The growing backlog of vulnerabilities awaiting analysis at the NVD is attracting a lot of attention. Securin’s analysts took a deep dive into the problem. Here’s what we found, and what it means for your organization.
What’s up with NVD?
Since February, a slowdown at the NVD has caused a growing backlog of vulnerabilities submitted and requiring analysis. The reasons for the delay include increasing numbers of software to be analyzed and a change in interagency support. Whatever the causes, it’s fair to say that the knock-on effects for cybersecurity in general and vulnerability management in particular are significant.
The threat research team at Securin took a deep dive into the problem. Here’s what we found – and what it means for anyone tasked with protecting their organization from cyberattacks.
CVEs: More Data, More Gaps, More Problems
The number of CVEs published every year has increased almost 2x in five years. Reasons for this include:
- Increasing complexity of software and technology systems
- Expanding threat landscape
- Heightened security awareness
- Improved vulnerability and reporting mechanisms
In theory, all of this is good news. The more vulnerabilities we detect, the better prepared we can be, right? The reality is that more data can bring more challenges for vulnerability management, as organizations struggle to understand, prioritize and address the growing volumes of vulnerabilities effectively.
Unintended end result: potential for leaving critical systems exposed to exploitation. The growing number of CVEs bring welcome visibility to security issues, the challenges however arise from incomplete data points required for CVE analysis & prioritization.
So what are these missing data points and why is context so important in vulnerability management? Let’s take a look.
1. The CPE Problem: Missing Context
