Recently, hackers have actively been exploiting zero-day vulnerabilities. The CISA is much more proactive in adding such vulnerabilities to the KEV catalog and recommending that organizations patch them on priority. In this post, we shall analyze the CVEs that have been prioritized for patching on December 9, 2022.
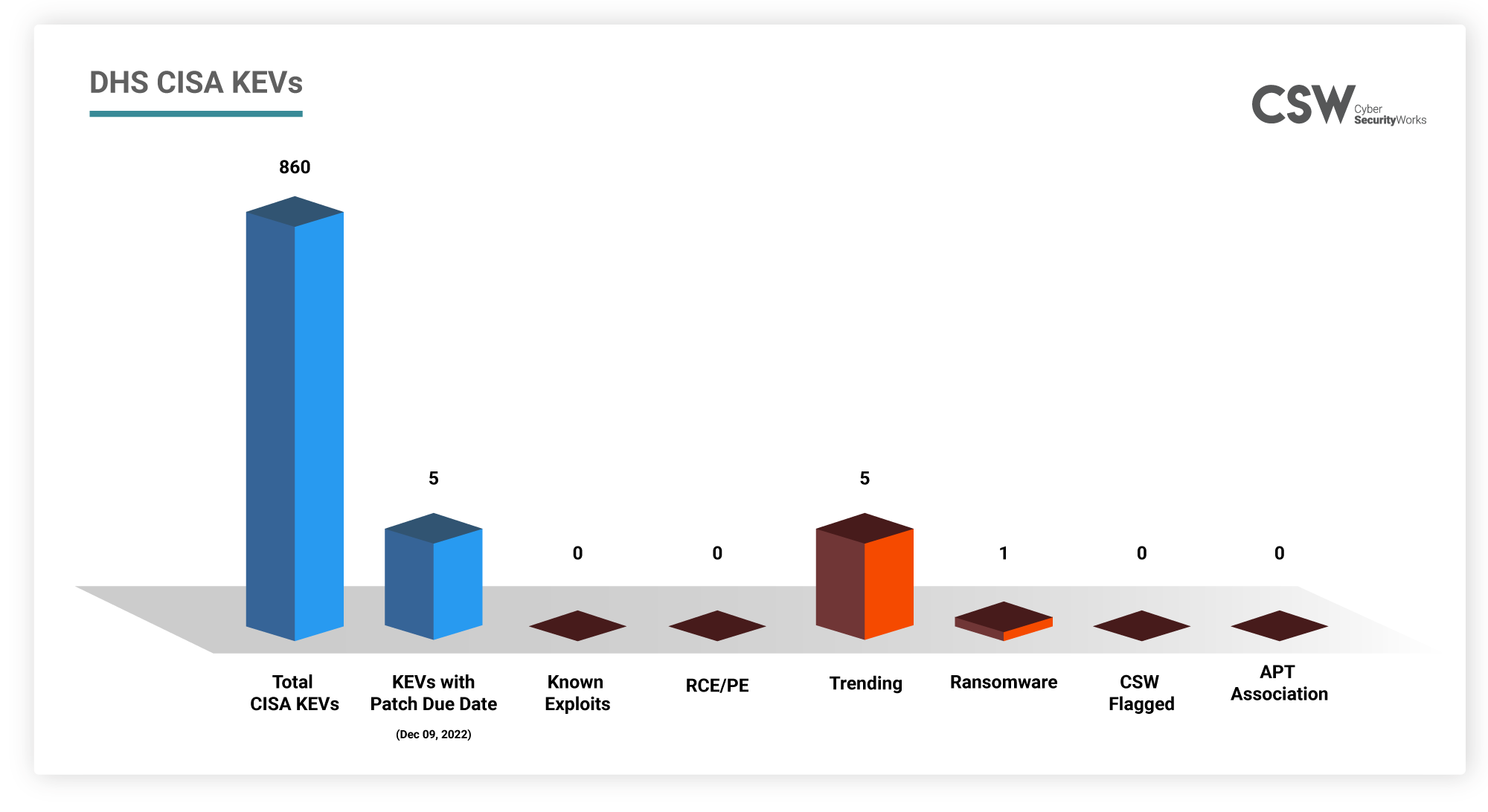
Why are these CVEs important?
From our analysis, we found that
-
All 5 vulnerabilities are trending this month.
-
CVE-2022-41049 is the second Mark-of-the-Web vulnerability that was exploited along with CVE-2022-41049. This allows attackers to download and execute malicious files without issuing a warning to the user. This is exploited by several ransomware groups (LockBit, BlackBasta, Magniber).
