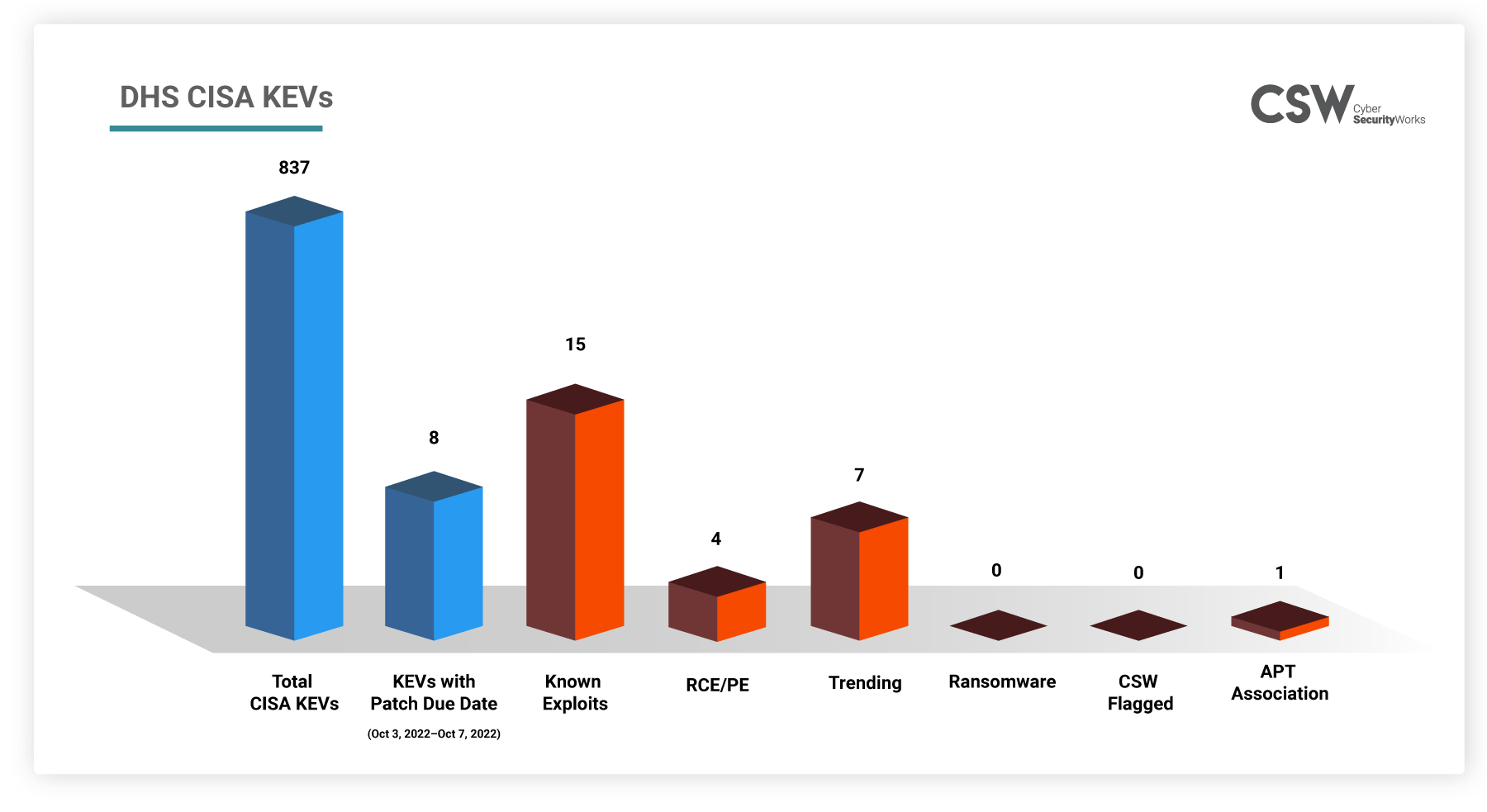
This week (Oct 3, 2022 – Oct 7, 2022), there are 8 vulnerabilities that are recommended to be patched by CISA. These vulnerabilities are especially important as they are found in popular vendor products used for both official and personal purposes.
