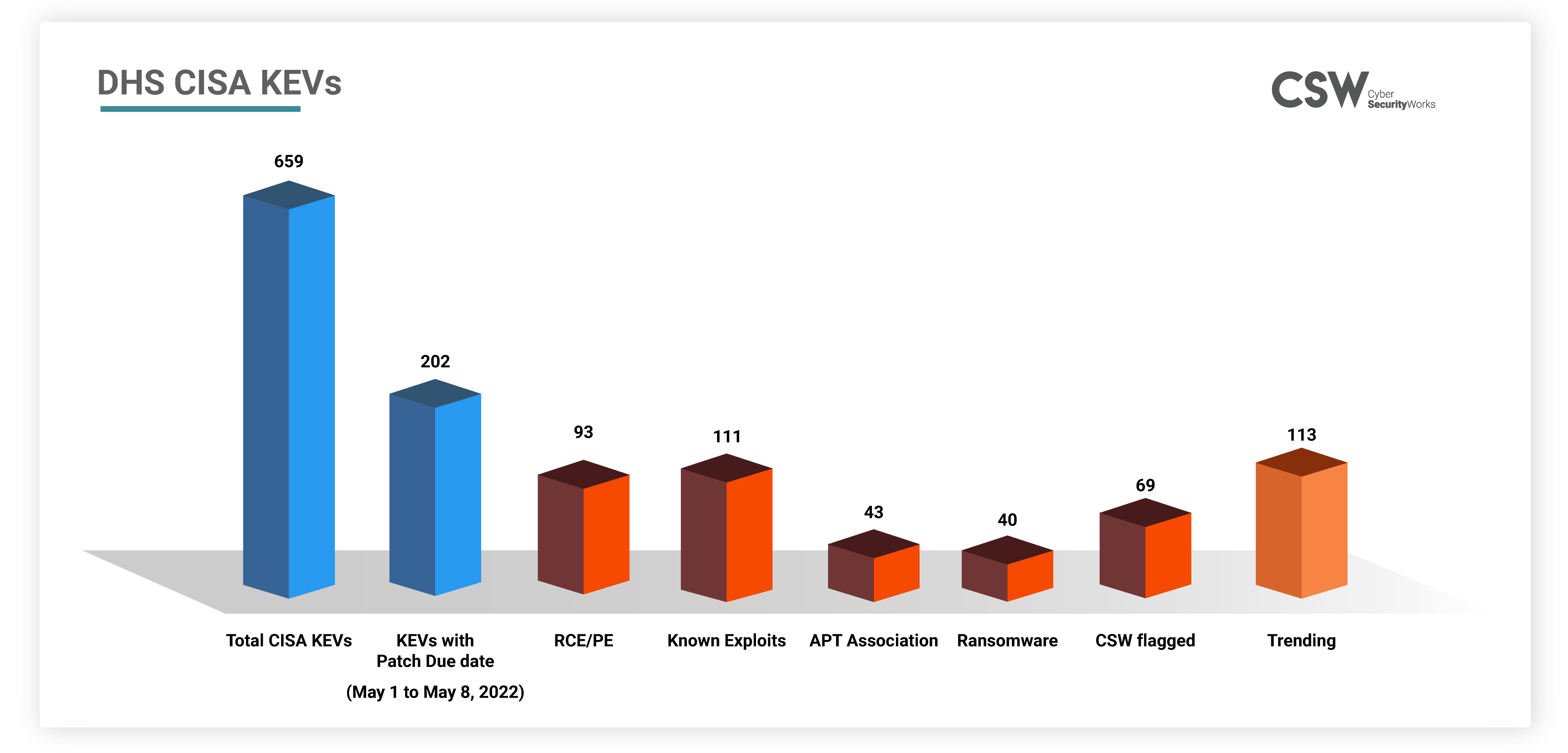
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has added five new flaws to its list of actively exploited vulnerabilities used in cyberattacks this week. This blog lists all of the DHS CISA KEVs that need to be patched this week (May 1 to May 8, 2022).
The federal agencies are expected to patch 202 known exploited vulnerabilities in the DHS CISA catalog this week in time for the May 1 to May 8, 2022 deadline. Based on our analysis of these KEVs, we found that –
 Our ML and AI model predicts that four out of 173 CVEs are potentially 38 times more likely to be exploited. So patch them now before they become problems.
Our ML and AI model predicts that four out of 173 CVEs are potentially 38 times more likely to be exploited. So patch them now before they become problems.
How Far Back Do They Go?