-
CVE-2022-41073 is a Microsoft Windows Print Spooler vulnerability which allows an attacker to gain root privileges.
-
CVE-2022-41128, is a Microsoft Windows Scripting Languages vulnerability in the JScript9 scripting language which allows for remote code execution.
-
CVE-2022-41125 is a ProxyNotShell vulnerability which is actively exploited in targeted attacks against at least 10 large organizations.
How Far Back Do They Go?
All 5 vulnerabilities were recently discovered and are actively exploited by the LockBit ransomware group.
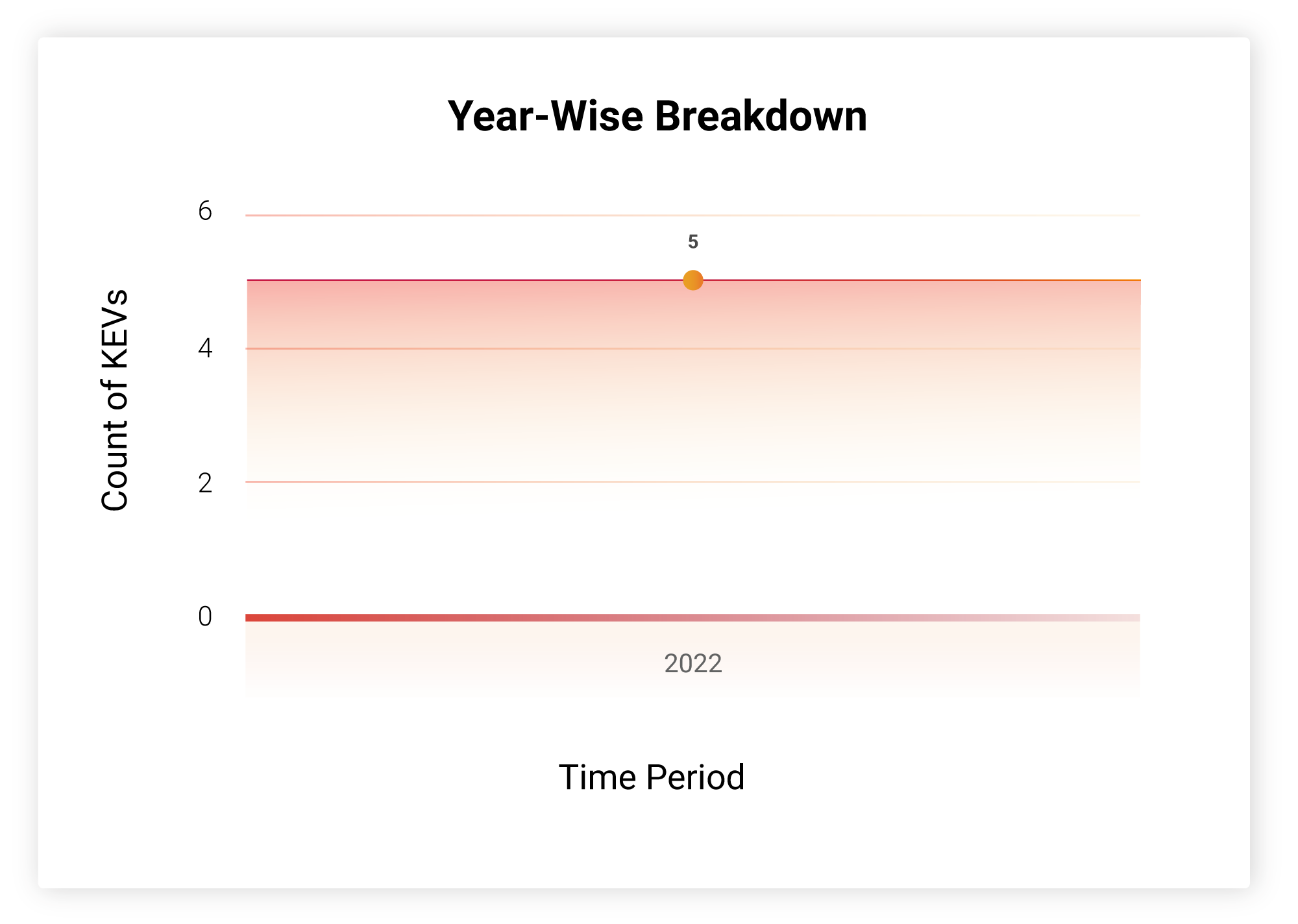
CVE-2022-41128 is an Internet Explorer zero-day bug found in the browser’s ‘JScript9’ JavaScript engine. It has been used in APT37 attacks since mid-November.