When it comes to vulnerability analysis, prioritization and mitigation, context is everything. With high volumes of CVEs and increasing complexity, context is key to understanding where to focus your attention and which threats require the most immediate mitigation. That’s where CPE comes in.
CPE, or Common Platform Enumeration, structures IT systems, software, and packages affected by a CVE. It offers vital context for understanding vulnerability impact.. Vulnerability scanners use CPE to detect affected assets and configurations, crucial for prioritizing and remediating security risks. Without it, organizations risk inefficient vulnerability management, leaving systems and data vulnerable to exploitation.
Here are some of the issues the Securin team has uncovered:
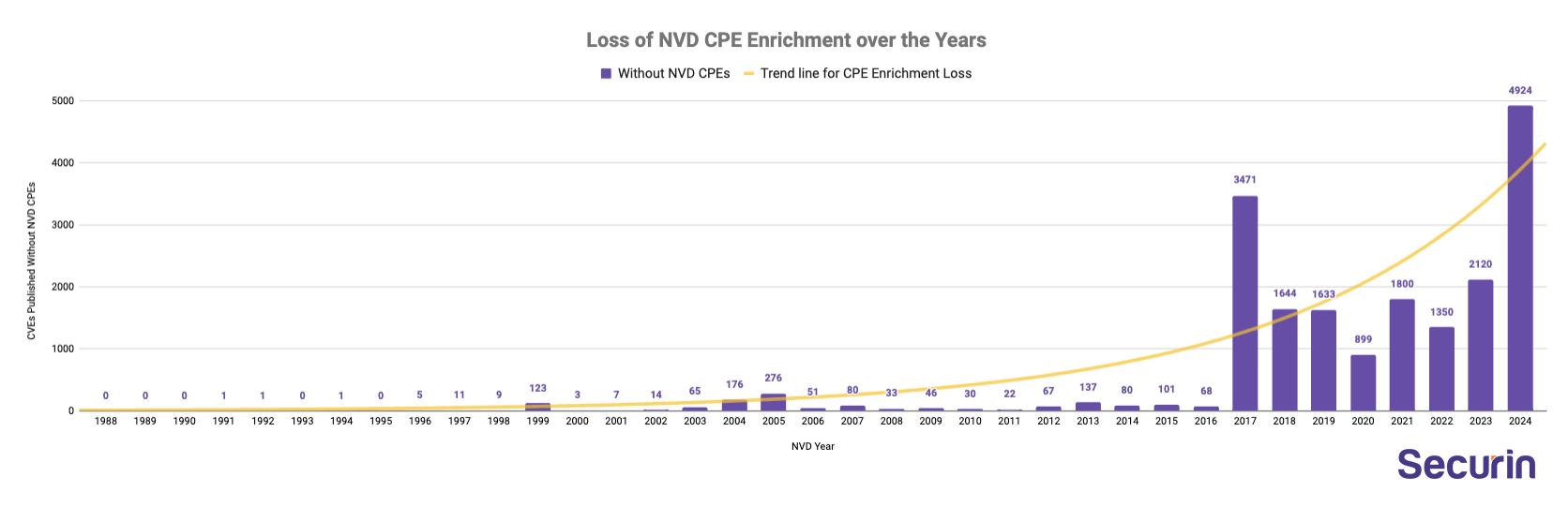
- Big chunk of information missing: 19,248 CVEs published on NVD lack CPE data. (~8% of all time published CVEs)
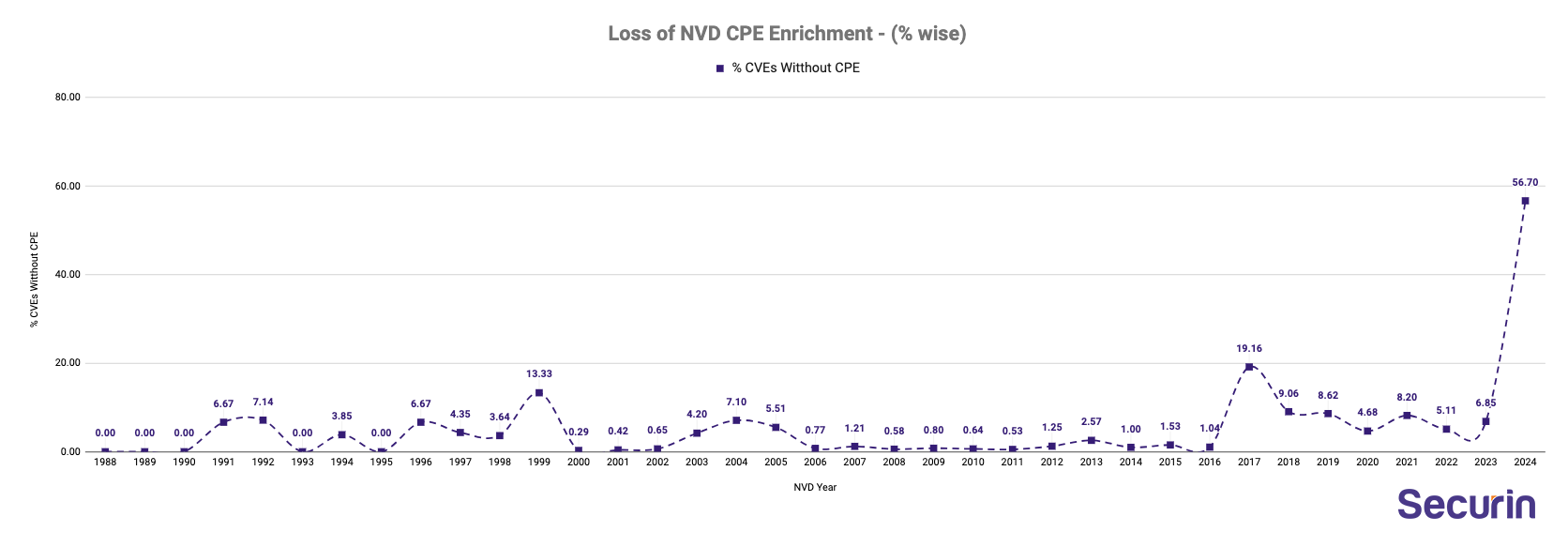
- Increasing Trend in loss of CPE enrichment: The increasing struggles of NVD are evident as the % of CVEs without CPEs has been on an upward trend, all the while the number of CVEs published has surged.
- The surge reached a dramatic peak in 2024, with over 56.7% CVEs published lacking CPE enrichment. (4924 of 8685 CVEs).
2. CVSS Score & Metrics: Critical Insights Into Impact
The Common Vulnerability Scoring System (CVSS) is a method for supplying a qualitative measure of threat severity. It’s not a measure of risk; while all vulnerability management programs discard CVSS scores, metrics such as Attack Vector, User Interaction, Attack Complexity, Privileges Required and CIA triad provide critical insights into the severity and potential impact of vulnerabilities. Moreover, several vendors continue to use CVSS scores as the base of their own enhanced scoring system.
