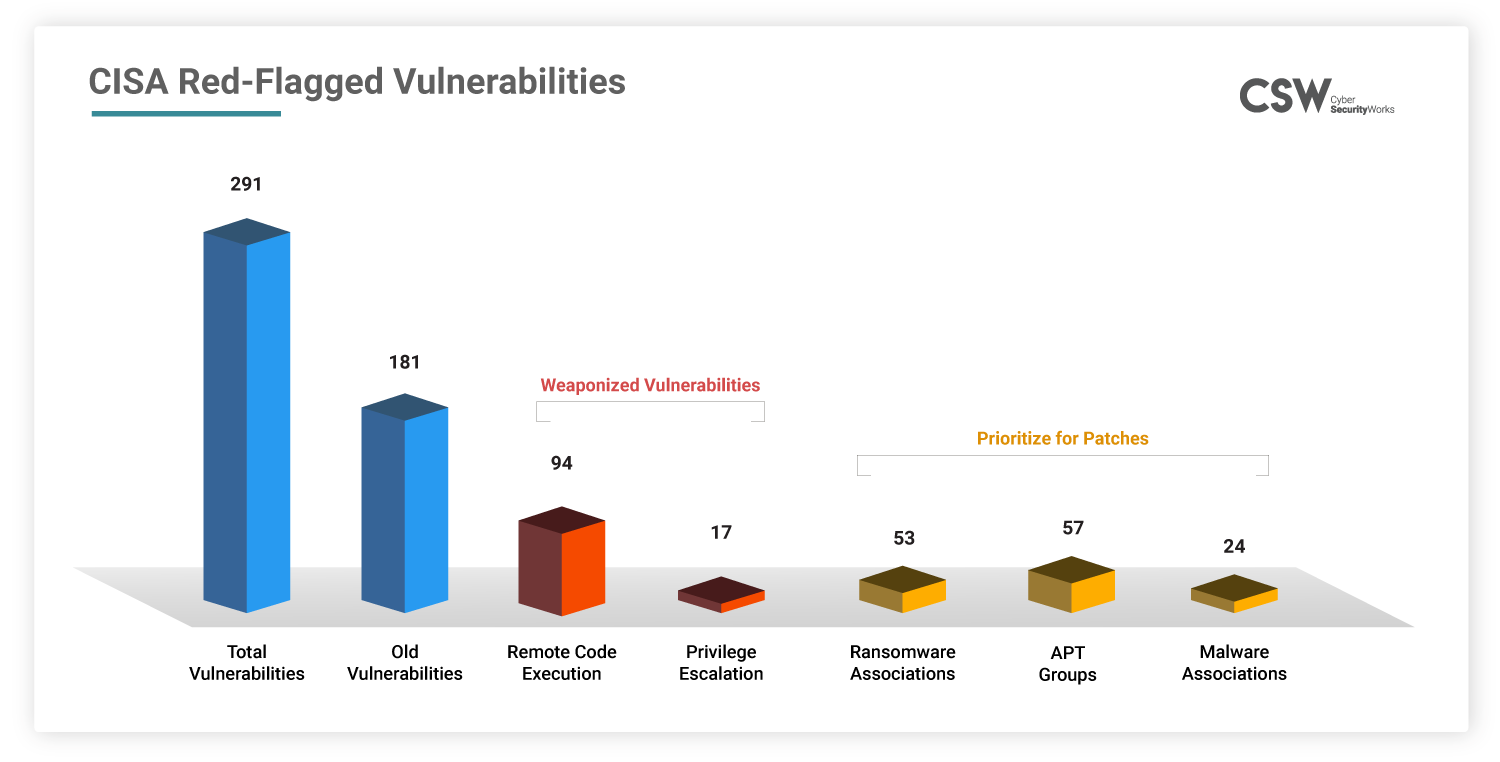
On November 3, 2021, the US Cybersecurity and Infrastructure Security Agency (CISA) issued a new Binding Operational Directive urging public entities to fix Known Exploited Vulnerabilities (KEV) within defined time frames. This catalog consists of 291 vulnerabilities dating back to 2010 that threat actors have been actively exploiting in attacks.