Which Vendors Are Affected?
All these vulnerabilities are found in Microsoft. Microsoft products are widely used in most organizations and homes, making all of them a target. Several journalists and diplomats have been affected by the Mark-of-the-Web vulnerabilities denoting that even personal devices are not off-limits.
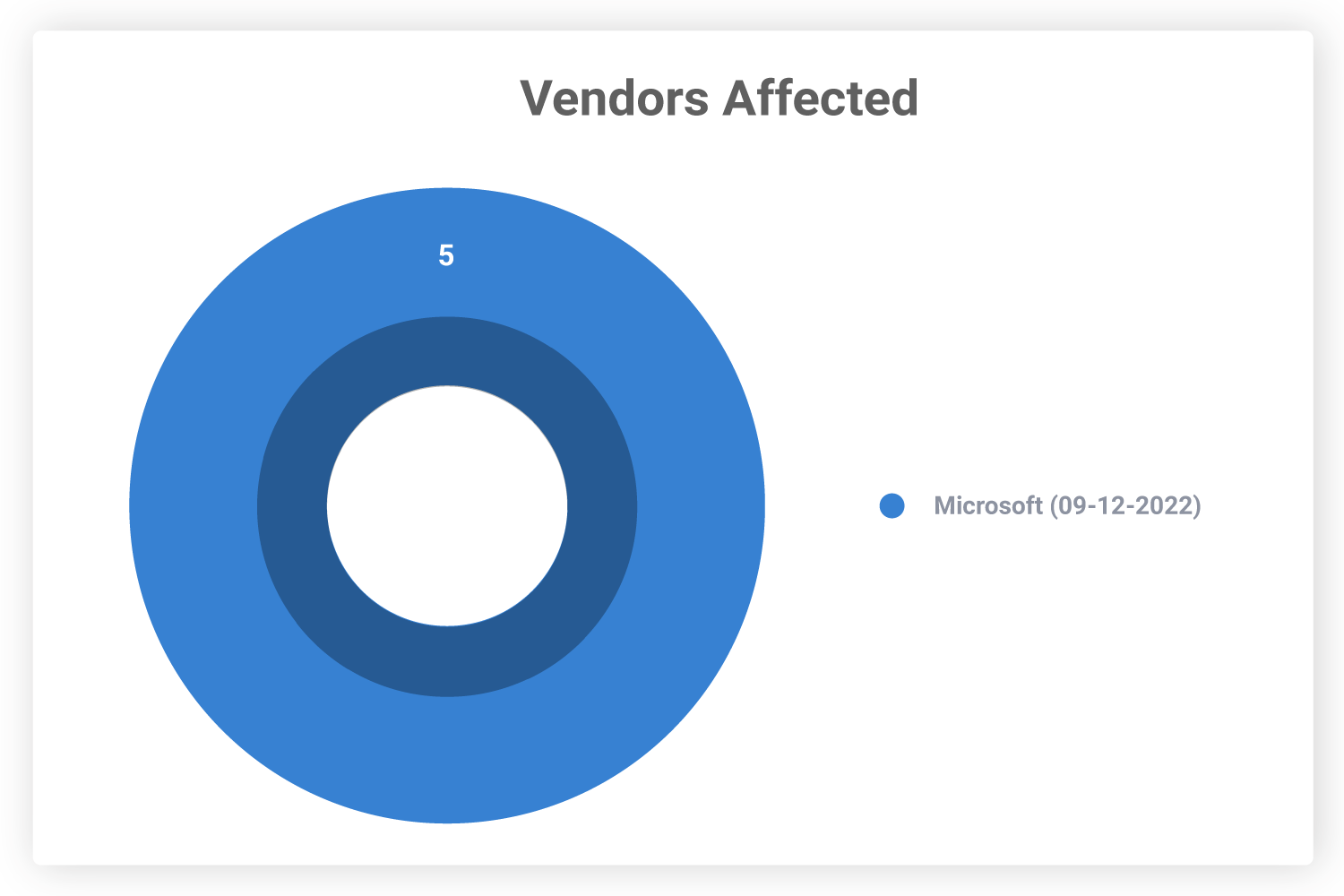
All Microsoft users must ensure that their devices are up-to-date on security patches to avoid being targeted by malicious actors.