The Securin team found some significant, urgent gaps in the data here:
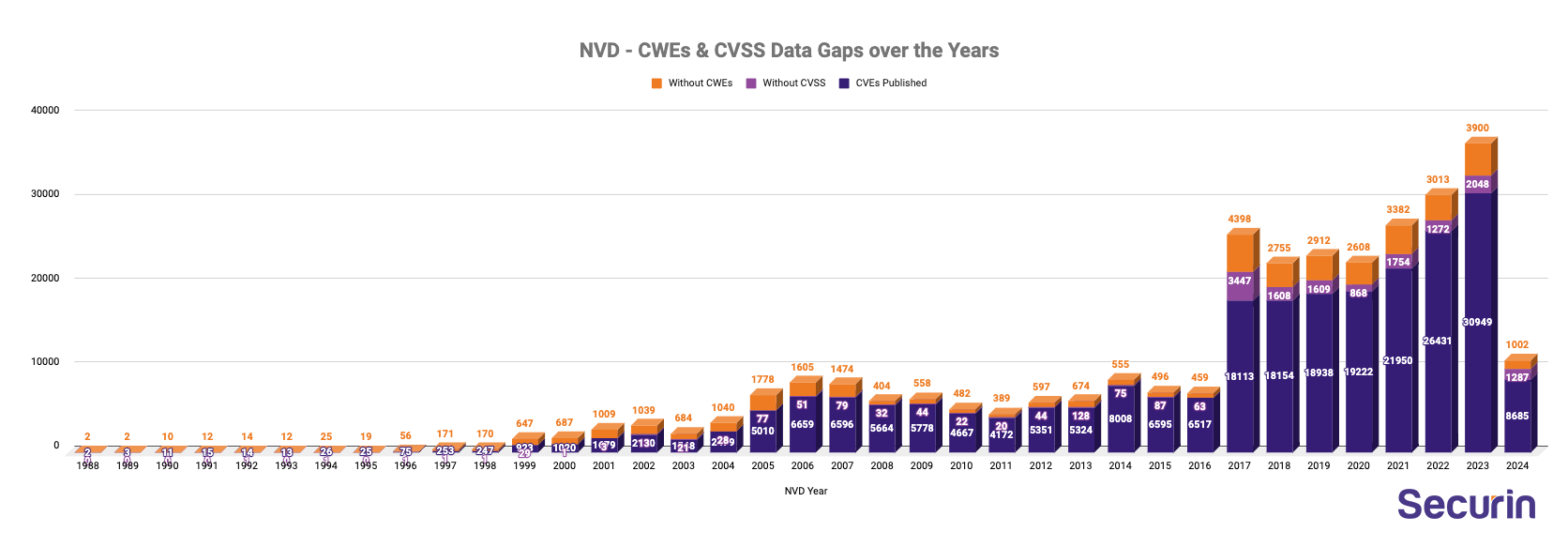
- Across NVD, 14,715 CVEs are missing CVSS data. What’s more concerning is that 94% of these CVEs are from 2017-present. CVSS analysis is a pressing gap that is widening rapidly.
3. Weaknesses/CWEs: Getting to the Root of the Threat
Common Weakness Enumeration (CWE) categorizes common flaws or weaknesses in software and hardware that can lead to vulnerabilities. These provide crucial contextual information about the underlying root case, helping security professionals understand the originating factors of the issue, potential attack vectors, and appropriate mitigation strategies.
These relationships enhance the accuracy of vulnerability assessments, facilitate prioritization of security measures, and help developers adopt a proactive stance to early detection & mitigation of security issues.