We further analyzed these 8 KEVs and found that:
-
The vulnerabilities affect 443 products which are actively used in organizations. CVE-2013-6282, a Linux Kernel vulnerability has 187 affected products.
-
CVE-2010-2568 is a vulnerability exploited by the Equation APT group. It has existed for more than a decade in 23 products. It also has the highest number of exploits (7) among these CVEs.
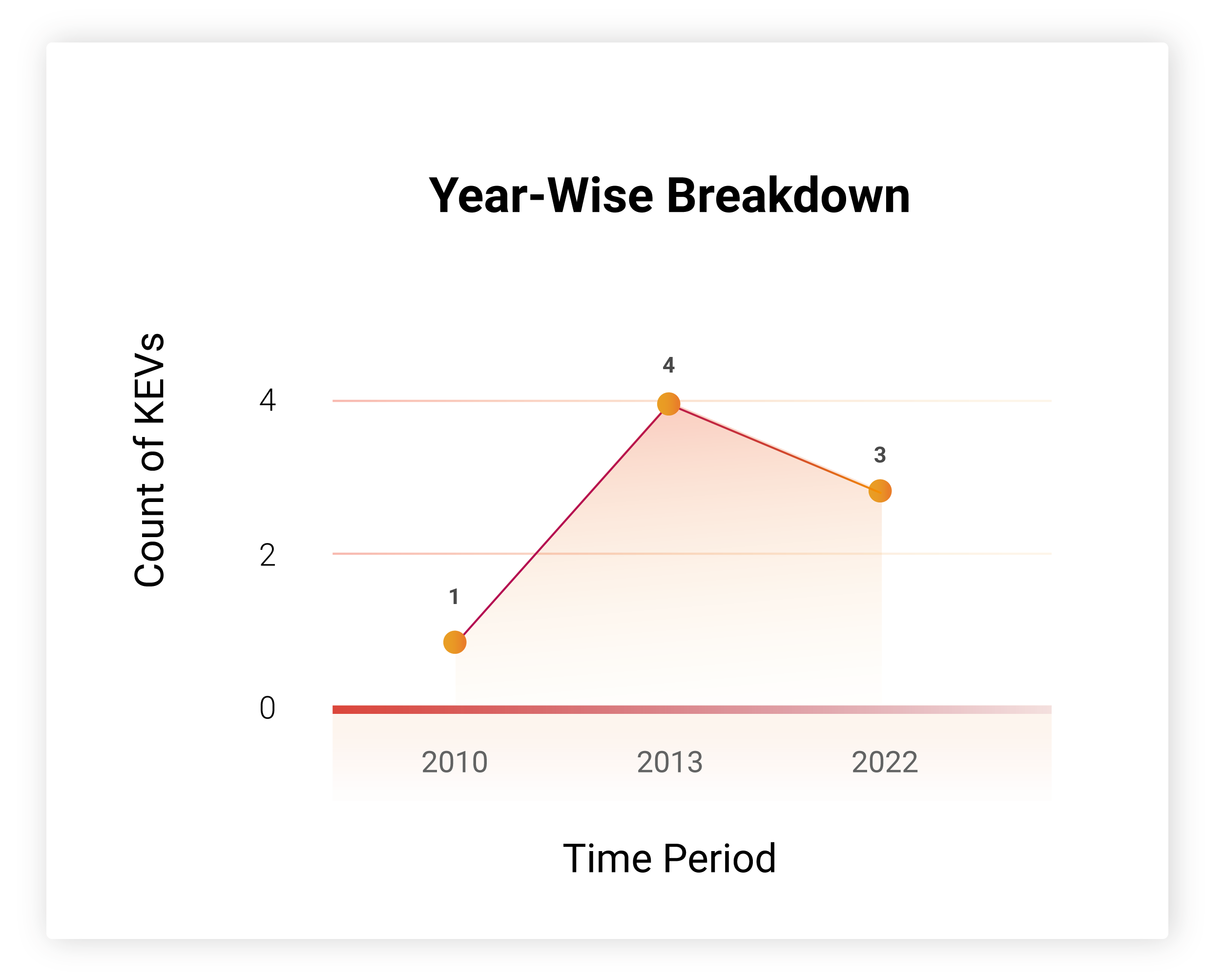
How Far Back Do They Go?
