The US Cybersecurity and Infrastructure Security Agency raises the alarm about known exploited vulnerabilities by adding new CVEs to the growing list of the KEV catalog. CISA added 22 new CVEs between September 08, 2022, and September 15, 2022.
In this blog, we bring you all the DHS CISA KEVs that need to be prioritized for patching this week (September 12 to September 16, 2022).
Why are these vulnerabilities important?
CISA’s KEVs is a collection of vulnerabilities that have been exploited by threat actors time and again. If left unpatched, these become low-hanging fruits that attackers can easily misuse.
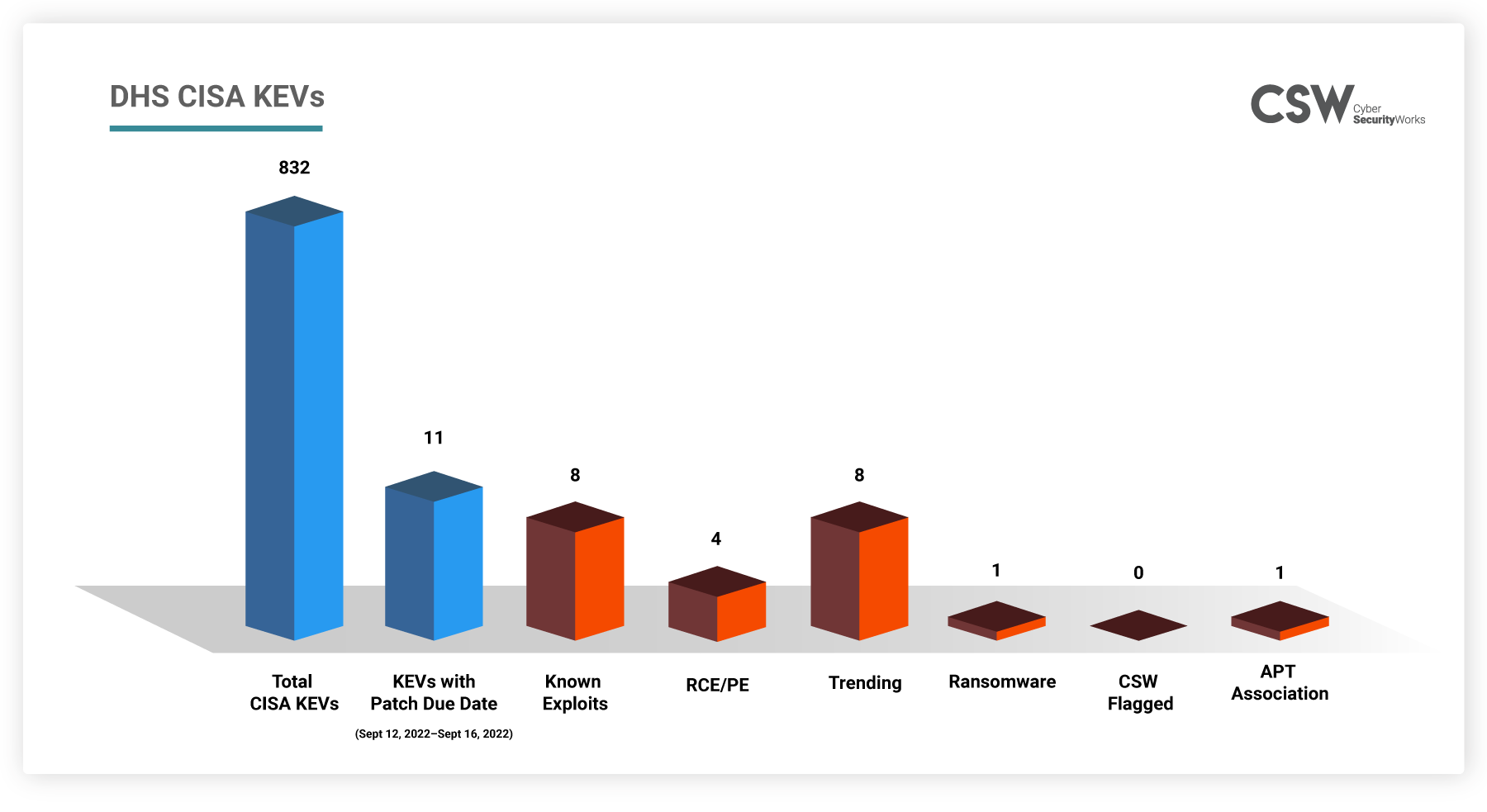
A total of 11 known exploited vulnerabilities from the DHS CISA catalog should be fixed by federal agencies this week before September 12 to September 16, 2022. We urge all organizations to address these to safeguard their networks from attacks.
