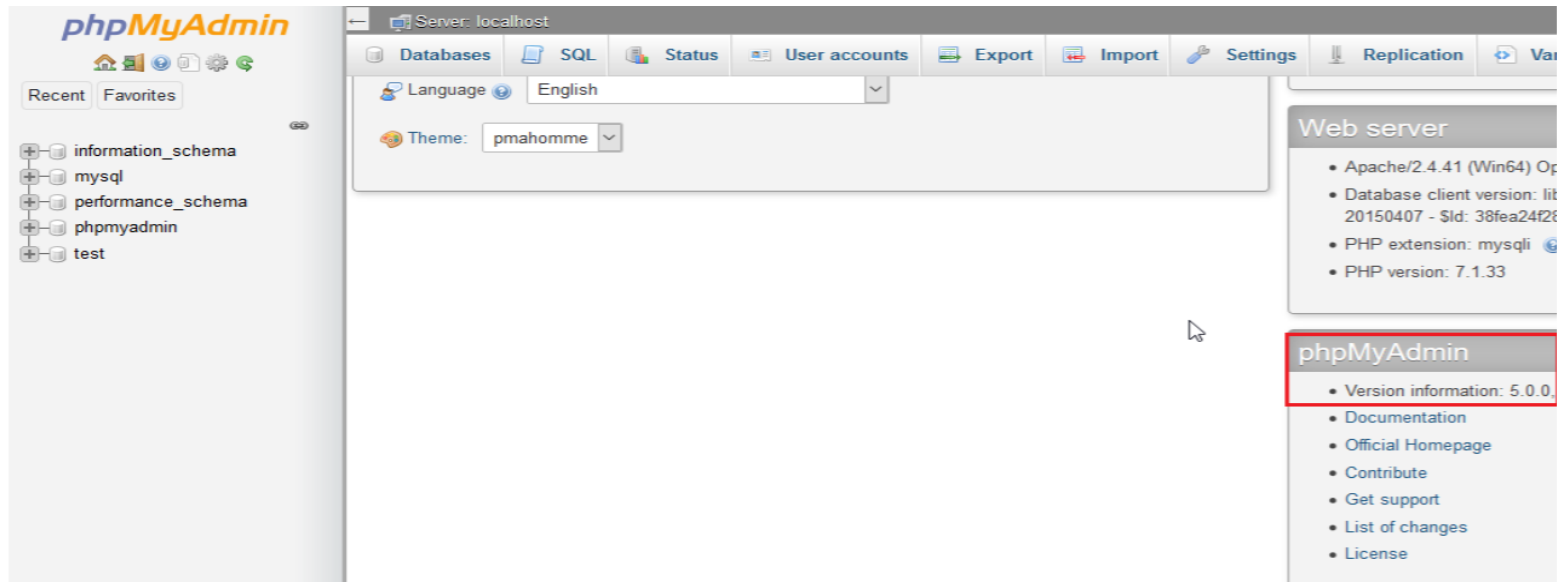
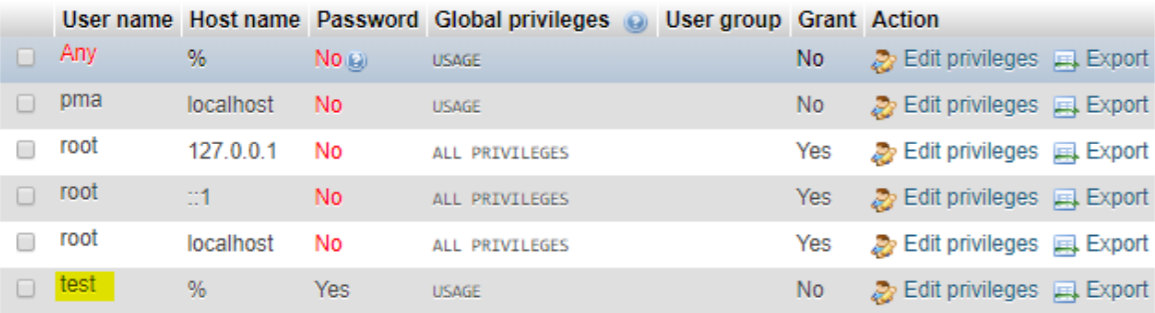
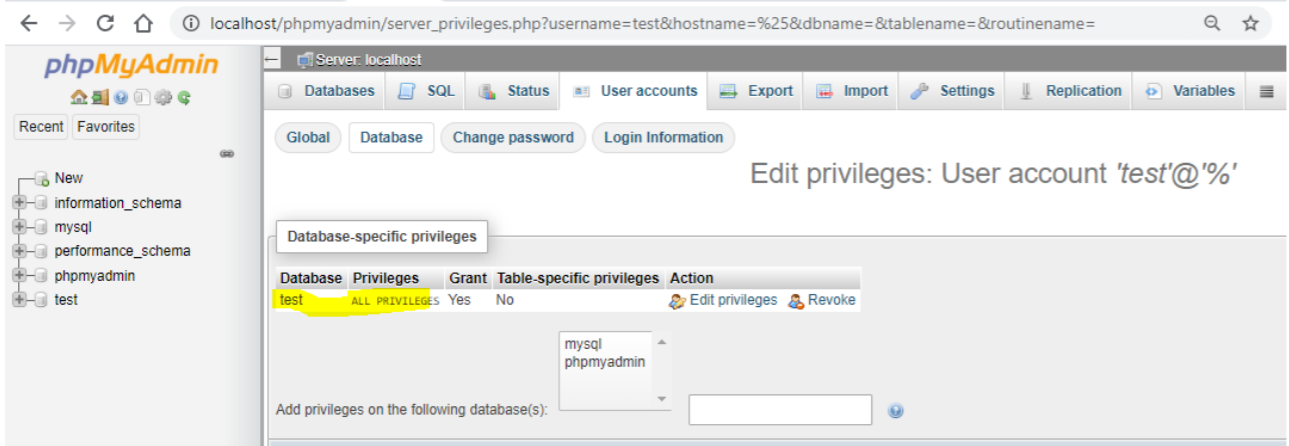
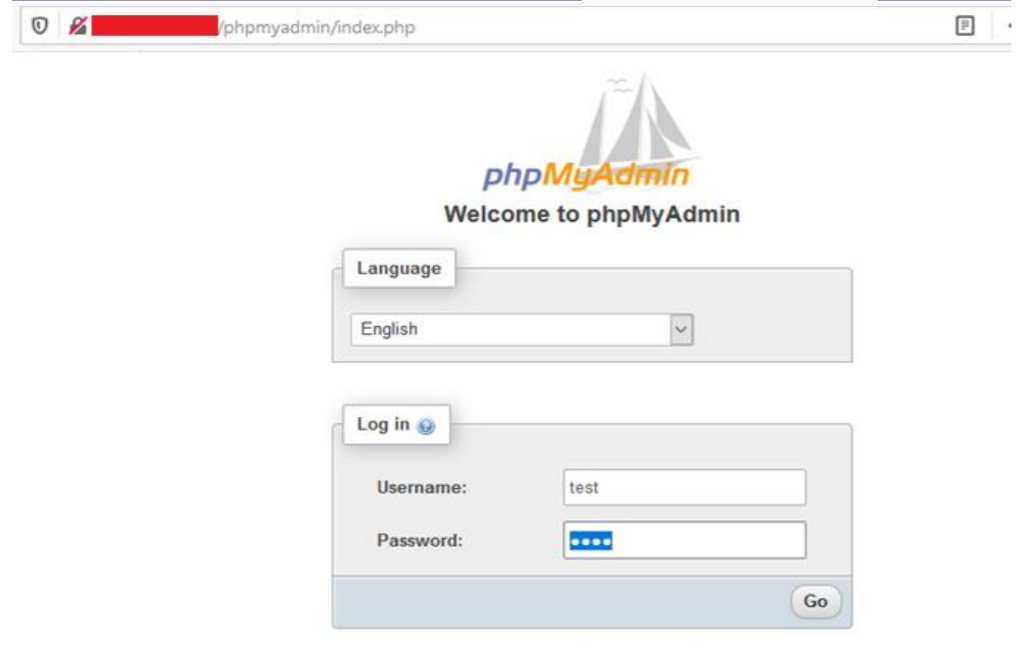
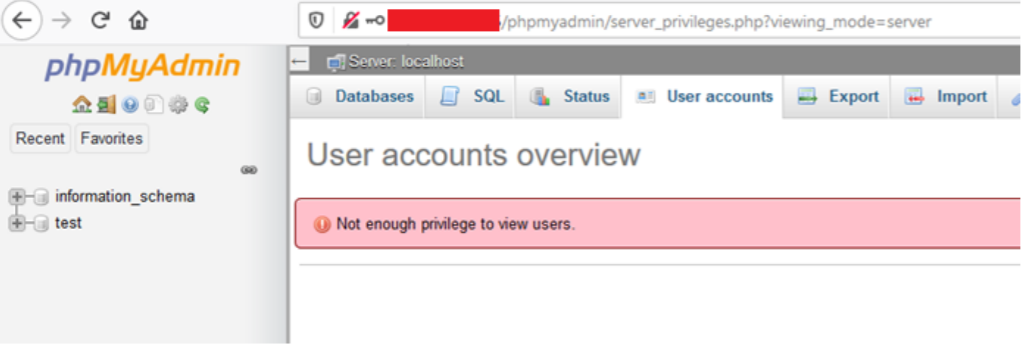
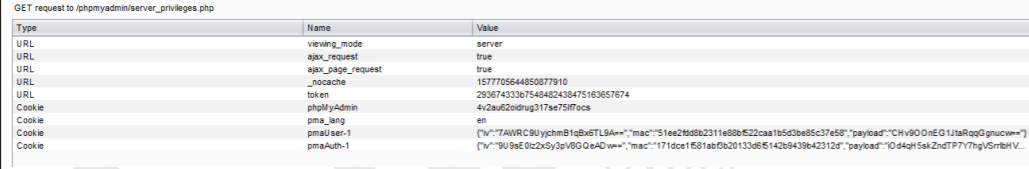
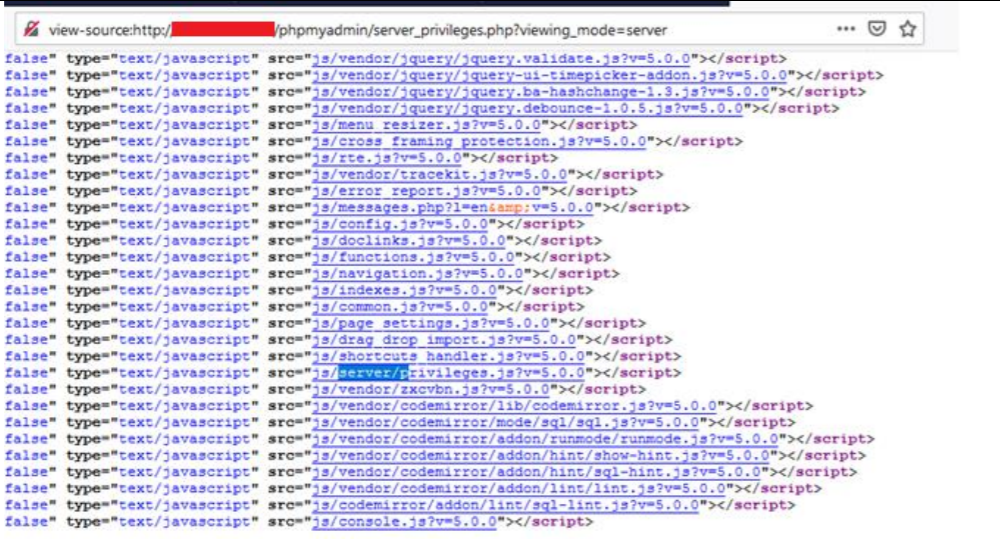
A SQL injection (SQLi) refers to an injection attack wherein an attacker can execute malicious SQL statements that control a web application’s database server. Missing functional level access flaws allow attackers to access unauthorized functionality. SQL injection (SQLi) vulnerability was identified with the conjunction of missing function level access in the latest version of the phpMyAdmin database. The vulnerability affects http://localhost/phpmyadmin/server_privileges.php, username.
-
Products
