Originally Published: Sept 29, 2022
LockBit ransomware is one of the few ransomware groups employing self-spreading malware technology and double encryption. After its recent attacks on the Italian Revenue Agency and digital security giant, Entrust, LockBit has only gained momentum to hunt for its next victim. Read on to learn how to protect your network from LockBit attacks.
One of the most prolific ransomware groups in recent times, LockBit ransomware began its spree of attacks in September 2019. The group is financially motivated and does not shy away from going after bigger, high-profile enterprises and companies.
LockBit is known for many of its unique characteristics: sophisticated technology, triple extortion, heavy marketing to affiliates, and high-severity cyberattacks. LockBit’s attack presence is seen globally, with intermediate breaks during which their ransomware technology receives superior upgrades. Their recent attack strategy and frequency make LockBit a formidable predator and determined adversary in the cyber realm.
In This Blog:
In this blog:
-
LockBit Cheat Sheet
CVEs
Recent Attacks
New Variants
How Does LockBit Attack (MITRE ATT&CK – TTPs)?
How Dangerous is LockBit?
How Can You Detect LockBit in Your Environment (IOCs)?
What Can Organizations Do to Prevent a LockBit Attack?
LockBit: A Cheat Sheet
LockBit is available as Ransomware-as-a-Service (RaaS); affiliates carry out attacks for hire and split the funds between the LockBit developer team and other affiliates.
CVEs
The following CVEs are exploited by the LockBit ransomware gang:
CVE-2018-13379 [WebApp Exploit]
CVE-2018-13379 is a vulnerability in FortiOS and is caused by a path traversal error. Several Advanced Persistent Threat (APT) groups have used this vulnerability to deploy the following ransomware: Pay2Key, Conti, LockBit, Apostle, and Cring.
There are five known exploits for CVE-2018-13379 that can be used to exploit web applications. As it is an old CVE, more functional exploits are likely to be developed, allowing attackers to wage powerful attacks.
CVE-2021-22986 [RCE/PE, WebApp Exploit]
CVE-2021-22986 is a critical unauthenticated, remote command execution vulnerability in F5’s BIG-IP.
It is rated critical with a CVSS v3 severity score of 9.8.
It is an RCE, PE, and web app vulnerability with three known exploits, which makes it very dangerous.
TA505, the Russian threat actor group, also known as Hive0065, has been using the LockBit ransomware payload in its attacks.
CVE-2021-36942
CVE-2021-36942 is a medium-severity Microsoft Windows Server vulnerability.
It has a CVSS V3 severity score of 5.30.
This vulnerability is exploited by both the LockBit and LockFile ransomware groups.
CVE-2020-0787 [RCE, PE, WebApp]
This is a Windows Background Intelligent Transfer Service (BITS) vulnerability.
It is given a CVSS rating of 7.80 and is a high-severity vulnerability.
It is classified as an RCE, PE, and web app exploit. Conti and LockBit ransomware groups use it to gain initial access.
CVE-2022-36537
CVE-2022-36537 is a critical remote code execution (RCE) vulnerability that affects the Java “ZK” Ajax web application framework.
More than 5,000 exposed server manager backup instances are affected by this vulnerability, which could expose companies to supply chain risks.
CVE-2021-20028
CVE-2021-20028 is a critical vulnerability affecting SonicWall products.
- It is caused by CWE-89, an Improper Neutralization of Special Elements used in an SQL Command (SQL Injection).
- It has a CVSS rating of 9.80.
CVE-2021-34473 [RCE, PE, WebApp, Other]
This is a Microsoft Exchange Server remote code execution vulnerability.
It is exploited by ChamelGang, TR, Bronze Starlight, Tropical Scorpius, DEV-0270, OilRig, and LookBack APT groups.
Twelve ransomware groups also exploit this vulnerability.
CVE-2021-34523 [RCE, PE, WebApp, Other]
CVE-2021-34523 affects five Microsoft Exchange products.
It is a critical-severity vulnerability with a 9.8 CVSS rating.
The vulnerability is exploited by Conti, LockBit 2.0, Hive, BianLian, AvosLocker, BlackCat, LockFile, Cuba, Karma, LV, BlackByte, and Babuk ransomware groups.
CVE-2021-31207 [RCE, PE, WebApp, Other]
CVE-2021-31207 is Microsoft Exchange Server security feature bypass vulnerability.