We further analyzed these 11 KEVs and found that:
-
For 73% of vulnerabilities, exploit codes are readily available in the public domain. Attackers getting a hold of such exploits can easily breach networks and exploit exposures to penetrate deeper into the networks. Of these, 4 are of the highest class of exploits that allow for remote execution of custom code.
-
The trending vulnerabilities are high on the radar of threat actors and attackers are constantly scouting the web for unpatched instances of such vulnerabilities.
-
CVE-2022-26352, in particular, has associations with both ransomware and APT groups, making it highly dangerous. If exploited, organizations stand to lose their reputation, part with sensitive data, or even be locked out of their own systems.
How Far Back Do They Go?
Although all these CVEs are relatively new, they have 8 exploits so far, which make them dangerous.
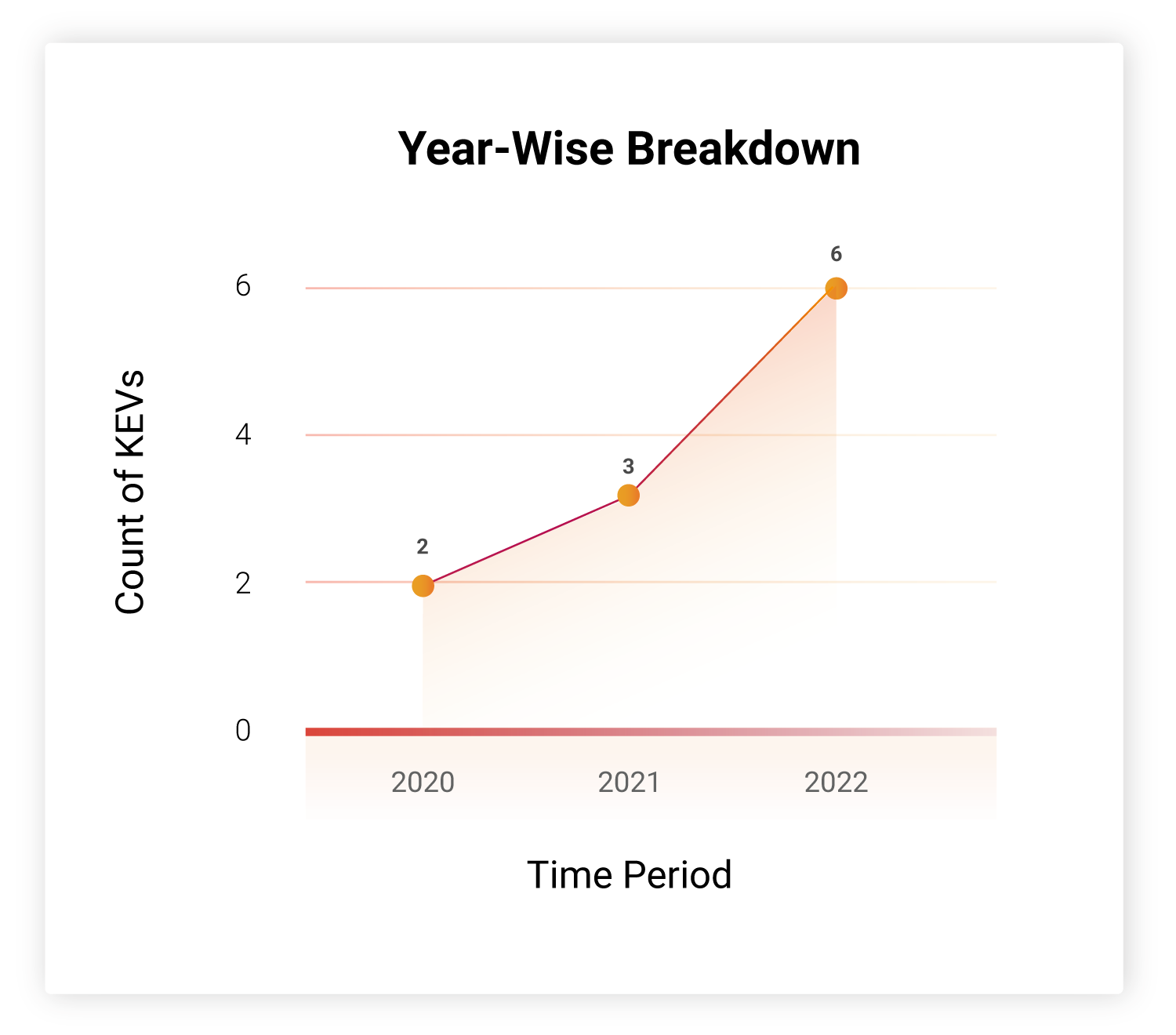
This is a clear indication of how fast attackers are progressing today developing exploits for new vulnerabilities as they appear, sometimes even before organizations are made aware of the existence of such a flaw.