Our ASM platform discovers, analyzes, prioritizes, & offers remediation plans for exposures in your known & unknown assets.
Our VI platform delivers threat intelligence & context on the latest cyber threats providing you with actionable insights for remediation.
-
Services

Our vulnerability management continually detects, prioritizes, & plans remediation to protect your entire IT landscape.

Our penetration testing simulates a real-world attack on your digital assets to determine the strength of your security & defenses.
-
Use Cases
- Attack Surface Management
- Continuous Attack Surface Reduction
- Discovery of Known & Unknown Assets
- Assets with Known Ransomware and Exploitable Vulnerabilities
- Non-Production Systems Exposed to the Public
- Monitor Subsidiaries & Acquisitions
- Vulnerability Intelligence
- Early Warning Risk Alerts
- Vulnerability Prioritization
- Tech Stack Alerting
- Actionable Threat Intelligence
- Penetration Testing
- Network & Infrastructure Penetration Testing
- Meet your Compliance Requirements
- Test Your Security Resilience
- Protect Intellectual Property
- Vulnerability Management
- Manage Vulnerabilities & Exposures
- Network & Application Vulnerability Management
- Threat & Vulnerability Advisories
- Vulnerability Validation & False Positive Elimination

-
Partners

As a partner led organization, we are committed to working with our partners to deliver world-class early warning security intelligence solutions that eliminate the adversary advantage & deliver superior security outcomes for your clients.
- Resources
-
About