In a recent update to this catalog, CISA has set a deadline for federal agencies to apply fixes for the newly added five security flaws in Qualcomm, MikroTik, Zoho, and the Apache Software Foundation.
We have analyzed these vulnerabilities and have spotlighted their threat associations that ought to be fixed on priority.
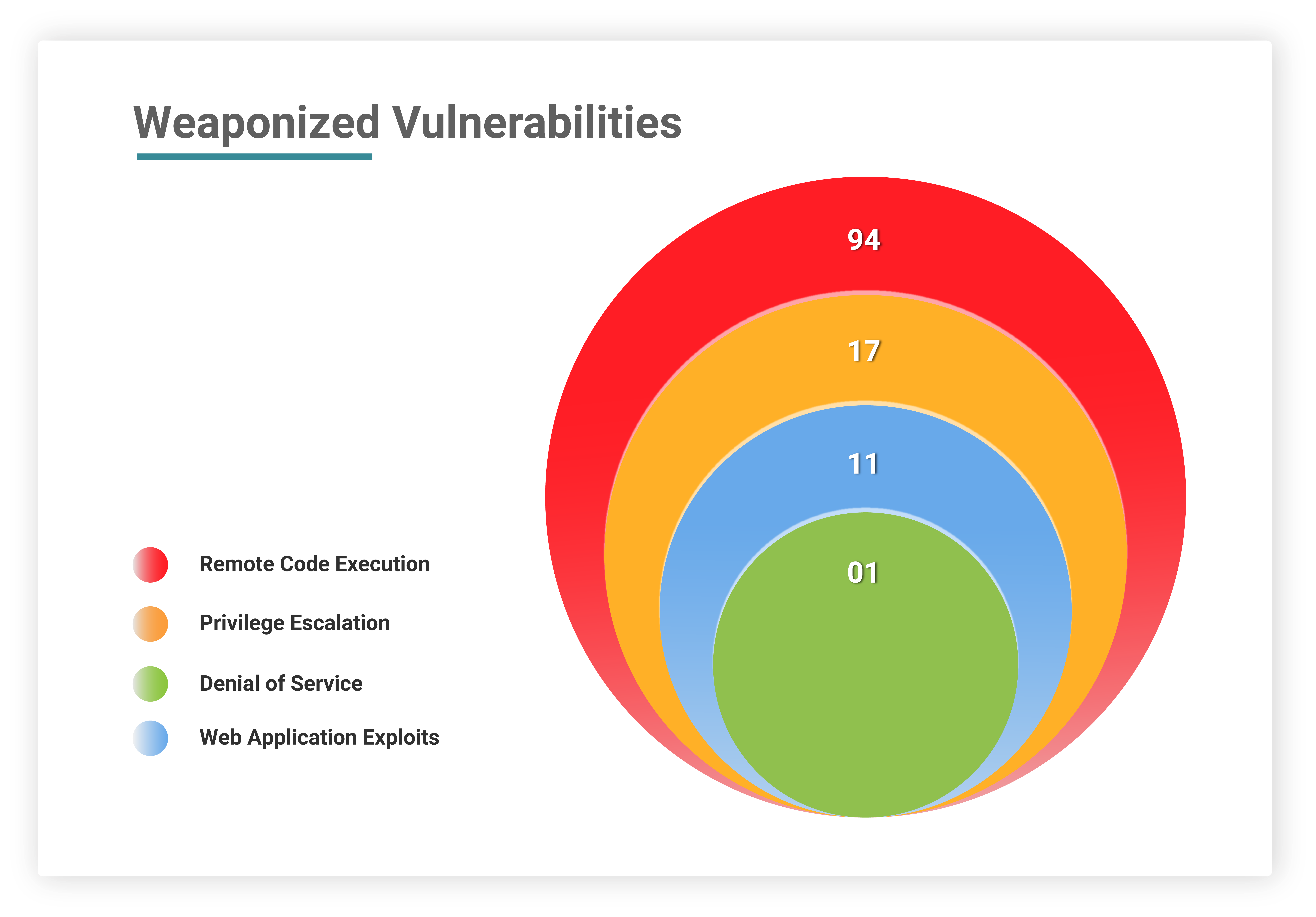
Weaponized Vulnerabilities
According to CISA, these 291 CVEs have been weaponized with known exploits. Here is our analysis:
-
53 CVEs are associated with multiple ransomware families.
-
57 CVEs are linked to APT groups.
-
24 CVEs are correlated to malware threats.
-
94 CVEs are classified as Remote Code Execution.
-
17 CVEs have Privilege Escalation capabilities.
-
1 CVE has denial-of-service capabilities.
-
11 CVEs are web application exploits.
-
167 CVEs are high severity, 118 are medium severity, and 5 are low severity.
Old Vulnerabilities
CISA’s catalog included 181 old vulnerabilities that were found to be active during the past decade.
-
35 CVEs are associated with multiple ransomware families.
-
37 CVEs are linked to APT groups.
-
20 CVEs are correlated to malware threats.
-
47 CVEs are classified as Remote Code Execution.
-
16 CVEs have Privilege Escalation capabilities.
-
118 CVEs are high severity, 60 are medium severity, and 3 are low severity.
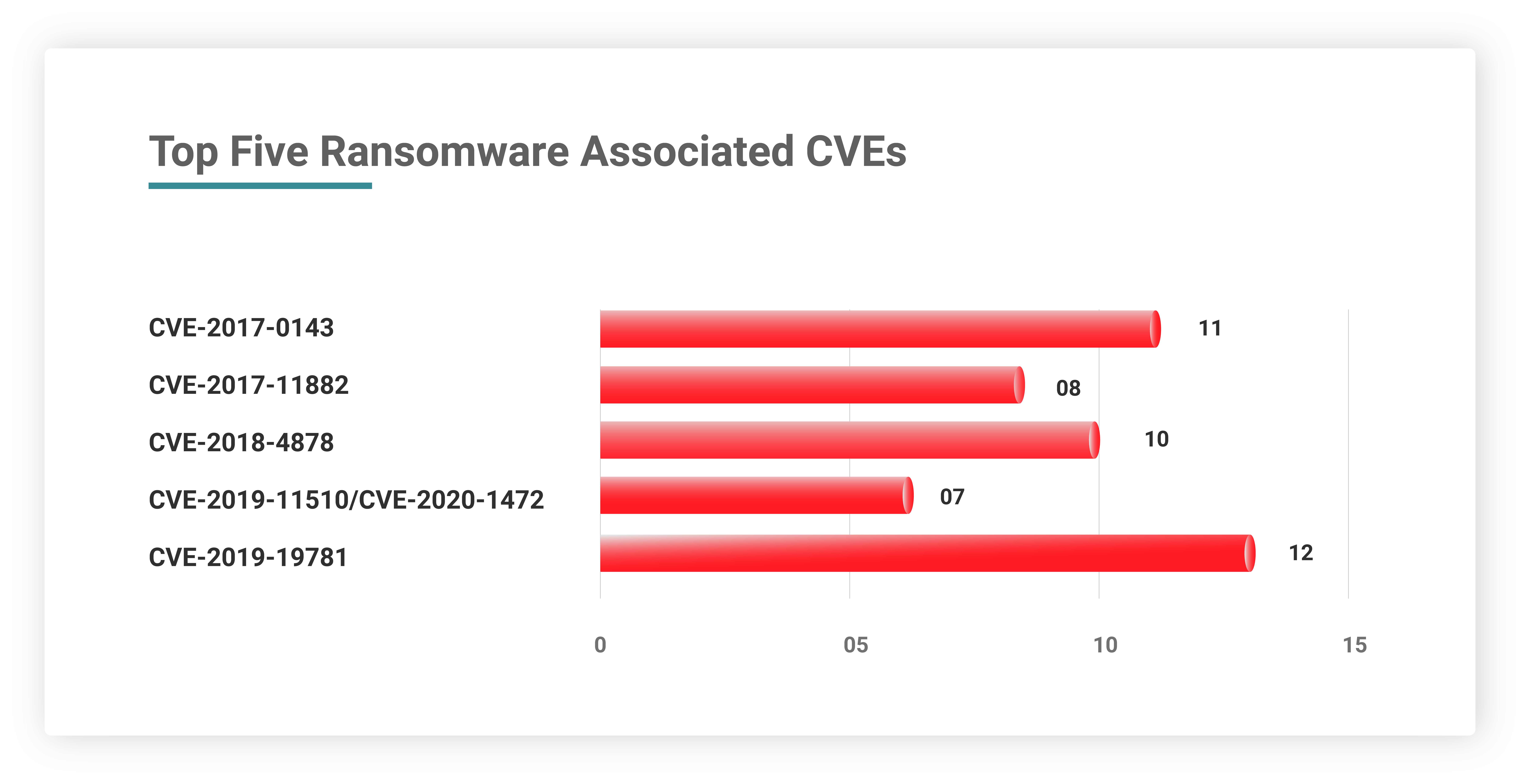
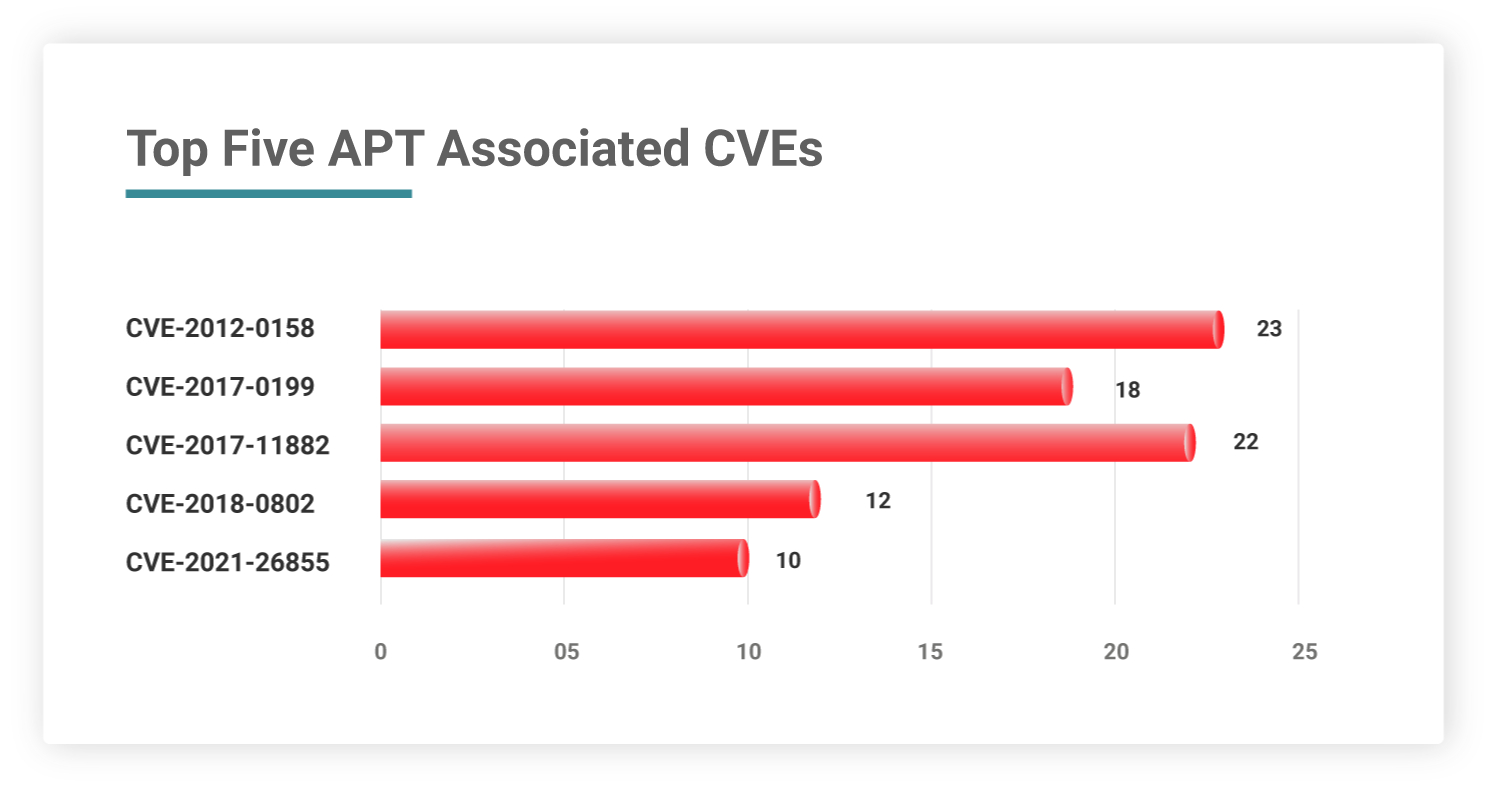
Top Five Ransomware and APT Groups
CVE-2019-19781 is a Remote Code Execution vulnerability that has been identified as one of the most popular among attackers, with 12 different ransomware variants. This vulnerability has a CVSS score of 9.8 and is accredited with the weakness enumeration, CWE-22, which is in the Top 10 software vulnerabilities on the MITRE 2021 CWE Top 25 list.
