What are the MITRE Kill Chain Vulnerabilities?
A MITRE kill chain is a model where each stage of a cyberattack can be defined, described, and tracked, visualizing each move made by the attacker. Using this framework, security teams can stop an attack and design stronger security processes to protect their assets.
This framework also has detailed procedures for each technique and catalogs the tools, protocols, and malware strains used in real-world attacks. Consequently, security researchers use these frameworks to understand attack patterns and focus on detecting exposures, evaluating current defenses, and tracking attacker groups.
Securin’s ransomware research, elucidated further in the Ransomware Spotlight Report 2023, has discovered 57 extremely dangerous vulnerabilities associated with ransomware that can be exploited as a complete MITRE ATT&CK kill chain, from initial access to exfiltration.
A total of 81 unique products across 20 major vendors, such as Microsoft, SonicWall, Apache, Atlassian, VMware, F5, and Oracle were identified by Securin experts.
ATT&CK Kill Chain Vulnerabilities
Our analysis of the 57 dangerous vulnerabilities produced the following findings:
49 of the 57 vulnerabilities already feature in the DHS CISA KEV catalog.
32 vulnerabilities are rated critical as per their CVSS v3 scores, while 20 are rated high, and 5 have no ratings available.
Securin’s Vulnerability Intelligence platform assigned 34 of 57 vulnerabilities a predictive score of 38.46, a critical severity rating, while 23 were assigned high-severity scores, providing an insight into the likelihood of the vulnerabilities being exploited in the wild.
33 vulnerabilities are categorized as remote code execution (RCE), 16 vulnerabilities are categorized as privilege escalation (PE), 5 CVEs are classified as DOS, 24 vulnerabilities are WEBAPP, and 34 CVEs have both RCE and PE issues.
-
CVEs with the highest ransomware associations include:
CVE-2016-0034 has the highest number of ransomware associations with 43
Closely followed by CVE-2012-1723 at 42
CVE-2021-34473 and CVE-2021-34523 are tied at 11 each
CVE-2020-1472 has 9 associations
Securin Recommends DHS CISA to Add 8 Kill-Chain Vulnerabilities to its KEV Catalog