Securin’s analysts observed some concerning gaps in CWEs:
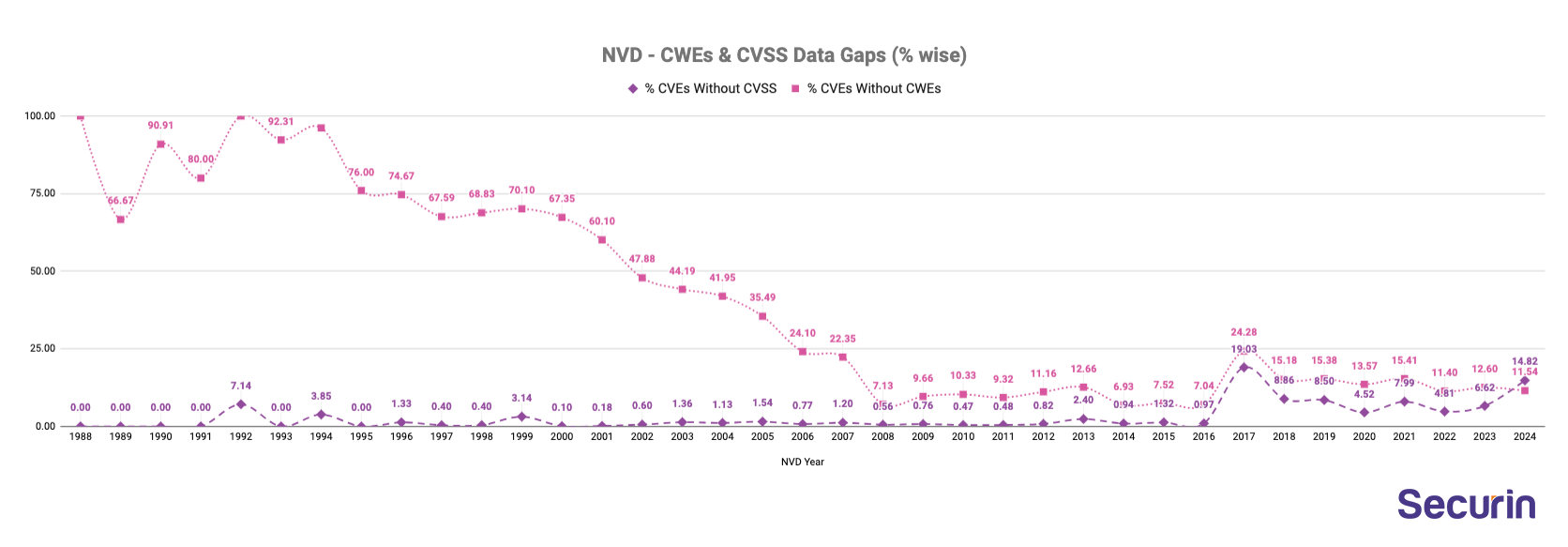
- 16% of all time NVD CVEs missing CWEs is a cause of concern.
- The percentage of CVEs without CWEs varies over the years but generally shows a decreasing trend.
- However since 2017, 23,970 CVEs are missing CWE assignment; including 53 CISA’s Known Exploited Vulnerabilities.
Summary of the Challenges:
- Without CPEs, the impact of vulnerabilities cannot be discovered, let alone prioritized. Vulnerability scanners depend on CPE data to discover products and map CVEs to them. It complicates the accurate assessment of system vulnerabilities and the implementation of effective mitigation strategies become significantly compromised, leaving organizations at heightened risk of security breaches and potential exploitation.
- CVSS metrics & CWEs play an important role in mapping CVEs to MITRE ATT&CK, which help identify vulnerabilities that allow attacker tactics such as initial access, privilege escalation & execution. The lack of this data hinders our ability to identify the positioning of CVEs across the MITRE ATT&CK Kill Chain.
Plugging the Gaps: Securin VI vs NVD
Securin’s threat research teams continue to analyze, observe and generate data to augment and enrich vulnerability data to ensure maximum coverage and accuracy for our users. Here are some of the areas where our coverage enhances visibility and reduces vulnerability.