In addition to the warnings issued by the NSA, FBI, and CISA, this significant CVE has been detected in multiple cyber incidents in 2021.
CVE-2012-0158 is one of the old vulnerabilities that has been associated with 23 Advanced Persistent Threat (APT) groups. This CVE holds a severity score of 9.3 and is categorized under CWE-94, leading to Improper Control of Generation of Code. CWE-94 has been covered in the 2021 CWE Top 30 and is also listed in the OWASP Top 10 2021 (A3).
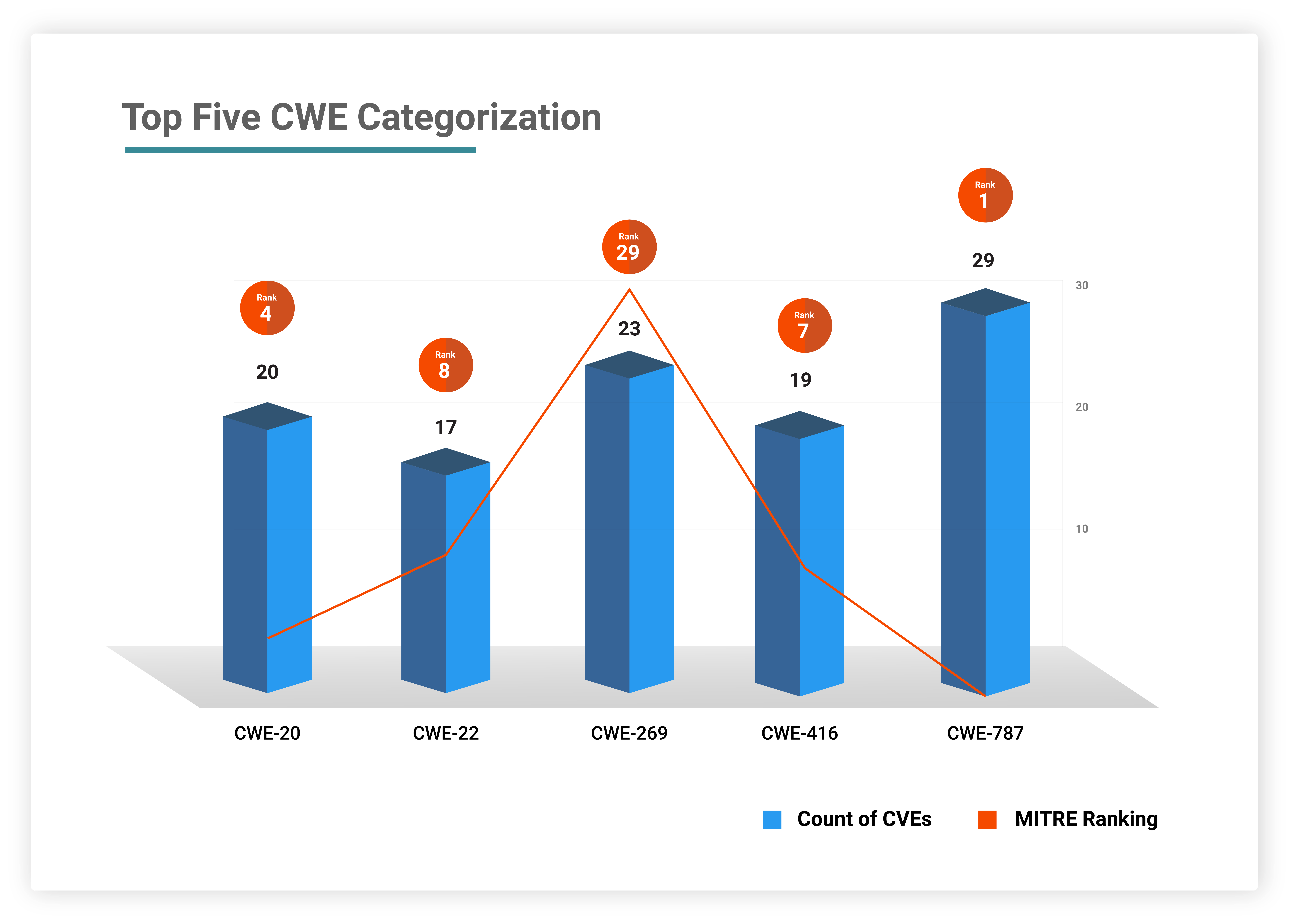
Common Weakness Enumeration (CWE)
Based on the CWE categorization, the Top Five CWEs covered the highest number of CVEs grouped under the Top 30 Most Dangerous Software Weaknesses of 2021.
Latency Analysis
Securin’s analysts studied the latency details and listed out the following:
-
The National Vulnerabilities Database (NVD) waited an average of 122 days from the patch disclosure to reveal the CVE information for 34% of the red-flagged vulnerabilities by CISA.
-
13 CVEs were exploited even before they were published to the NVD.
-
An exploit was released on the day of the disclosure in the NVD for five vulnerabilities.