Of the 202 KEVs, 117 CVEs are old vulnerabilities dating from 2017 to 2021, with a patch deadline of May 1 to May 8, 2022.

Ransomware/APT Groups
Based on our analysis of DHS CISA KEVs due this week, we found –
-
There are 40 CVEs associated with various ransomware variants.
-
Among them, seven CVEs are connected to more than five ransomware outbreaks.
|
Top 5 Ransomware linked KEVs |
Count of Ransomware Families |
|
CVE-2017-0143 |
11 |
|
CVE-2017-11882 |
8 |
|
CVE-2018-4878 |
10 |
|
CVE-2019-19781 |
12 |
|
CVE-2015-0311 | CVE-2017-0199 | CVE-2018-13379 |
5 |
-
43 CVEs are identified with a threat group.
-
Of these, 9 CVEs are linked with more than five threat groups, all of which exist in Microsoft products.
|
Top 5 APT linked KEVs |
Count of Associated Threat Groups |
|
CVE-2012-0158 |
21 |
|
CVE-2017-0143 |
9 |
|
CVE-2017-0199 |
15 |
|
CVE-2017-11882 |
20 |
|
CVE-2018-0802 |
13 |
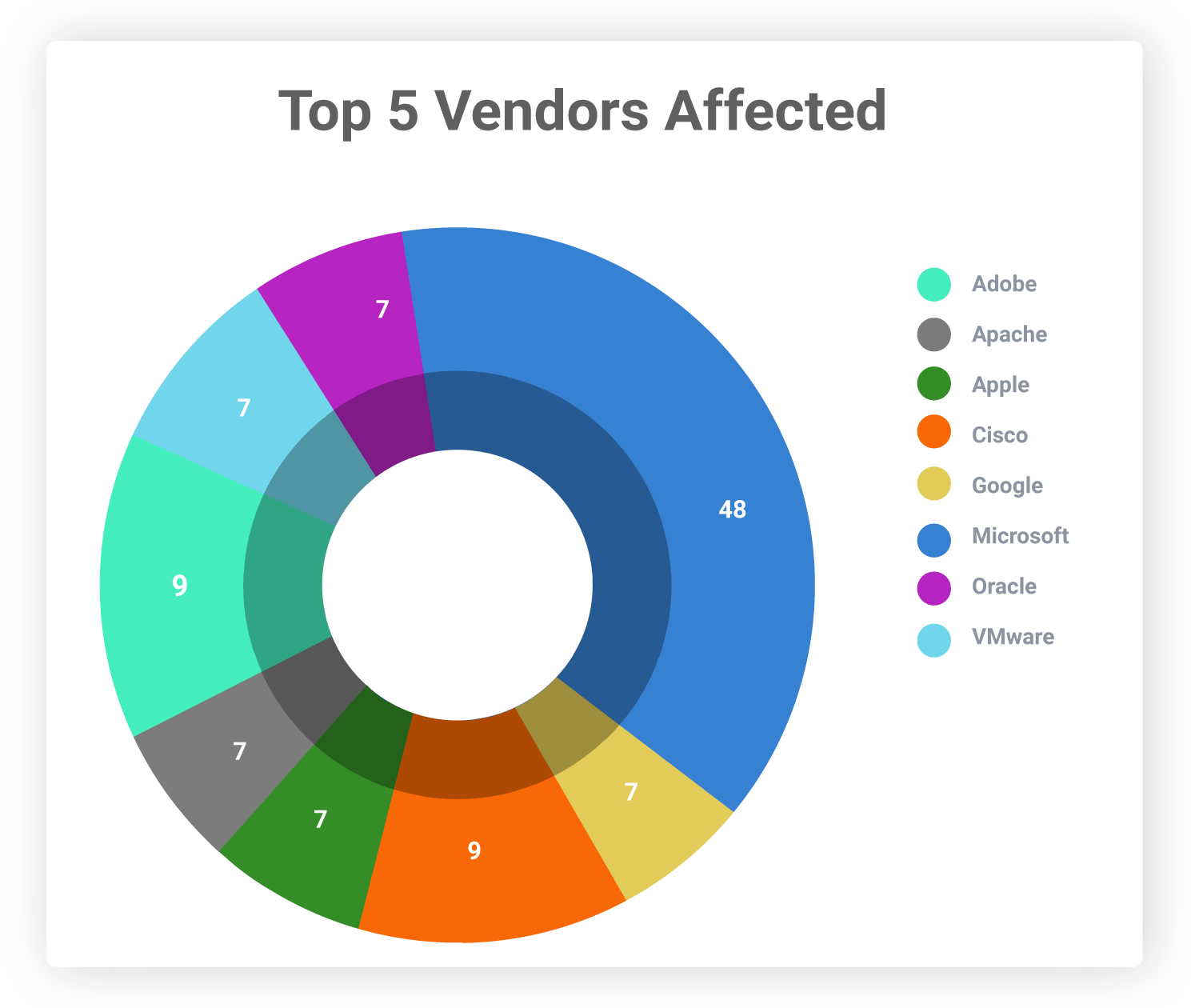
Which Vendors Are Affected?