Eight of the 57 MITRE kill-chain vulnerabilities are not in the CISA KEV catalog. Our Securin experts recommend CISA to add the following to the KEVs:
CVE-2016-10401 – A vulnerability affecting Zyxel home routers
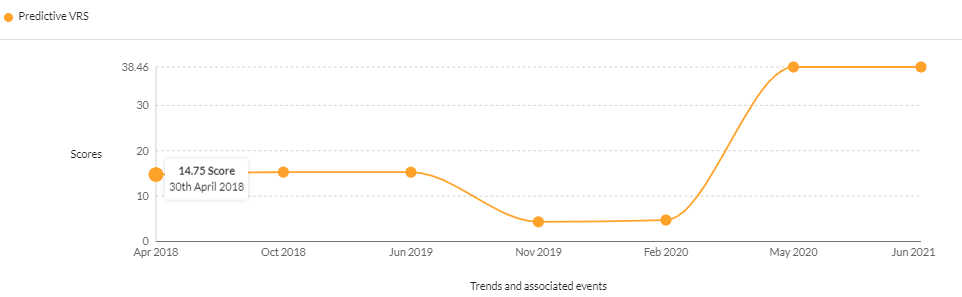
CVSS v2 – 9.00 | CVSS v3 – 8.80 | Securin VRS – 8.48
- CVE-2017-6884 – A command injection vulnerability affecting Zyxel home routers
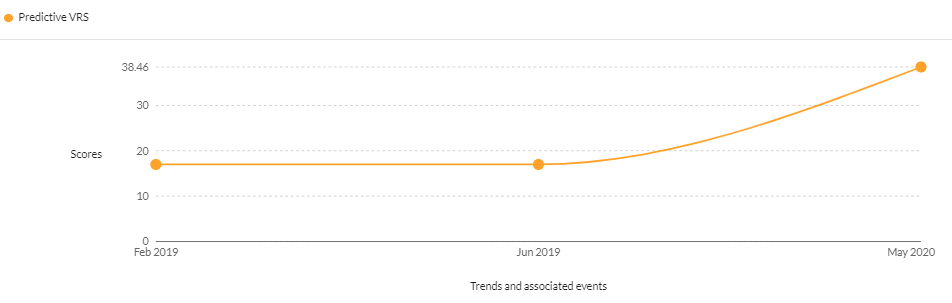
CVSS v2 – 9.00 | CVSS v3 – 8.80 | Securin VRS – 9.39
- CVE-2018-8389 – A Scripting Engine Memory Corruption Vulnerability affecting Internet Explorer
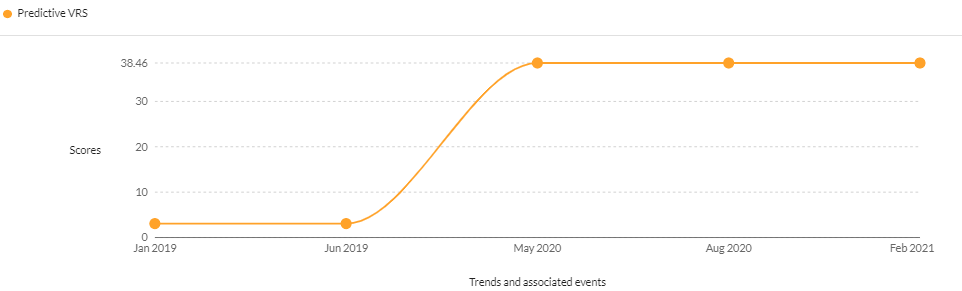
CVSS v2 – 7.60 | CVSS v3 – 7.50 | Securin VRS – 7.76
- CVE-2019-2729 – Vulnerability in the Oracle WebLogic Server component
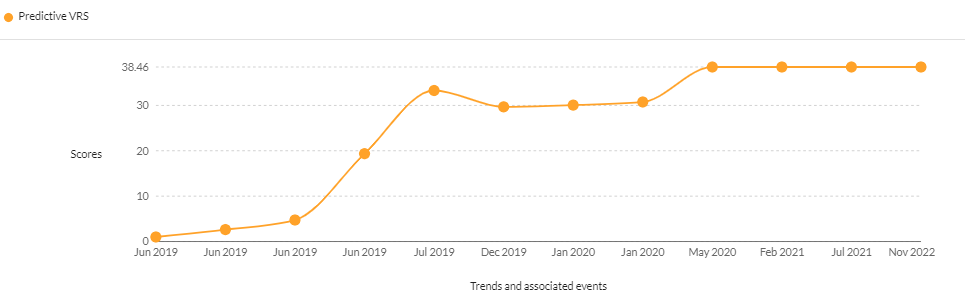
CVSS v2 – 7.50 | CVSS v3 – 9.80 | Securin VRS – 9.98
- CVE-2020-1210 – An RCE vulnerability in Microsoft SharePoint
CVSS v2 – 6.50 | CVSS v3 – 8.80 | Securin VRS – 8.47
- CVE-2020-16875 – An RCE vulnerability in Microsoft Exchange server
CVSS v2 – 9.00 | CVSS v3 – 7.20 | Securin VRS – 9.08
- CVE-2020-36195 – SQL injection vulnerability affecting QNAP NAS devices
CVSS v2 – 7.50 | CVSS v3 – 9.80 | Securin VRS – 8.79
- CVE-2021-31206 – Microsoft Exchange Server RCE vulnerability
CVSS v2 – 7.90 | CVSS v3 – 8.00 | Securin VRS – 8.36
Auld Lang Syne: Ghosts of the Past
Securin analysts identified 25 vulnerabilities that are old, dating from between 2012 and 2019. The oldest CVEs belong to Oracle. CVE-2012-1710, CVE-2012-1723 and CVE-2012-4681 affect multiple products apart from Oracle. CVE-2012-1723 and CVE-2012-4681 both have CVSS v3 scores of 10.0.
While all 25 have multiple ransomware associated with them, CVE-2016-0034 (Microsoft) takes the cake with a whopping 43 ransomware associations, followed closely by CVE-2012-1723 with 42.
Of the 25 old vulnerabilities, 17 CVEs are categorized as RCE and RCE/PE respectively, eight are privilege escalation vulnerabilities, two are categorized as DOS, and 12 as Webapp.
The majority of the old vulnerabilities affect two specific vendors – eight CVEs plague 70 unique Oracle products, while seven CVEs affect 51 unique Microsoft products.