Our ransomware reports called out such vulnerabilities that were exploited as zero days, even before the vendor was aware of its presence. Read here to know more about our research.
Which Vendors Are Affected?
Apache is the worst affected with two critical vulnerabilities – an authentication bypass and an improper resource initialization vulnerability. There are 9 other vendors that have vulnerabilities in them.
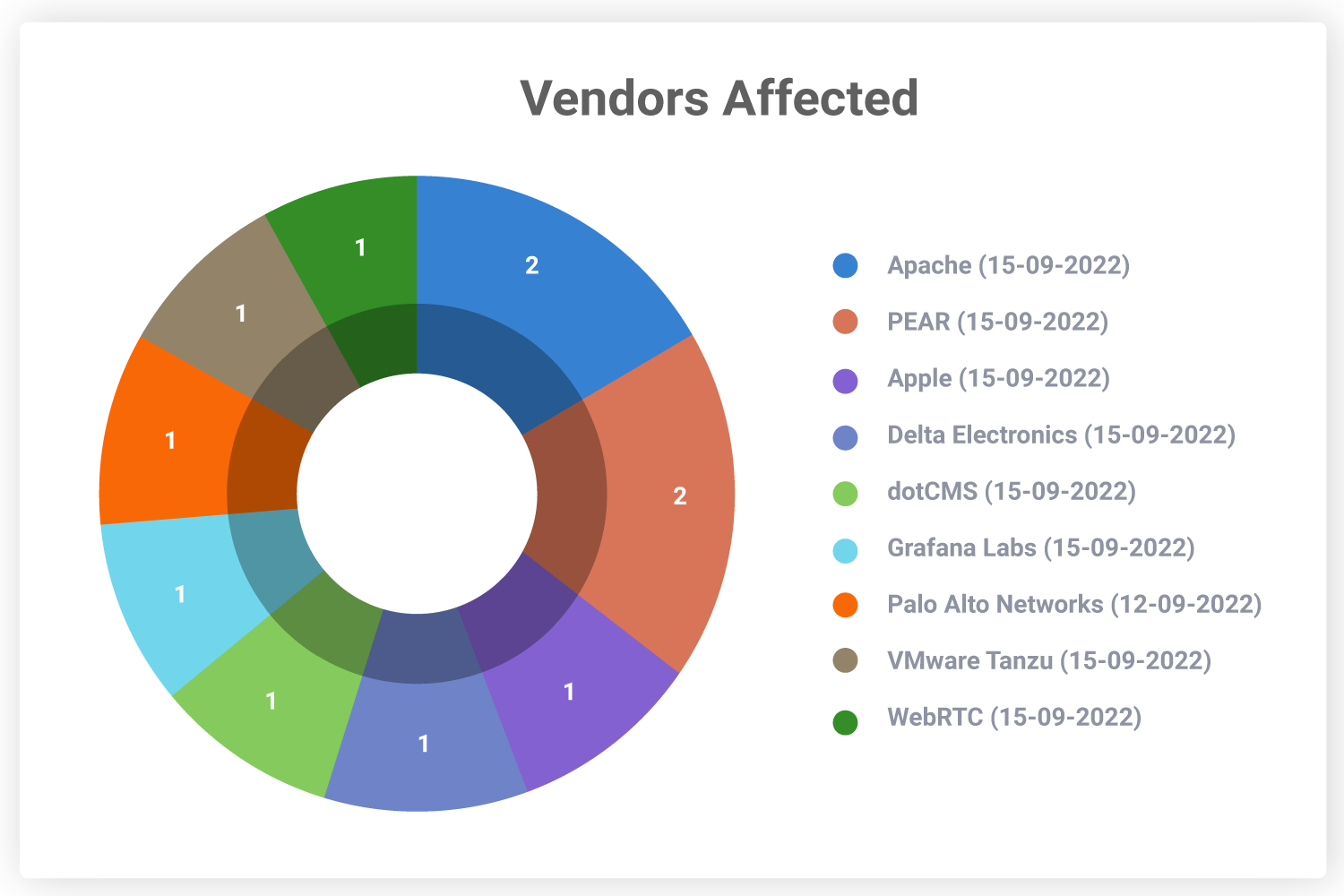
Organizations must keep themselves up to date with these vendor advisories and upgrade their products as and when new patches are released.