These 202 CVEs that have a patch deadline of May 1 and May 5, 2022, affect 66 vendors such as Microsoft, Adobe, Vmware, Apple, Oracle, and Apache.
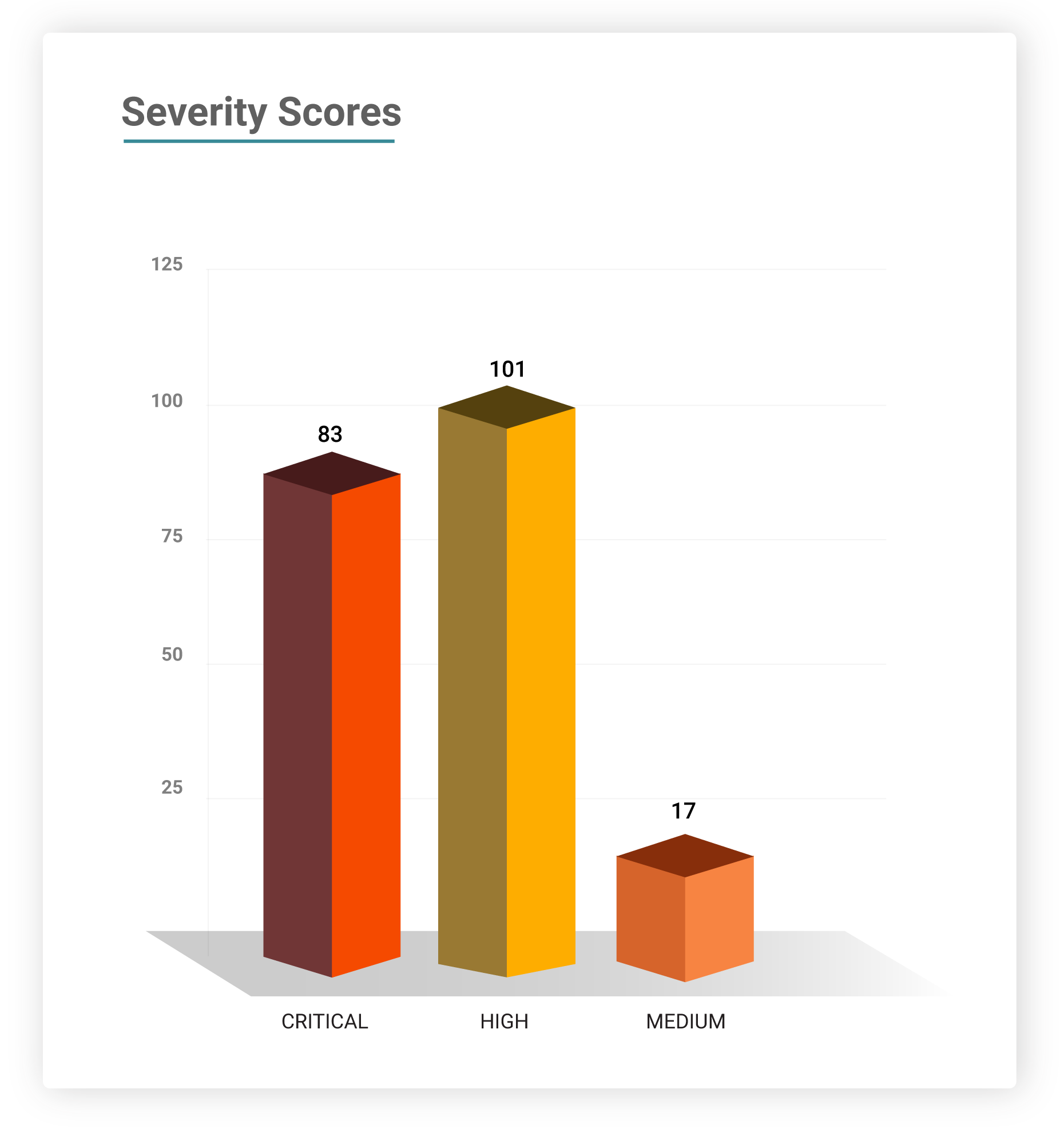
 Severity Scores
Severity Scores
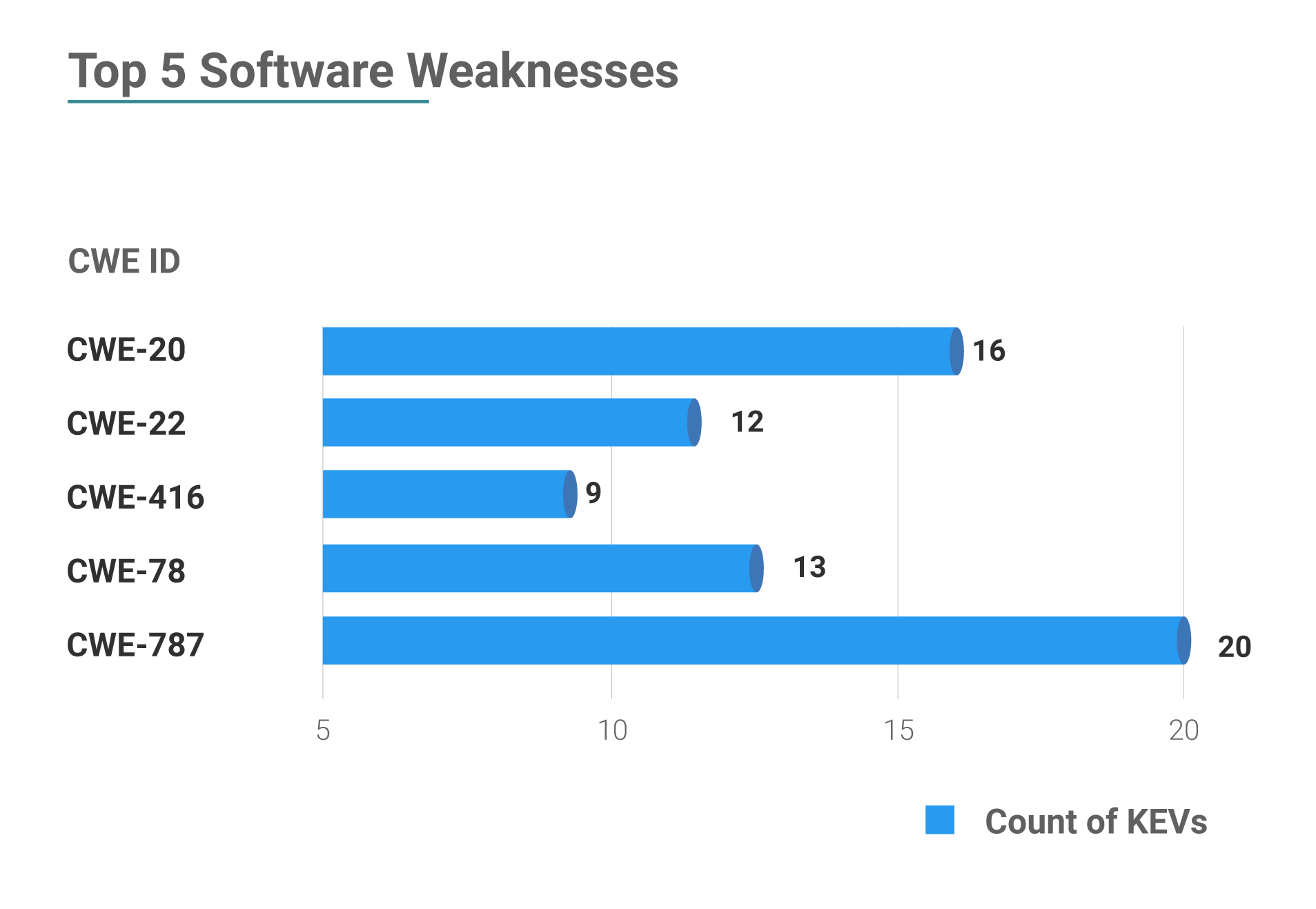
Software Weaknesses
161 out of the 202 KEVs with a patch due date between May 1 to May 7, 2022 fall under the Top 40 Most Dangerous Software Weaknesses, and 115 of these KEVs fall under OWASP Top 10:2021.
 These public warnings are intended to raise awareness among system administrators who have yet to implement the necessary security upgrades and to encourage them to prioritize the action.
These public warnings are intended to raise awareness among system administrators who have yet to implement the necessary security upgrades and to encourage them to prioritize the action.









