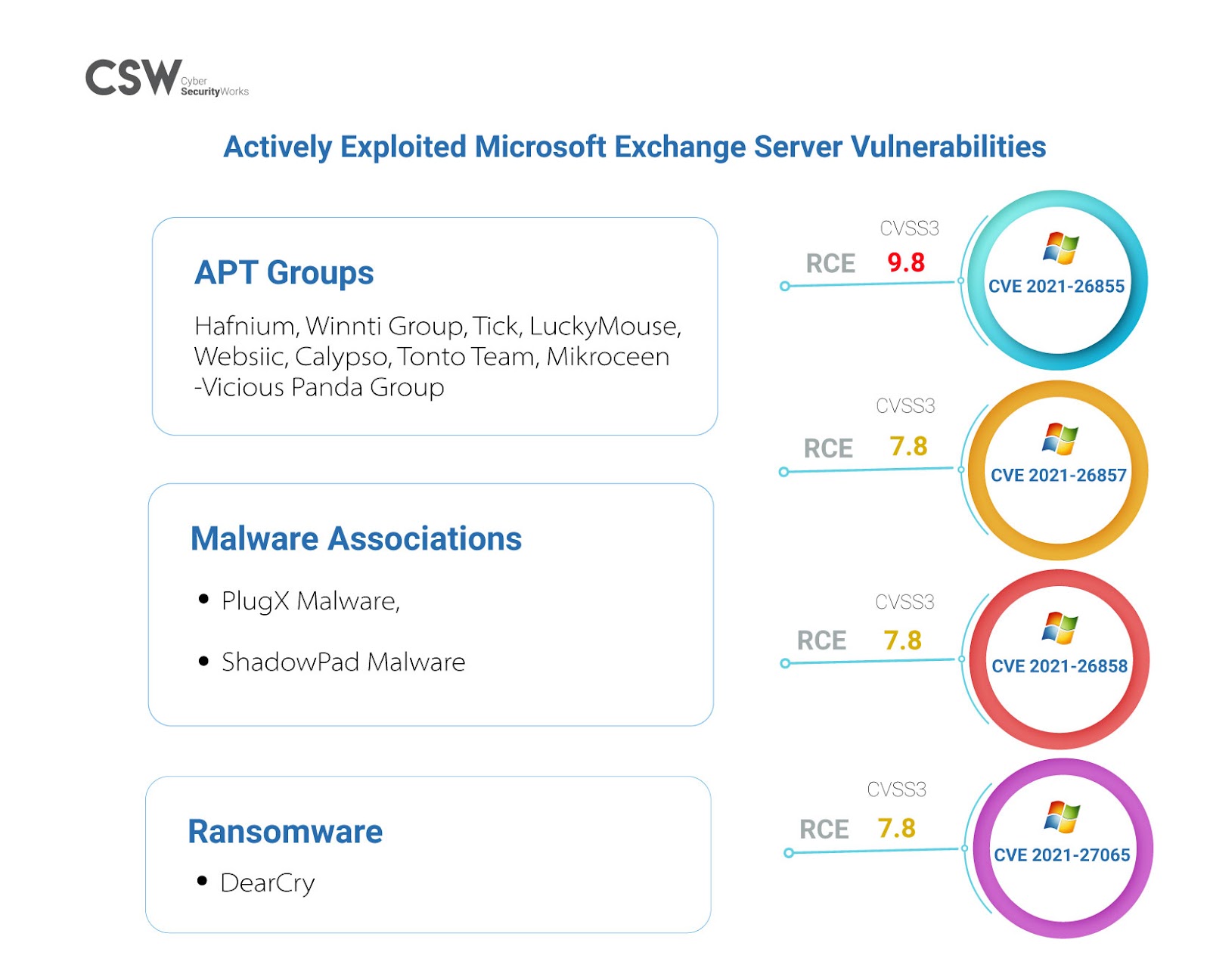
Microsoft also patched three unrelated remote code execution (RCE) vulnerabilities (CVE-2021-26412, CVE-2021-26854, CVE-2021-27078) in Microsoft Exchange Server in addition to the four zero-day vulnerabilities. Organizations must take the ongoing situation into consideration and patch these vulnerabilities immediately.
Impact
These vulnerabilities could be used to enact a four-step attack –
-
When exploited, these vulnerabilities would gain initial access to the Exchange server.
-
HAFNIUM operators would install web shells on the compromised server, which potentially allow attackers to steal data and drop malware to compromise the targets further.
-
Then, perform a memory dump of the LSASS.exe executable to harvest cached credentials using this web shell.
-
Thus, they export mailboxes and steal data from the Exchange server and upload it to file-sharing services, such as MEGA, where they could later retrieve it.
The New Malware
Microsoft Threat Intelligence Center (MSTIC) has identified NOBELIUM, the new threat actor behind the attacks against SolarWinds, the SUNBURST backdoor, TEARDROP malware. These threat actors are using both malware and backdoor to gain access by leveraging networks. Lately, Fire Eye tracked three new malwares named GoldMax, GoldFinder, and Sibot, which perform action on targeted networks and evade detection.
It has been observed that stolen credentials are utilized to access cloud services like email, storage, and maintain access to networks via virtual private networks (VPNs) and remote access tools.
Table: Microsoft Exchange Server Patches
What Microsoft customers can do in Response
Multiple sources indicate that at least 30K US organizations have been affected by these vulnerabilities. Immediate patching is essential and of paramount importance before threat actors exploit these bugs.
Microsoft stated that a click mitigating tool has been released to detect the new NOBELIUM components which block new unknown threats. It is recommended to follow Microsoft’s guidelines and update Exchange Server immediately to fix these vulnerabilities.
Check your attack surface exposure. Talk to us now