It is also a part of the ProxyShell vulnerabilities (CVE-2021-34523, CVE-2021-34473, and CVE-2021-31207).
It is currently exploited by the Hive ransomware group.
- CISA alerted organizations of this vulnerability in the #StopRansomware campaign.

Recent Attacks
Let us look at some of the recent attacks staged by this prolific group.
- Maximum Industries: This manufacturer makes rocket parts for SpaceX. The LockBit gang boasted about stealing 3,000 proprietary schematics as well as other blueprints in an attack in mid-March 2023.
- Essendant: A wholesale distributor of office goods had a significant cyber attack in March 2023. The LockBit group claimed responsibility on March 14.
- Housing Authority of the City of Los Angeles (HACLA): The state-chartered agency providing affordable housing to low-income individuals and families for the City of Los Angeles, warned of a cyber incident that was later attributed to the LockBit ransomware group.
- Aguas do Porto: A Portuguese municipal water utility company, Aguas do Porto, was hit by the ransomware group in February 2023. The company manages full water cycles inclusive of water supply and waste water drainage, public lighting and photovoltaic parks.
- Royal Mail: In early January 2023, the LockBit ransomware group breached systems of UK’s leading mail delivery service, Royal Mail, that led to disruption of package deliveries.
Whitworth University: A private university in Washington suffered a LockBit ransomware attack in July 2022, and all its operations were halted for over two weeks. The group claimed to have stolen 715 GB of Whitworth data relating to accounting, marketing, infrastructure, and documents.
Italian Revenue Agency: The largest cyberattack was perpetrated on the Italian Revenue Agency by the LockBit gang in July 2022. In this attack, 78 GB worth of data was stolen from the agency’s servers. There are ongoing talks between the revenue agency and LockBit gang regarding ransom payments.
Entrust: Security giant, Entrust’s network was breached in June 2022 and sensitive data was stolen by the LockBit ransomware gang. In an interesting twist, Entrust deployed Denial-of-Service malware on LockBit’s servers preventing them from releasing the stolen data.
Library Lending App, Onleihe: The online library faced an operational dysfunction after the service provider, EKZ, became a victim of a cyberattack in March 2022. Several affiliated websites, statistics pages, catalog data, and ID-Deliveries were impacted in the attack. There is no credible information on what data was stolen in the attack.
Accenture: LockBit attacked Accenture in August 2021 and demanded $50 million as ransom. During this attack, some proprietary information was stolen and released on LockBit’s leak site. For a detailed analysis of the attack, check out our blog on how the Accenture attack unfolded.
New Variants
LockBit started out as an ABCD cryptovirus in 2019. LockBit’s primary targets were private enterprises and government organizations in the United States, China, India, Indonesia, Ukraine, and Europe with cryptocurrency as the demanded ransom. In 2019 and 2020, Windows systems in healthcare and financial institutions bore the brunt of LockBit attacks. The ransomware group then took a brief hiatus to work on their malware kit and improve their operations. Thus far, two other LockBit versions have been released with attack methodologies superior to the preceding ones.
LockBit Version 2.0
LockBit version 2.0 was released in June 2021 and was used for attacks in Chile, Taiwan, and the UK. In this version, LockBit introduced the double extortion technique and automatic encryption of devices across Windows domains. In October 2021, LockBit began infiltrating Linux servers as well, targeting ESXi servers.
LockBit Version 3.0 (also known as LockBit Black)
In June 2022, LockBit released yet another upgraded version of its ransomware with a bug bounty program, Zcash payments, and new extortion tactics. The new version derives from other ransomware such as BlackMatter and DarkSide and has anti-analysis techniques to evade detection, passwordless execution, and an inbuilt command-line argument feature.
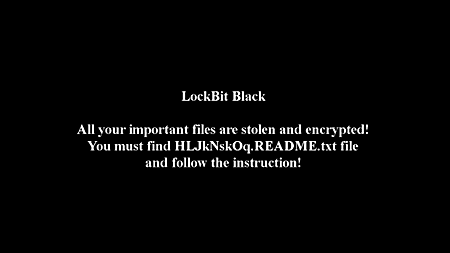
A desktop wallpaper applied by LockBit 3.0 on a victim’s system
This new version of the ransomware was used in attacks on the Italian Revenue Agency and a county office in Ontario, Canada. In this version, LockBit included Denial-of-Service attacks as a method in addition to encryption and data leaks.