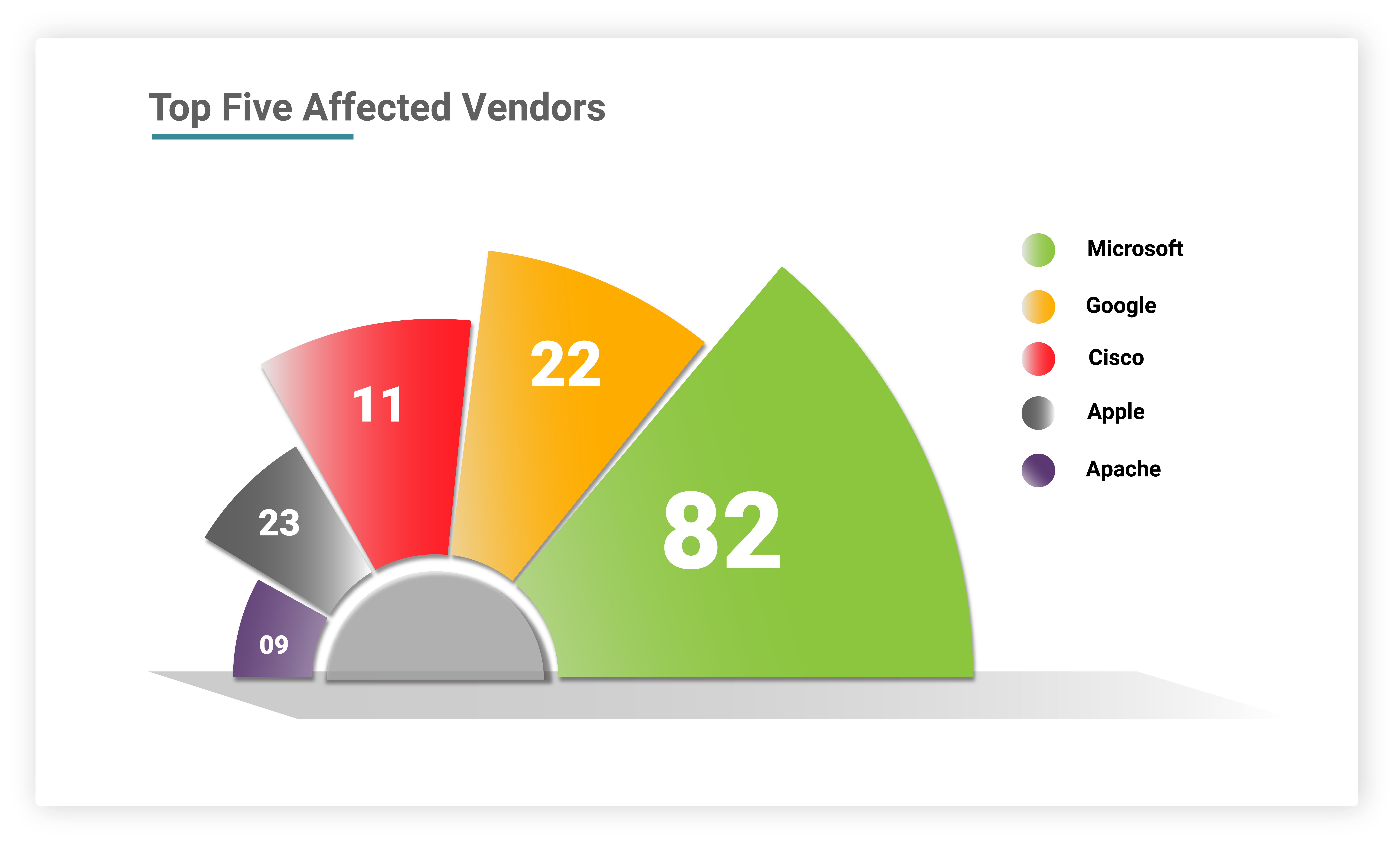
Affected Vendors
The KEVs listed out by CISA had impacted 68 vendors, including Microsoft, Apple, Oracle, Adobe, Atlassian, Fortinet, and other organizations. A notable statistic is that 82 vulnerabilities from the overall list are attached to Microsoft.
Running Out of Time!
The patching deadline for many exploited vulnerabilities in the catalog published by CISA is set to May 3, 2022. There is no doubt that the catalog’s publication provides a chance for private organizations to evaluate their systems and address the flaws.