Severity Scores
Patching these vulnerabilities is of high priority, as they rank high and critical on the CVSS scoring scale. Exploiting such vulnerabilities will allow attackers to cause maximum damage to their victim networks.
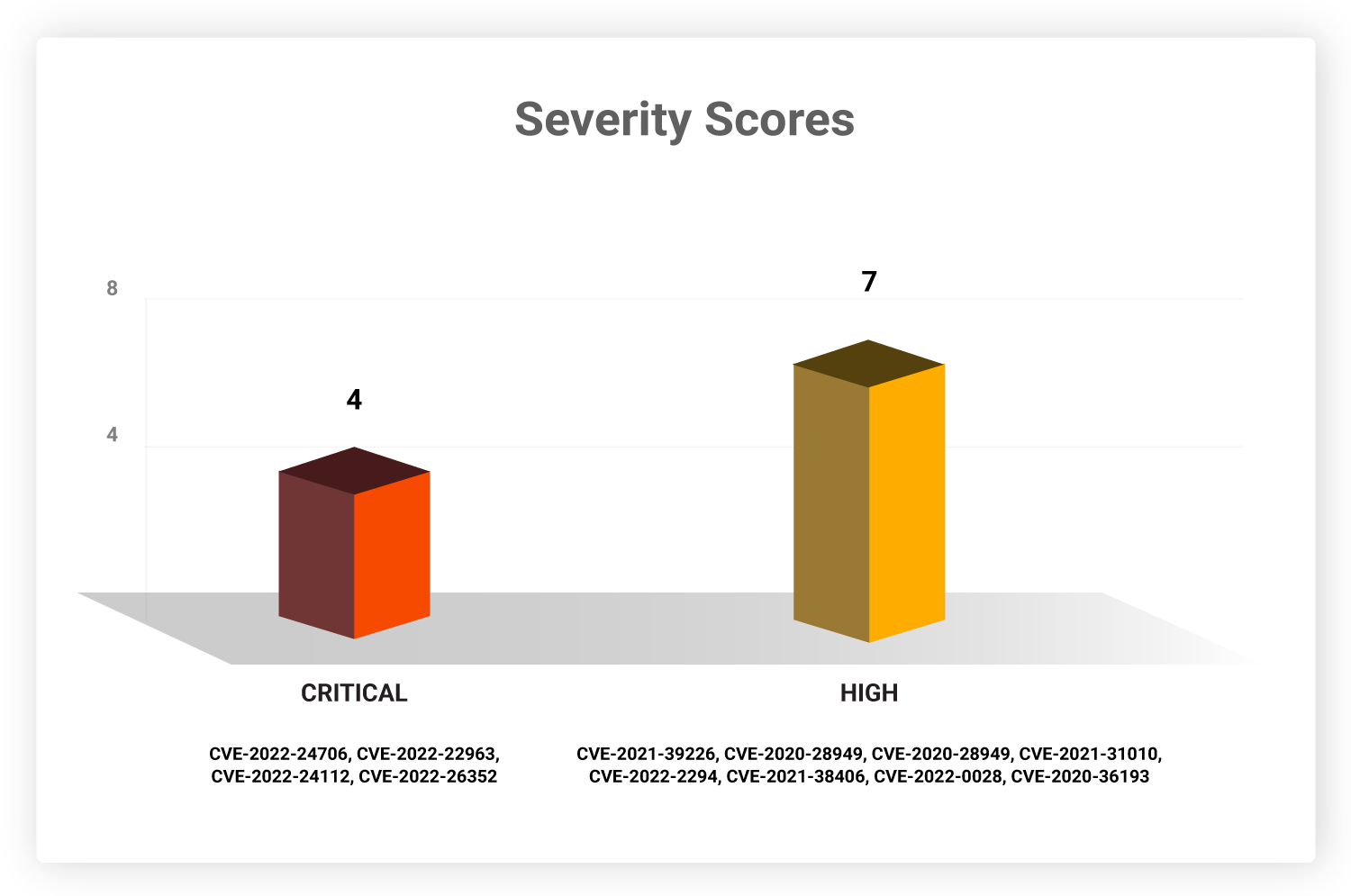
CVE-2022-26352 is associated with the HolyGhost ransomware group that is actively exploiting organizations across the globe. Organizations must give importance to this threat context and ensure the vulnerability is patched without delay.