A majority of these vulnerabilities (5) are old and will have more exploits among them, making easy targets for hackers.
Which Vendors Are Affected?
Linux has the most number of vulnerabilities (3) that need to be patched this week. All these vulnerabilities which need immediate attention, are from 2013.
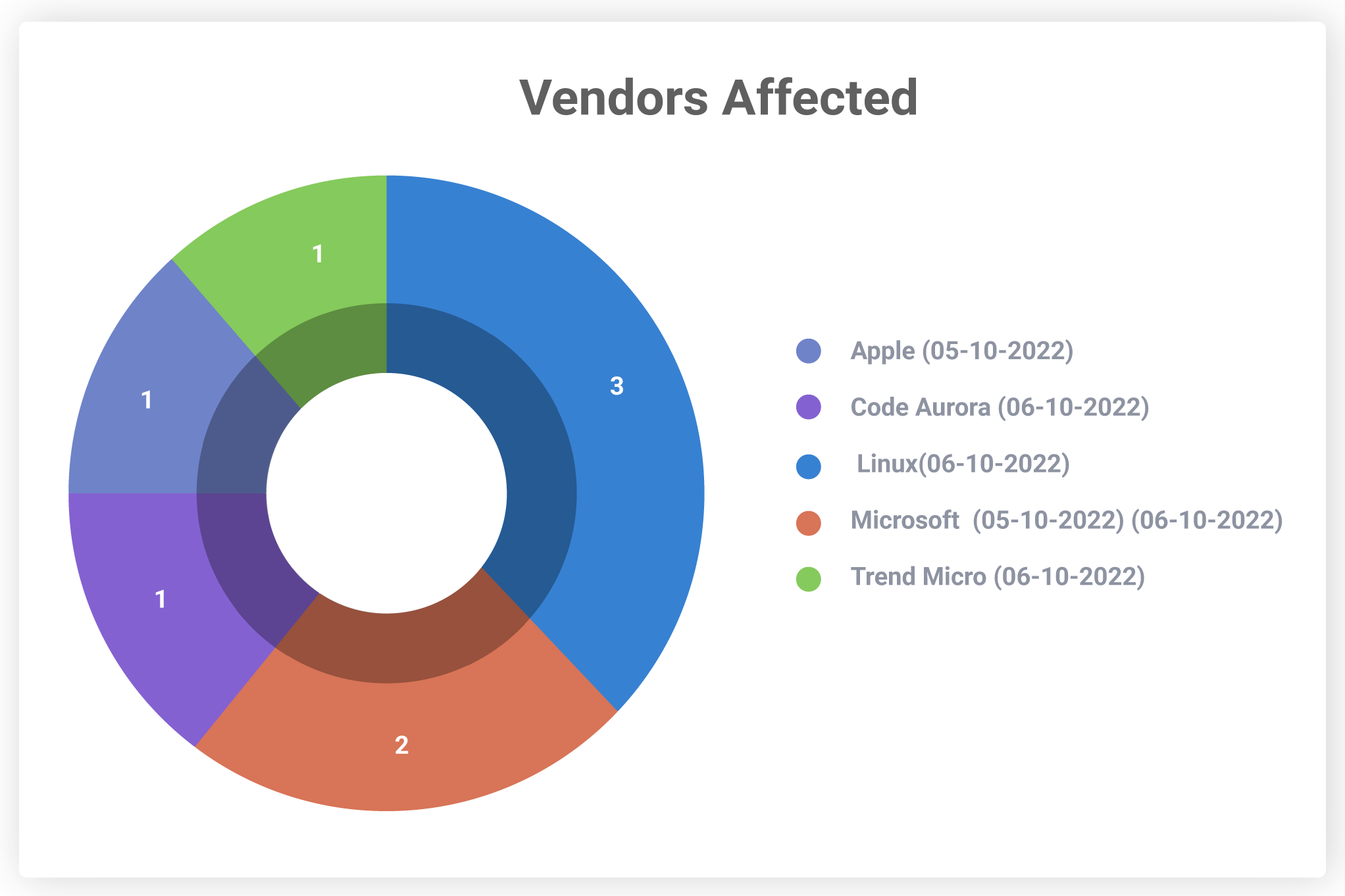
Organizations must keep themselves up-to-date with these vendor advisories and upgrade their products as and when new patches are released.