Top 5 Kill Chain CVEs with Highest Number of Products Affected
CVE ID |
CVE Description |
Number of Products Affected |
Apache Log4J |
379 |
|
Zoho ManageEngine ADSelfService Plus |
170 |
|
Pulse Secure Pulse Connect Secure |
97 |
|
BIG IP RCE |
84 |
|
QNAP SQL Injection |
57 |
Top 5 Products Affected by the Kill Chain Vulnerabilities
|
Vendor Name |
Number of Products Affected |
Worst Affected Product(s) |
|
Microsoft |
23 |
Microsoft Exchange Server |
|
Oracle |
16 |
JRE, JDK and WebLogic Servers |
|
F5 |
14 |
– |
|
Apache |
3 |
Log4J, Struts |
|
Atlassian |
3 |
Confluence Server |
Top 5 CWEs of the Kill Chain Vulnerabilities
Securin experts analyzed the weakness category of the vulnerabilities and found five CWEs that are ranked among the top 10 in MITRE’s top 40 dangerous weaknesses (2022).
Top 10 MITRE CWEs (and Count of Vulnerabilities) | ||||
|
CWE-20 11 |
CWE-22 7 |
CWE-787 4 |
CWE-89 4 |
CWE-78 4 |
CWE-20, an improper input validation vulnerability, has the maximum number of CVEs categorized within it. CWE-22, an Improper Limitation of a Pathname to a Restricted Directory or ‘Path Traversal’ vulnerability, has the second highest number of CVEs. The other noteworthy weaknesses, CWE-787, CWE-89 and CWE-78, are rated 1st, 3rd and 6th in the list of MITRE’s Most Dangerous Software Weaknesses.
Scanner Detection Gone Awry
Three kill chain vulnerabilities are especially dangerous, thanks to their evasive nature from the roving eyes of common scanners like Qualys, Nessus and Nexpose. Let us take a deeper dive into these vulnerabilities:
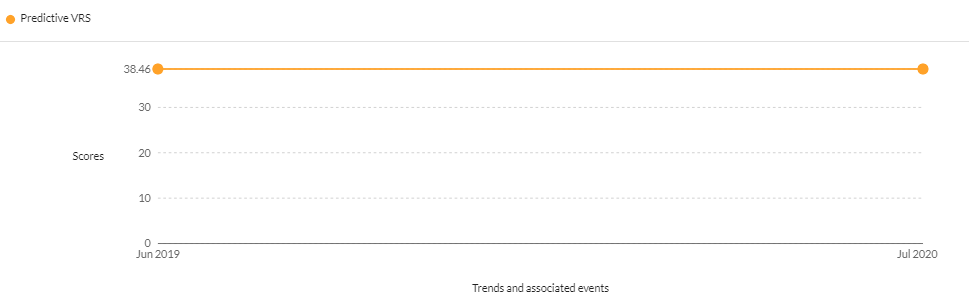
- CVE-2017-18362– ConnectWise ManagedITSync integration through 2017 for Kaseya VSA is vulnerable to unauthenticated remote commands that allow full direct access to the Kaseya VSA database. The Securin Vulnerability Intelligence platform assigned it a score of 38.46, deeming it extremely critical since June 2019. Though the vulnerability was exploited as far back as November 2019 by GandCrab ransomware group, DHS CISA added the CVE to the KEV catalog in May 2022. Securin experts had called out the vulnerability and its inclusion in the KEV catalog in our Ransomware Spotlight Report Q3.
CVSS v2 – 7.50 | CVSS v3 – 9.80 | Securin VRS – 8.80
CVE-2017-18362 was initially assigned a CVSS v2 score of just 7.50, later to be revised to a critical score of 9.80 (CVSS v3). The Securin VRS definitive score of 8.80 is due to the reduced frequency of attacks exploiting the vulnerability. However, it is important to note that the vulnerability is not detectable by popular scanners, making it difficult for security teams to patch.