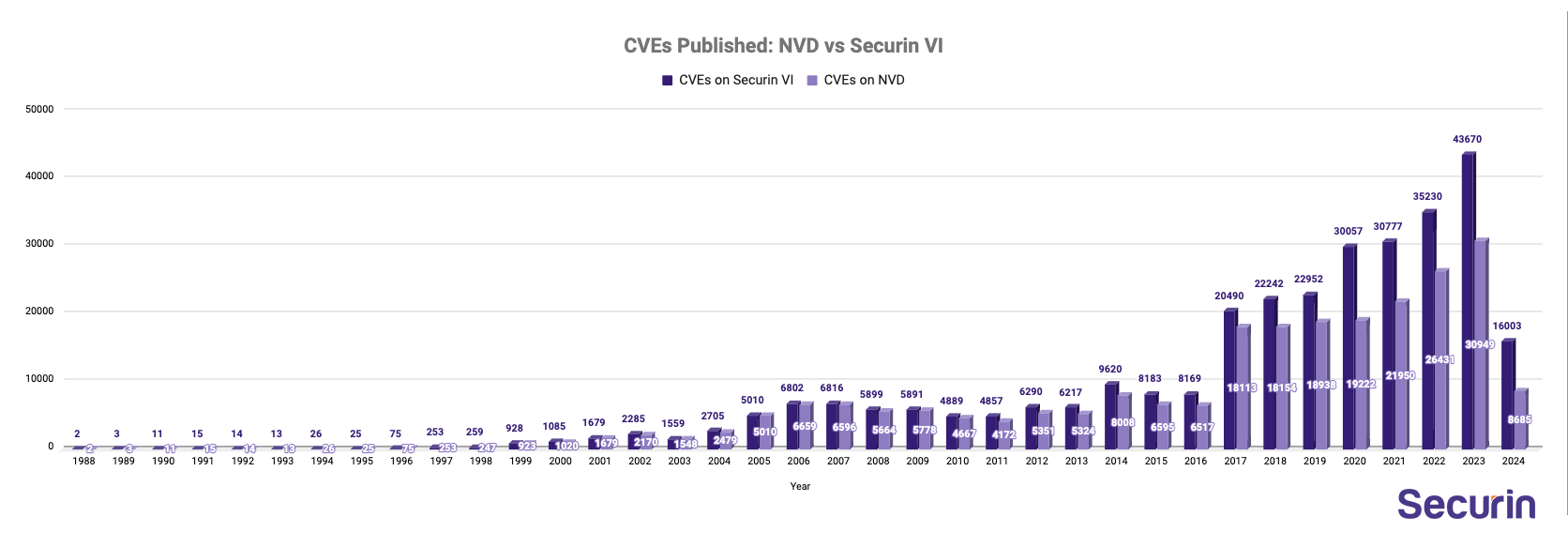
1. CVE Coverage:
While we’ve talked about the data handicaps with NVD, another perspective is the incomplete coverage of NVD in aggregating CVEs. Without the complete visibility of vulnerabilities and associated risk, organizations are left vulnerable to cyber threats, increasing the likelihood of security breaches and potentially compromising sensitive data and systems.
Key statistics:
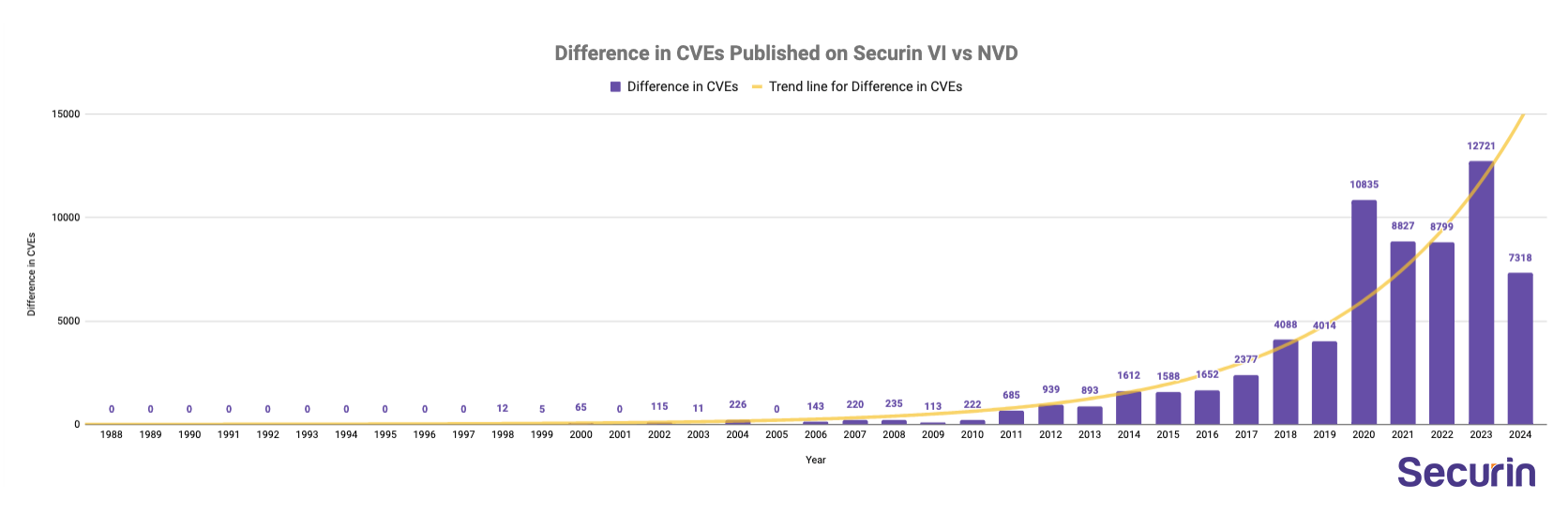
- Securin VI has 311,001 CVEs compared to NVD’s 243,286 CVEs. 27% better coverage.