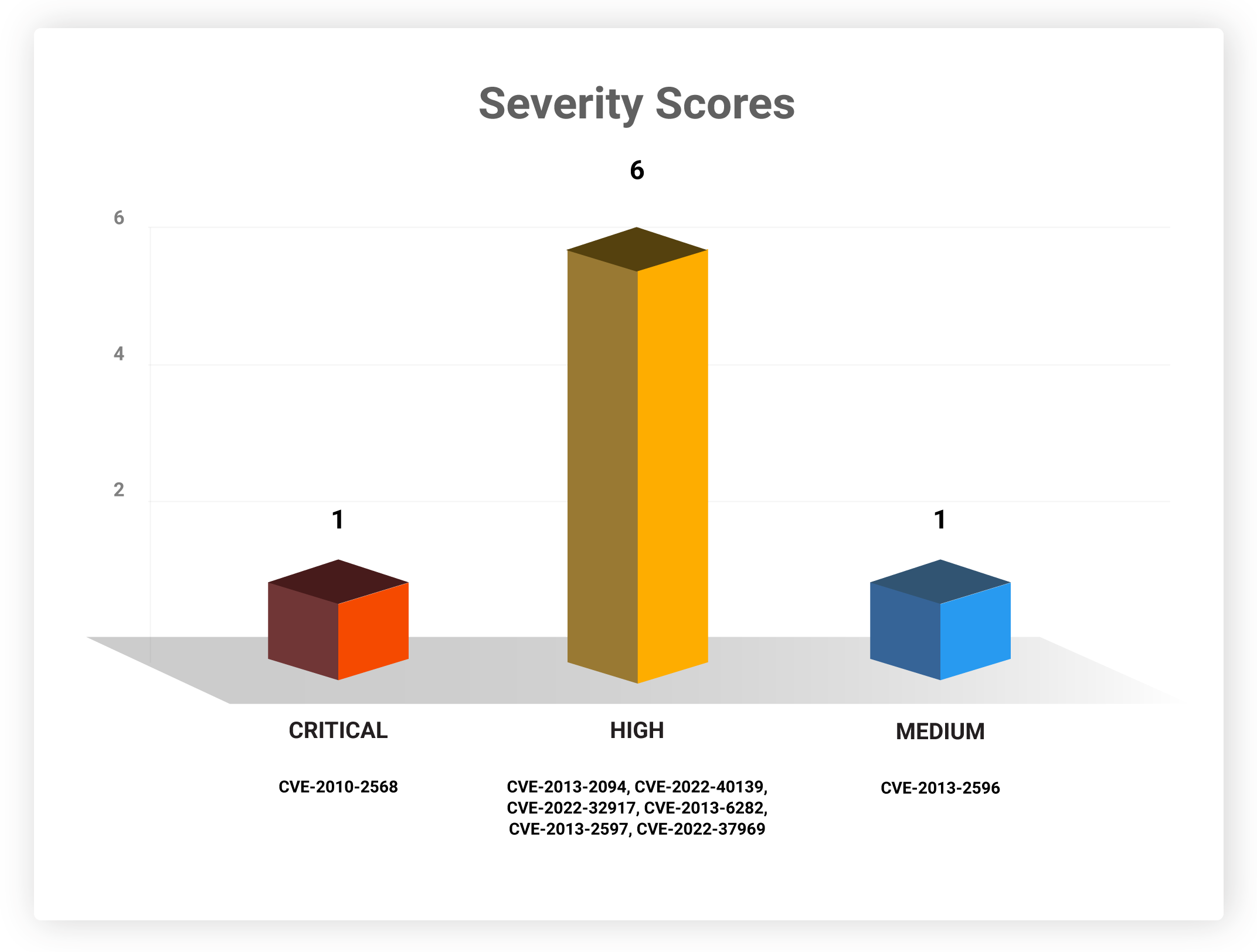
Severity Scores
Patching these vulnerabilities is of high priority, as they rank high and/or critical on the CVSS scoring scale. Exploiting such vulnerabilities will allow attackers to cause maximum damage to their victim networks.