Severity Scores
Three of these vulnerabilities are ranked high on the CVSS scale. These vulnerabilities impact 57 affected products in total and are commonly used.
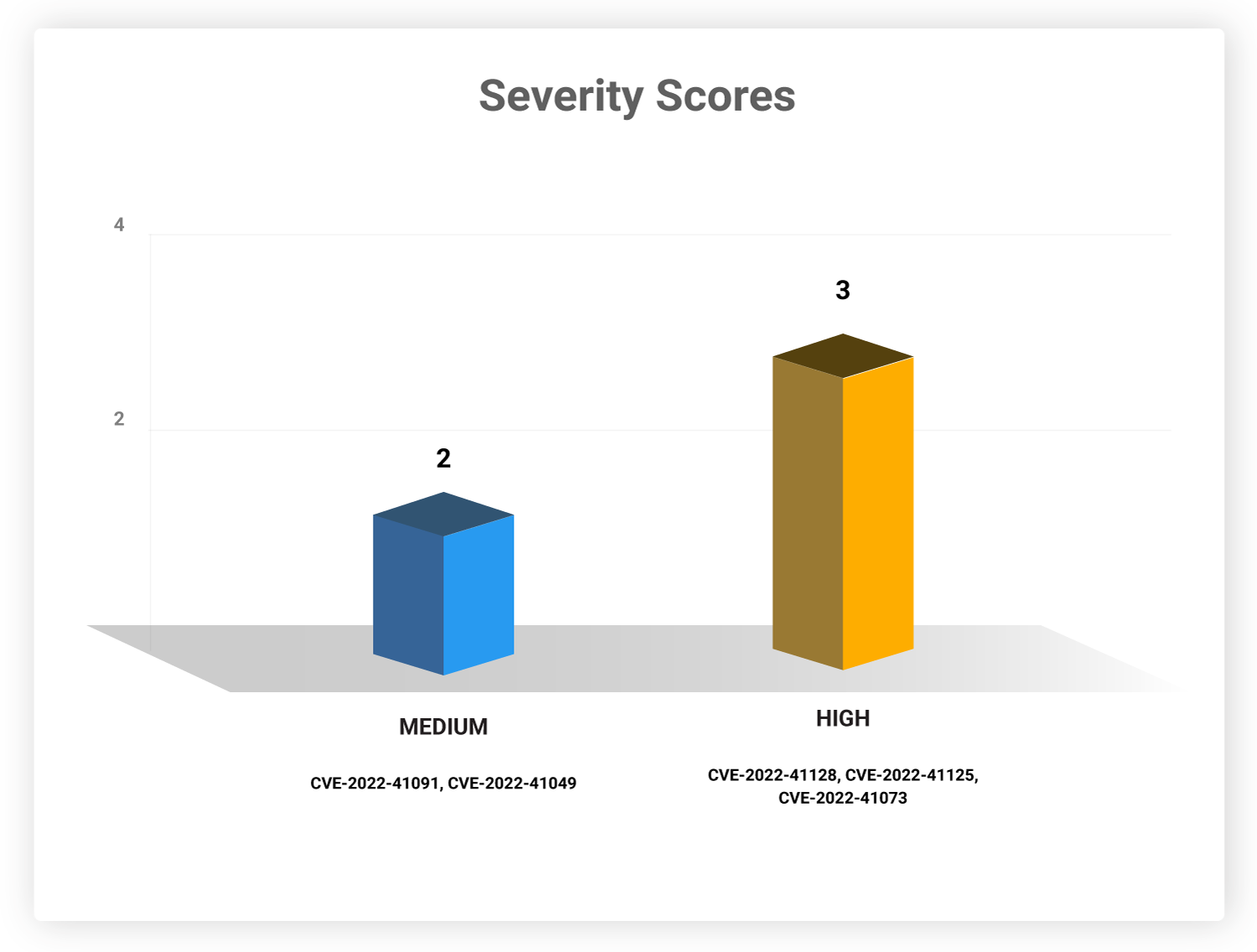
CVE-2022-41125 and CVE-2022-41073 allow an attacker to gain system-level privileges.
Software Weaknesses
None of the CVEs have any CWEs associated with them.
Table: DHS CISA KEVs
We urge organizations to implement patches for these CVEs at the earliest. With CSW’s threat-based approach and vulnerability intelligence, security teams can prioritize the threats, including all KEVs, and minimize their attack surface.
For the latest news regarding vulnerabilities that are exploited and critical threats, read our blog on Weekly Threat Intelligence.