- In the last 10 years, Securin VI has been covering on average 6221 more CVEs per year compared to NVD.
- In 2024, Securin VI has almost twice the CVE coverage. 16003 vs 8685, an indicator of NVD’s struggles this year.
2. CPE Enrichment by Securin VI
Securin VI aggregates data from diverse sources. While NVD emerges as the primary CVE reference, providing invaluable insights. In instances where CPEs are absent, our platform analyzes alternative sources for vendor/product names or packages.
Key statistics:
- In 2024 so far, Securin VI has affected products/packages information for 1468 CVEs lacking CPE data on NVD; 17% better CPE enrichment than NVD.
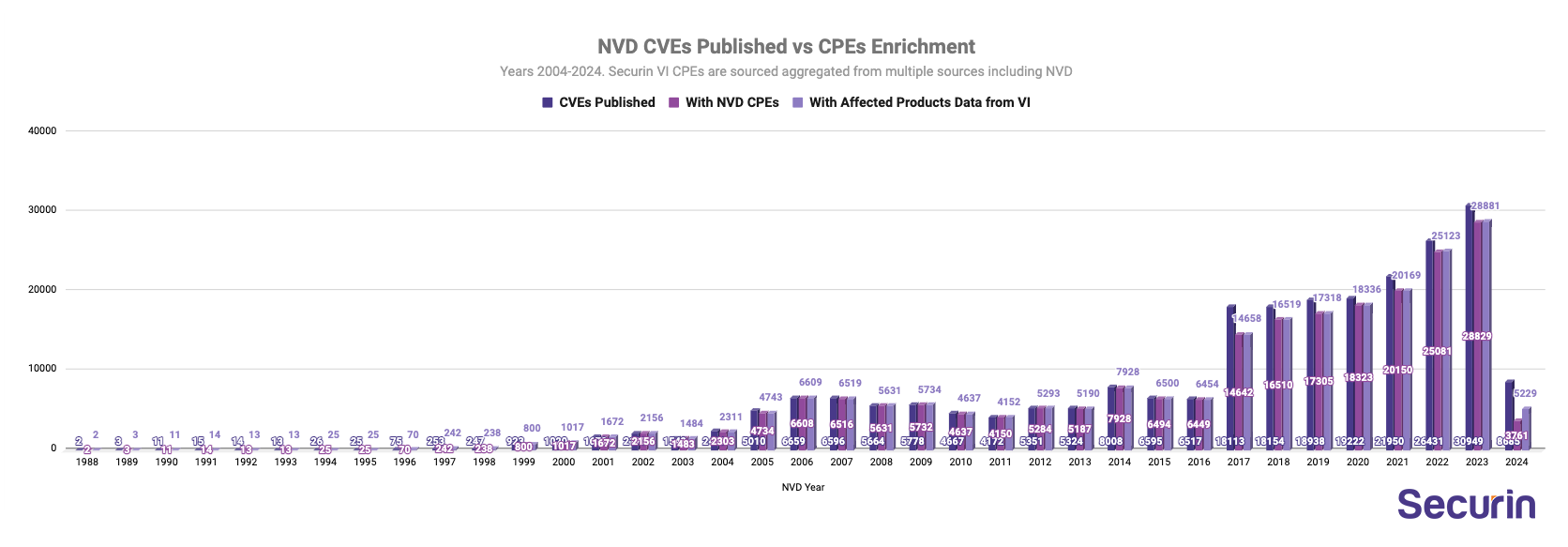
NVD’s shortcomings, including missing enrichment data on over 3,000 recent CVE entries, hinder cybersecurity efforts by depriving researchers and security teams of crucial bug details. This gap in vital information undermines vulnerability management strategies, potentially leaving organizations more vulnerable to cyberattacks. We’re optimistic that the NVD will return to business-as-usual soon. Until then, Securin’s researchers will continue to plug the gaps and augment the data and insights our customers need to mitigate risk and manage vulnerabilities.