Software Weaknesses
The following CWEs have caused the vulnerabilities that need to be patched this week. From our analysis, some CVEs have more than one software weakness which allows multiple initial access entry points.
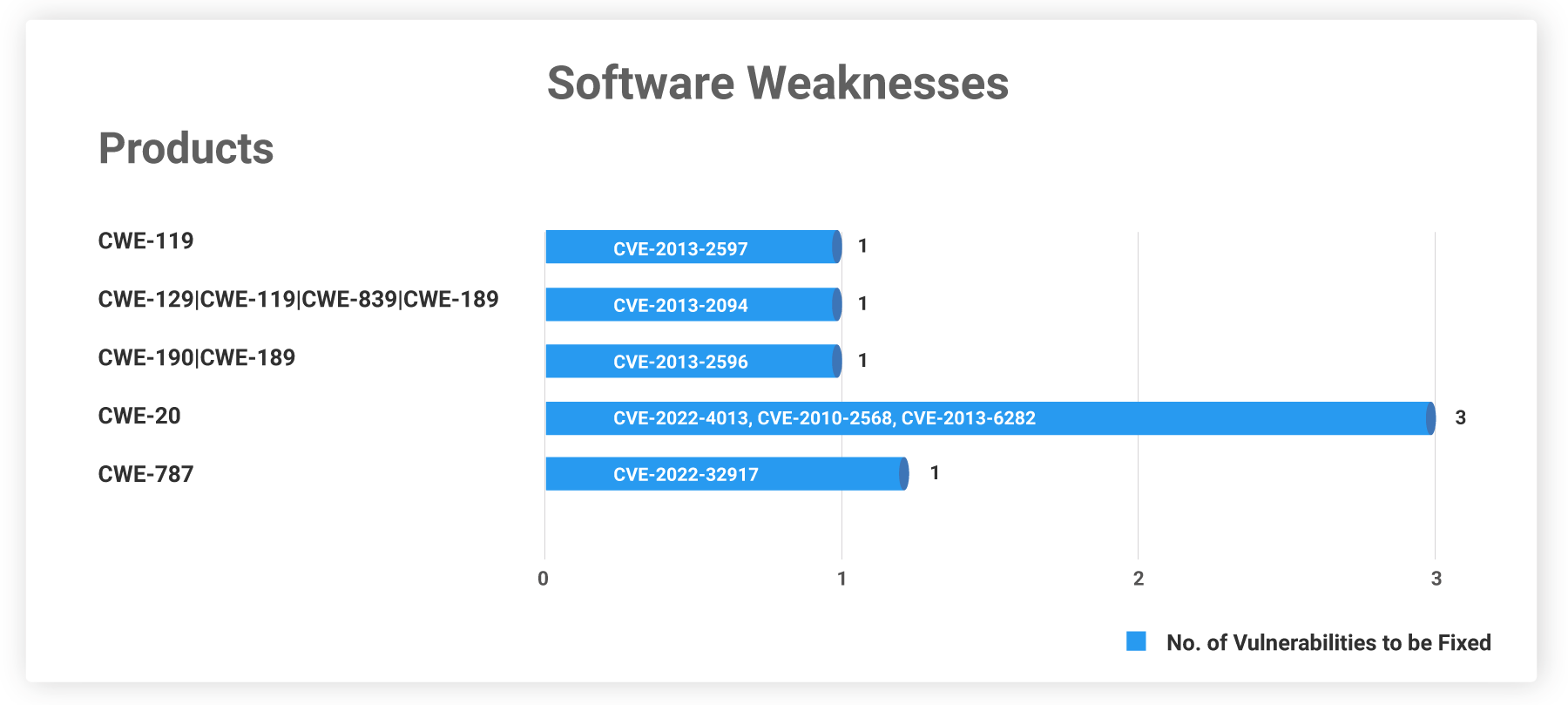
CVE-2022-37969 does not have any CWE associated with it.
Table: DHS CISA KEVs
We urge organizations to implement patches for these CVEs at the earliest. With CSW’s threat-based approach and vulnerability intelligence, security teams can prioritize the threats, including all KEVs, and minimize their attack surface.
For the latest news regarding vulnerabilities that are exploited and critical threats, read our blog on Weekly Threat Intelligence.