In September 2022, an allegedly disgruntled developer leaked the build for LockBit 3.0’s encryptor on Twitter. The developer was reportedly unhappy with the group’s leadership and leaked the private data. This was a blow to the ransomware group, as the builder data allows anyone to start their own ransomware kit with an encryptor, decryptor, and specialized tools to launch the decryptor.
Update:
Based on the leaked builder, Bl00dy ransomware gang developed encryptors and used them in an attack on an Ukrainian entity in September 2022.
How Dangerous is LockBit Ransomware?
Being one of the most active ransomware groups today, LockBit has a variety of tactics and technologies to attack the biggest agencies in any industry. Here are some tools, techniques, and procedures that make LockBit a dangerous adversary:
The threat gang introduced StealBit, a malware tool used for encryption in the LockBit 2.0 version. It is believed to be the fastest and most efficient encryption tool. In the latest version, its encryption techniques have been enhanced further.
StealBit automatically spreads to other devices in the network, using tools like Windows PowerShell and Server Message Block (SMB), which makes it difficult to confine immediately.
LockBit attacks both Windows and Linux systems with malware. Initially, they had targeted only Windows systems, but LockBit 2.0 was improvised to attack Linux systems as well.
Their evasion tactics are well strategized, making it hard to get flagged by system’s defenses.
LockBit conducts bug bounty programs to improve their defenses and establish that they are professional hackers. Anyone who finds a flaw in their malware kit is rewarded generously.
This ransomware group actively markets to affiliates to join them and carry out attacks. These marketing activities have garnered quite the attention and work well for the group in getting highly-skilled threat actors.
LockBit 3.0 introduced ZCash payment options for collecting ransoms from victims, paying their affiliates, and transacting with less disruption from law enforcement.
LockBit is known for its double extortion technique wherein they steal data and also encrypt the system data making it harder for victims to recover it.
In August 2022, LockBit announced that it would use triple extortion on its victims via data leaks, encryption, and DDoS attacks.
LockBit 3.0 also checks the victim’s UI language before carrying out an attack. They avoid infecting systems with the following languages:
- Arabic (Syria)
- Armenian (Armenia)
- Azerbaijani (Cyrillic Azerbaijan)
- Azerbaijani (Latin Azerbaijan)
- Belarusian (Belarus)
- Georgian (Georgia)
- Kazakh (Kazakhstan)
- Kyrgyz (Kyrgyzstan)
- Romanian (Moldova)
- Russian (Moldova)
- Russian (Russia)
- Tajik (Cyrillic Tajikistan)
- Turkmen (Turkmenistan)
- Tatar (Russia)
- Ukrainian (Ukraine)
- Uzbek (Cyrillic Uzbekistan)
- Uzbek (Latin Uzbekistan)
A notable tactic of the third version of LockBit includes a file deletion technique, where instead of using cmd.exe to execute a batch file to perform the deletion, the group drops and executes a .tmp file decrypted from the binary.
Updates:
- Exfiltrator-22: A new attack framework was created by affiliates of the former LockBit 3.0 operation that includes features found commonly in other post-exploitation toolkits, but has added features that enhance ransomware deployment and data theft. The EX-22, as it is referred to, is designed to spread ransomware quickly in corporate networks while evading detection.
- The LockBit ransomware group started a campaign in early January 2023, that used combinations of techniques effective against AV and EDR solutions.
- In a recent campaign, the LockBit gang introduced a new method to allow it to exfiltrate data from high-profile organizations by bypassing the Mark of The Web (MOTW) protection mechanism.
How Does LockBit Ransomware Attack?