Software Weaknesses
The following CWEs have caused the vulnerabilities that need to be patched this week. These are the weaknesses developers should be aware of and work to overcome while making their products.
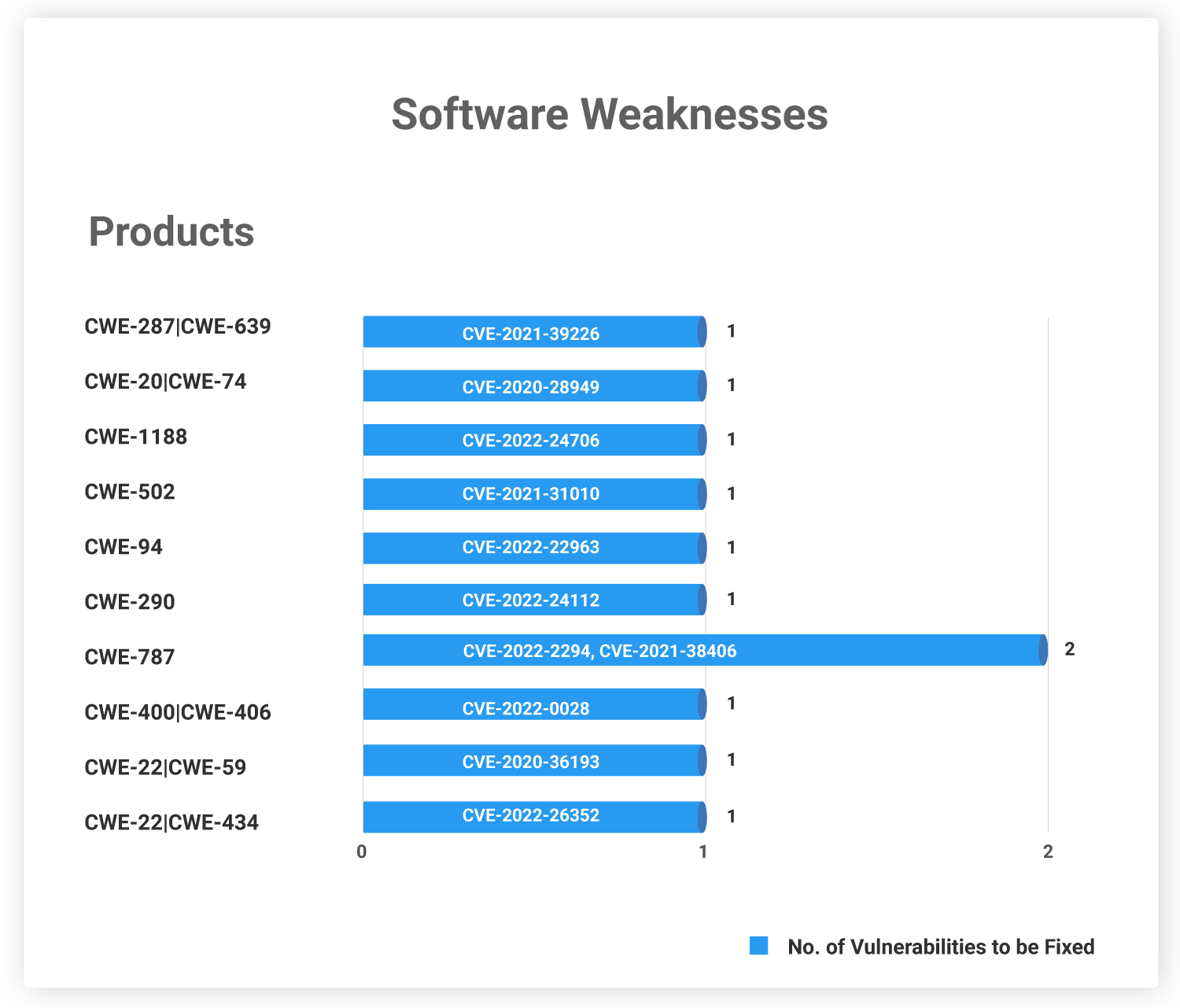
Table: DHS CISA KEVs
We urge organizations to implement patches for these CVEs at the earliest. With CSW’s threat-based approach and vulnerability intelligence, security teams can prioritize the threats, including all KEVs, and minimize their attack surface.
For the latest news regarding vulnerabilities that are exploited and critical threats, read our blog on Weekly Threat Intelligence.