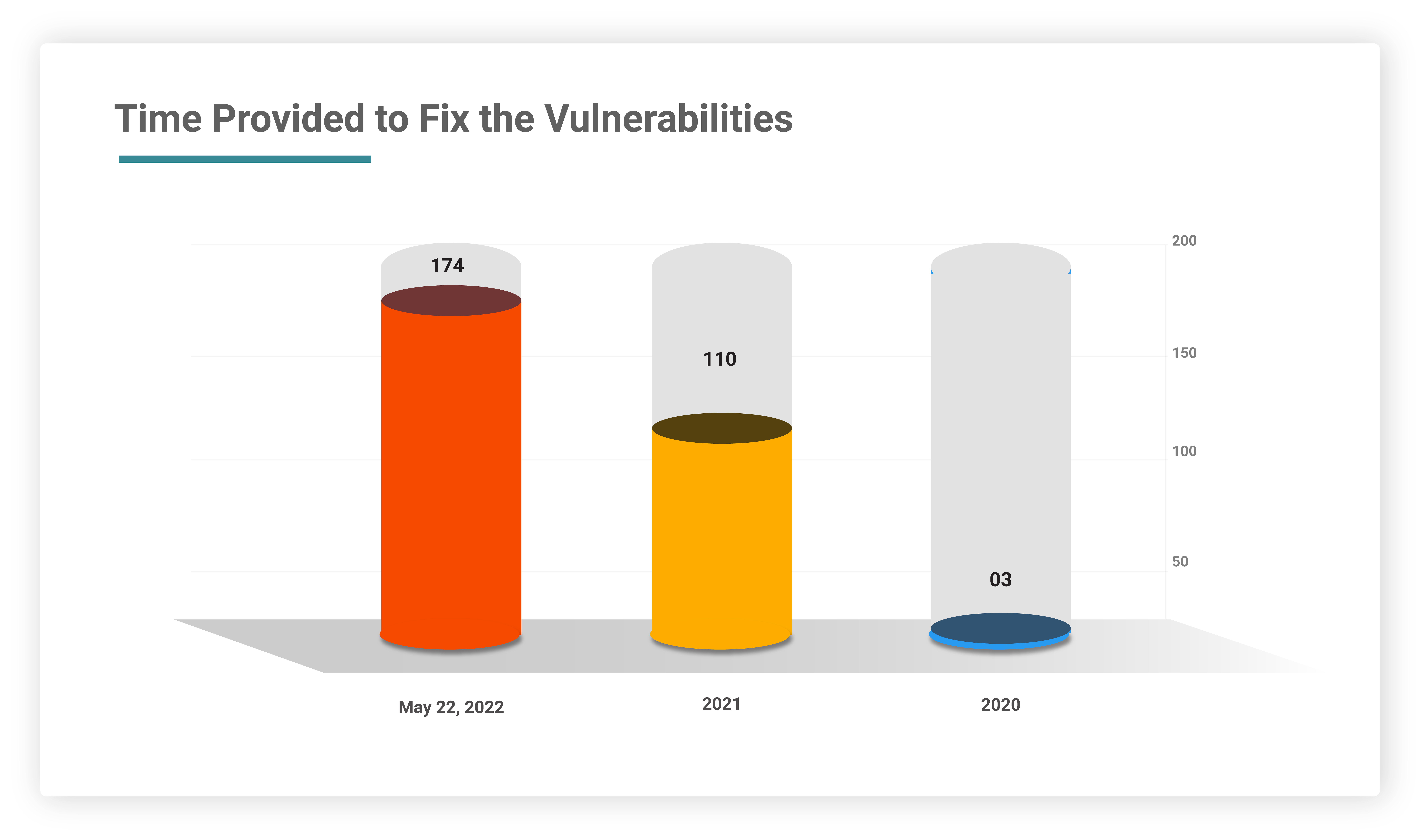
Table: CISA Listed Known Exploited Vulnerabilities
The new directive comes on the heels of the high-level concern in the government and private sector over recent attacks, such as the ones involving SolarWinds and Kaseya and those exploiting Microsoft Exchange, Fortinet, Zoho, and Pulse VPN over the past year. The cyberattacks impacted a wide range of companies, and many of them contained vulnerabilities that organizations should have been aware of and patched long ago.
CISA will update the catalog periodically with information on any new vulnerabilities that pose a risk to the federal government or the vulnerabilities that may be exploited.