LockBit has undergone three version revisions; the latest version uses sophisticated attack techniques. Let us take a look:
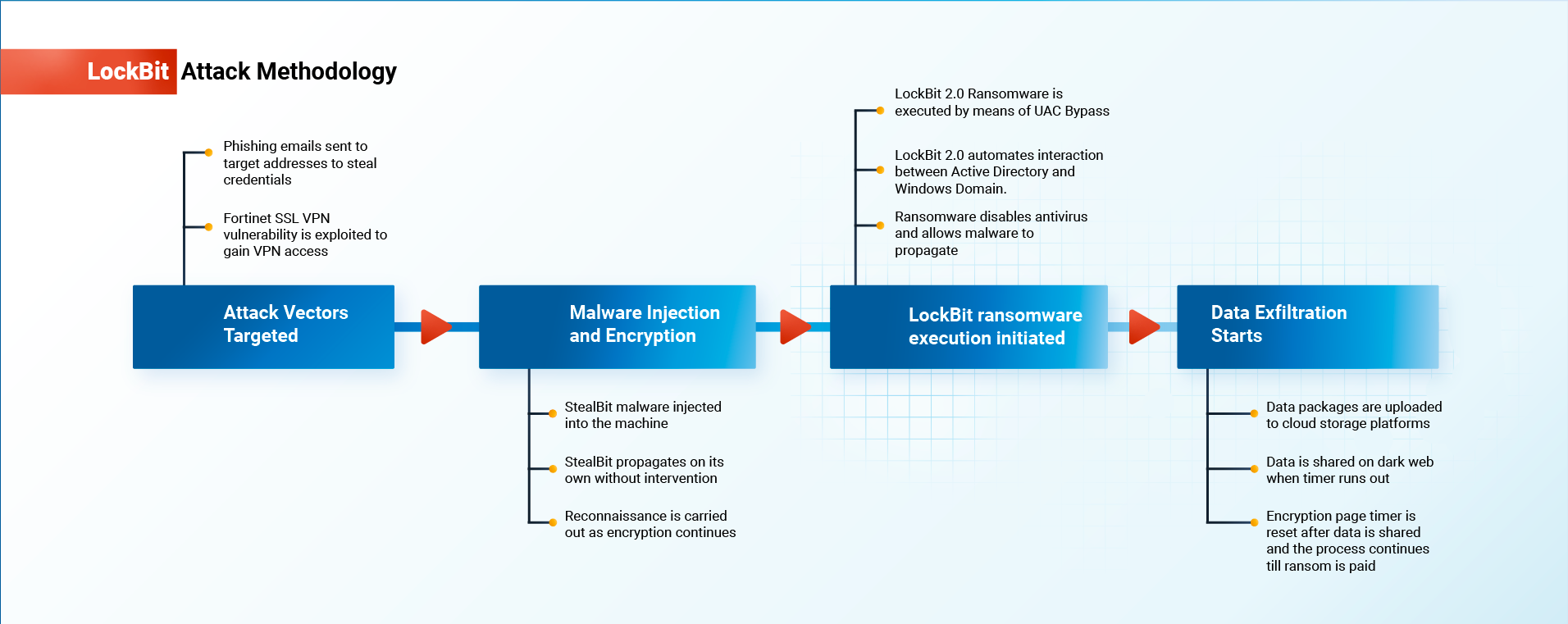
LockBit 2.0 Attack Methodology
LockBit Ransomware MITRE ATT&CK Techniques and Sub-Techniques
How to Detect LockBit Ransomware in your Environment
How Do Organizations Prevent a LockBit Attack?
Patch CVEs
More often than not, attackers infiltrate networks and gain access to systems via known, unpatched vulnerabilities. Follow advisories from your vendors and the CISA KEV advisories to patch all CVEs at the earliest. To stay ahead of attackers, follow advisories pertaining to CVEs critical to your organization.
Set strong passwords
Hackers can break into critical systems that do not implement complex passwords. It is essential that everyone accessing the network enables strong passwords and multi-factor authentication (MFA) to secure their logins.
Remove unnecessary permissions
Increase the amount of restrictions on permissions to prevent potential dangers from being ignored. Pay specific attention to those accessible by IT accounts with admin-level permissions and endpoint users.
Be vigilant while handling links
Social engineering techniques such as phishing emails are one of the most common methods incorporated by ransomware groups to gain access for malware distribution. Clicking unknown links is always ill-advised.
Keep tabs on your attack surface
Employ a solution that can scan your entire attack surface for weaknesses. Know and keep tabs on known and unknown devices connected to your broader network.
Organizations can keep attackers at bay by staying vigilant and ensuring that the above steps are strictly followed. A good way to do this is to employ an automated system that regularly scans for vulnerabilities and loopholes, and alerts the Chief Information Security Officers.
Are you unsure of how to check for ransomware vulnerabilities in your network? Afraid that attackers might find a way into your network? Talk to a Securin to help you identify vulnerabilities in your attack surface & prioritize them for remediation.
Download our Ransomware Spotlight Report 2023 to stay updated on the latest developments in ransomware vulnerabilities and prevention.