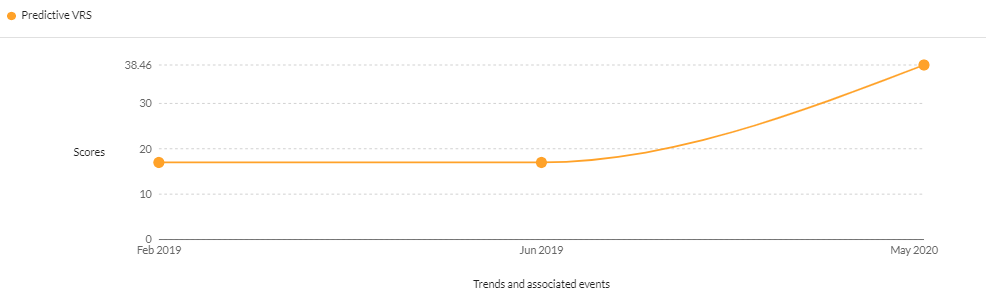
- CVE-2017-6884 – A command injection vulnerability was discovered on the Zyxel EMG2926 home router with firmware V1.00 (AAQT.4)b8. The vulnerability was assigned a critical score of 38.46 by Securin’s VI platform in May 2020. Despite being six years old, being associated with Ryuk ransomware, being invisible to popular scanners and having a critical severity, the DHS CISA is still yet to add the vulnerability to the KEV catalog.
CVSS v2 – 9.00 | CVSS v3 – 8.80 | Securin VRS – 9.39
CVE-2017-6884 received a critical CVSS v2 score of 9.00, only to be downgraded to a CVSS v3 score of 8.80, in spite of its dangerousness. Thus, the Securin VRS reaffirms the criticality of the issue with a score of 9.39.
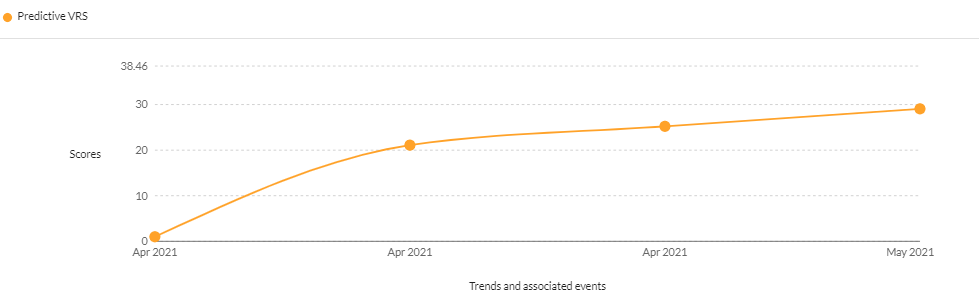
- CVE-2020-36195– An SQL injection vulnerability reported to affect QNAP NAS running Multimedia Console or the Media Streaming add-on. The vulnerability was assigned a critical score of 38.46 by Securin’s VI platform in July 2021. Despite being three years old, having been associated with QLocker ransomware and eCh0raix ransomware, being undetectable to popular scanners, having a critical severity, and being actively trending, the DHS CISA is still yet to add the vulnerability to the KEV catalog.
CVSS v2 – 7.50 | CVSS v3 – 9.80 | Securin VRS – 8.79
CVE-2020-36195 received a high severity CVSS v2 score of 7.50, only to be upgraded to a CVSS v3 score of 9.80. In spite of the danger it poses, Securin VRS assigns it a high score of 8.79 owing to the reduced chatter on hacker forums, thereby reducing its likelihood of being attacked.
In our Ransomware Report Q2-Q3, Securin analysts noted and warned about a flawed open source code used in Oracle products. Since the DHS CISA KEV catalog does not feature the trending critical vulnerability, CVE-2019-2729, Securin experts emphasized how important it is to add to the catalog. Oracle, on the other hand, used the same code in newer products in spite of the warning, as a result of which, eight new products reflect the same ransomware kill chain vulnerability.
Securin experts have been constantly analyzing vulnerabilities associated with ransomware and mapping each CVE to their corresponding MITRE ATT&CK framework to continuously develop a better understanding into how a threat actor thinks, how they behave, and what attack patterns they deploy. Keeping abreast of the kill chain vulnerabilities by ensuring they are aware of their organization’s complete attack surface.
Securin’s Attack Surface Management platform provides organizations with a hacker’s view of their attack surface, enabling them to see exposures, misconfigurations, shadow IT, and vulnerable products that have ransomware-associated vulnerabilities. Securin ASM helps companies gain visibility into their true attack surface, helping them to improve their security posture through actionable insights by leveraging our excellent threat hunting expertise, and by expediting remediation before being attacked.
Learn more about Securin’s ASM platform.









